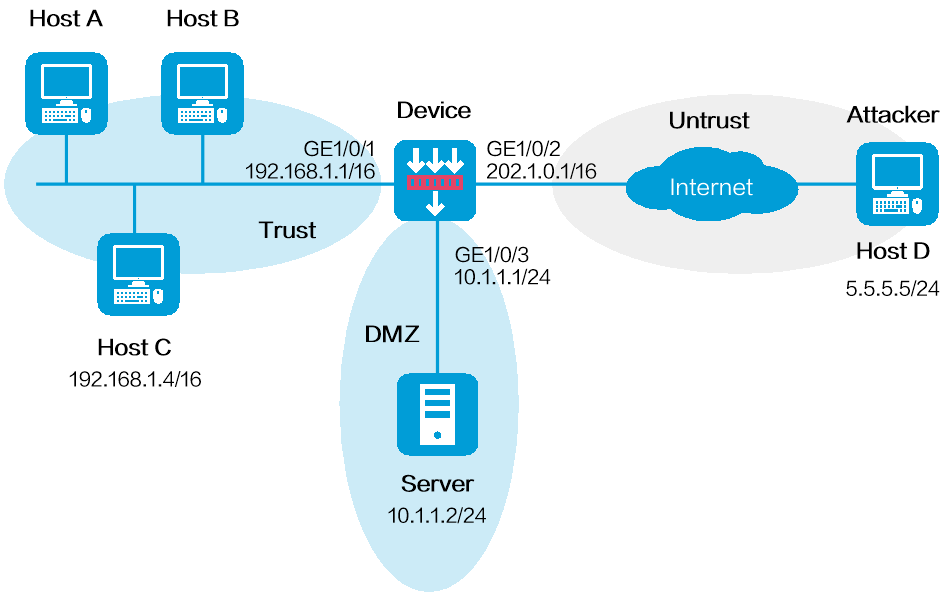
As shown in Figure 1, configure source IP blacklist entries on the device to block packets from the attacker Host D permanently and from Host C for 50 minutes.
This configuration example was created and verified on F9900 of the F5000-AI120 device.
Assign IP addresses to interfaces:
Assign an IP address to interface GigabitEthernet 1/0/1.
<Device> system-view
[Device] interface gigabitethernet 1/0/1
[Device-GigabitEthernet1/0/1] ip address 192.168.1.1 255.255.0.0
[Device-GigabitEthernet1/0/1] quit
# Assign IP addresses to other interfaces in the same way. (Details not shown.)
Add interfaces to security zones.
[Device] security-zone name trust
[Device-security-zone-Trust] import interface gigabitethernet 1/0/1
[Device-security-zone-Trust] quit
[Device] security-zone name untrust
[Device-security-zone-Untrust] import interface gigabitethernet 1/0/2
[Device-security-zone-Untrust] quit
[Device] security-zone name dmz
[Device-security-zone-DMZ] import interface gigabitethernet 1/0/3
[Device-security-zone-DMZ] quit
Configure a security policy:
# Configure a rule named trust-untrust to allow hosts in security zone trust to access the Internet.
[Device] security-policy ip
[Device-security-policy-ip] rule name trust-untrust
[Device-security-policy-ip-1-trust-untrust] source-zone trust
[Device-security-policy-ip-1-trust-untrust] destination-zone untrust
[Device-security-policy-ip-1-trust-untrust] source-ip-subnet 192.168.0.0 16
[Device-security-policy-ip-1-trust-untrust] action pass
[Device-security-policy-ip-1-trust-untrust] quit
# Configure a rule named untrust-dmz to allow hosts on the Internet to access the server.
[Device-security-policy-ip] rule name untrust-dmz
[Device-security-policy-ip-2-untrust-dmz] source-zone untrust
[Device-security-policy-ip-2-untrust-dmz] destination-zone dmz
[Device-security-policy-ip-2-untrust-dmz] destination-ip-host 10.1.1.2
[Device-security-policy-ip-2-untrust-dmz] action pass
[Device-security-policy-ip-2-untrust-dmz] quit
[Device-security-policy-ip] quit
Configure the source IP blacklist:
# Add a source IPv4 blacklist entry for Host D.
[Device] blacklist ip 5.5.5.5
# Add a source IPv4 blacklist entry for Host C and set the blacklist entry aging time to 50 minutes.
[Device] blacklist ip 192.168.1.4 timeout 50
# Enable the global blacklist feature.
[Device] blacklist global enable
# Verify that the source IPv4 blacklist entries are successfully added.
<Device> display blacklist ip
IP address VPN instance DS-Lite tunnel peer Type TTL(sec) Dropped
5.5.5.5 -- -- Manual Never 0
192.168.1.4 -- -- Manual 2989 0
# Verify that the device drops packets from Host D. (Details not shown.)
# Execute the undo blacklist ip 5.5.5.5 command and verify that the device forwards packets from Host D. (Details not shown.)
# Verify that the device drops packets from Host C for 50 minutes and forwards packets from Host C after 50 minutes. (Details not shown.)
#
interface GigabitEthernet1/0/1
port link-mode route
ip address 192.168.1.1 255.255.0.0
#
interface GigabitEthernet1/0/2
port link-mode route
ip address 202.1.0.1 255.255.0.0
#
interface GigabitEthernet1/0/3
port link-mode route
ip address 10.1.1.1 255.255.255.0
#
#
security-zone name Trust
import interface GigabitEthernet1/0/1
#
security-zone name DMZ
import interface GigabitEthernet1/0/3
#
security-zone name Untrust
import interface GigabitEthernet1/0/2
#
blacklist ip 5.5.5.5
blacklist global enable
#
security-policy ip
rule 1 name trust-untrust
action pass
source-zone trust
destination-zone untrust
source-ip-subnet 192.168.0.0 255.255.0.0
rule 2 name untrust-dmz
action pass
source-zone untrust
destination-zone dmz
destination-ip-host 10.1.1.2