CLI example: Configuring account login audit
Network configuration
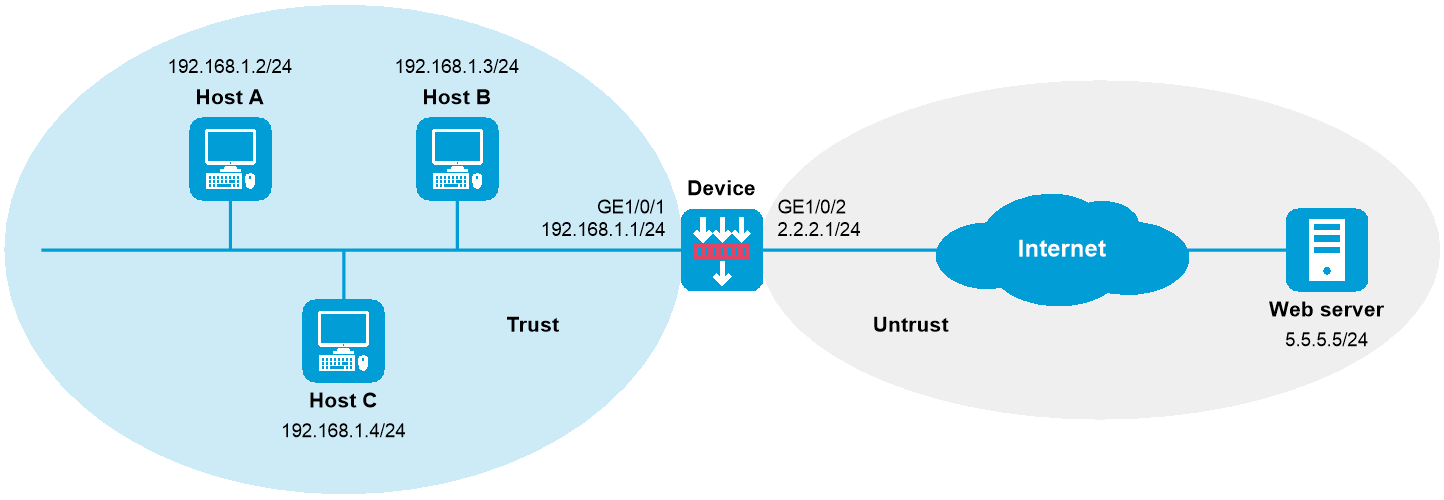
As shown in Figure-1, all departments of a company access the Internet through the device. The working hours of the company are 8:00:00 through 18:00:00 from Monday to Friday.
Configure an application audit and management policy on the device to meet the following requirements:
Software versions used
This configuration example was created and verified on R9900P2705 of the F5000-AI-55-G device.
Procedures
Assign IP addresses to interfaces:
# Assign an IP address to interface GigabitEthernet 1/0/1.
<Device> system-view
[Device] interface gigabitEthernet 1/0/1
[Device-GigabitEthernet1/0/1] ip address 192.168.1.1 255.255.255.0
[Device-GigabitEthernet1/0/1] quit
# Assign IP addresses to other interfaces in the same way. (Details not shown.)
Configure settings for routing.
This example configures static routes, and the next hop in the routes is 2.2.2.2.
[Device] ip route-static 5.5.5.5 24 2.2.2.2
Add interfaces to security zones.
[Device] security-zone name trust
[Device-security-zone-Trust] import interface gigabitEthernet 1/0/1
[Device-security-zone-Trust] quit
[Device] security-zone name untrust
[Device-security-zone-Untrust] import interface gigabitEthernet 1/0/2
[Device-security-zone-Untrust] quit
Configure a security policy:
# Configure a rule named
trust-untrust to allow the host to access the Internet.[Device] security-policy ip
[Device-security-policy-ip] rule name trust-untrust
[Device-security-policy-ip-1-trust-untrust] source-zone trust
[Device-security-policy-ip-1-trust-untrust] destination-zone untrust
[Device-security-policy-ip-1-trust-untrust] source-ip-host 192.168.1.2
[Device-security-policy-ip-1-trust-untrust] source-ip-host 192.168.1.3
[Device-security-policy-ip-1-trust-untrust] source-ip-host 192.168.1.4
[Device-security-policy-ip-1-trust-untrust] action pass
[Device-security-policy-ip-1-trust-untrust] quit
[Device-security-policy-ip] quit
Configure a time range named
work to cover 8:00:00 through 18:00:00 from Monday to Friday.[Device] time-range work 08:00 to 18:00 working-day
Update the APR signature library to the latest version (in this example, 1.0.183). (Details not shown.)
Configure an application audit and management policy:
# Enter application audit and management view.
[Device] uapp-control
# Create an audit policy named
audit-qq and enter its view.[Device-uapp-control] policy name audit-qq audit
# Configure source security zone
Trust as a match criterion for audit policyaudit-qq .[Device-uapp-control-policy-audit-qq] source-zone trust
# Configure destination security zone
Unt rust as a match criterion for audit policyaudit-qq .[Device-uapp-control-policy-audit-qq] destination-zone untrust
# Specify time range
work for audit policyaudit-qq .[Device-uapp-control-policy-audit-qq] time-range work
# Configure an audit rule to permit login from all QQ accounts and generate audit logs.
[Device-uapp-control-policy-audit-qq] rule 1 app QQ behavior Login bhcontent any keyword equal any action permit audit-logging
[Device-uapp-control-policy-audit-qq] quit
[Device-uapp-control] quit
# Activate the configuration.
[Device] inspect activate
Verifying the configuration
When QQ accounts attempt to access the Internet, the device permits the login requests and generates audit log messages.
Configuration files
#
interface GigabitEthernet1/0/1
ip address 192.168.1.1 255.255.255.0
#
interface GigabitEthernet1/0/2
ip address 2.2.2.1 255.255.255.0
#
security-zone name Trust
import interface GigabitEthernet1/0/1
#
security-zone name Untrust
import interface GigabitEthernet1/0/2
#
ip route-static 5.5.5.0 24 2.2.2.2
#
time-range work 08:00 to 18:00 working-day
#
uapp-control
policy name audit-qq audit
rule 1 app QQ behavior Login bhcontent any keyword equal any action permit audit-logging
time-range work
source-zone trust
destination-zone untrust
#
inspect activate
#
security-policy ip
rule 0 name trust-untrust
action pass
source-zone trust
destination-zone untrust
source-ip-host 192.168.1.2
source-ip-host 192.168.1.3
source-ip-host 192.168.1.4
#