CLI example: Configuring a zone pair-based packet filter
Network configuration
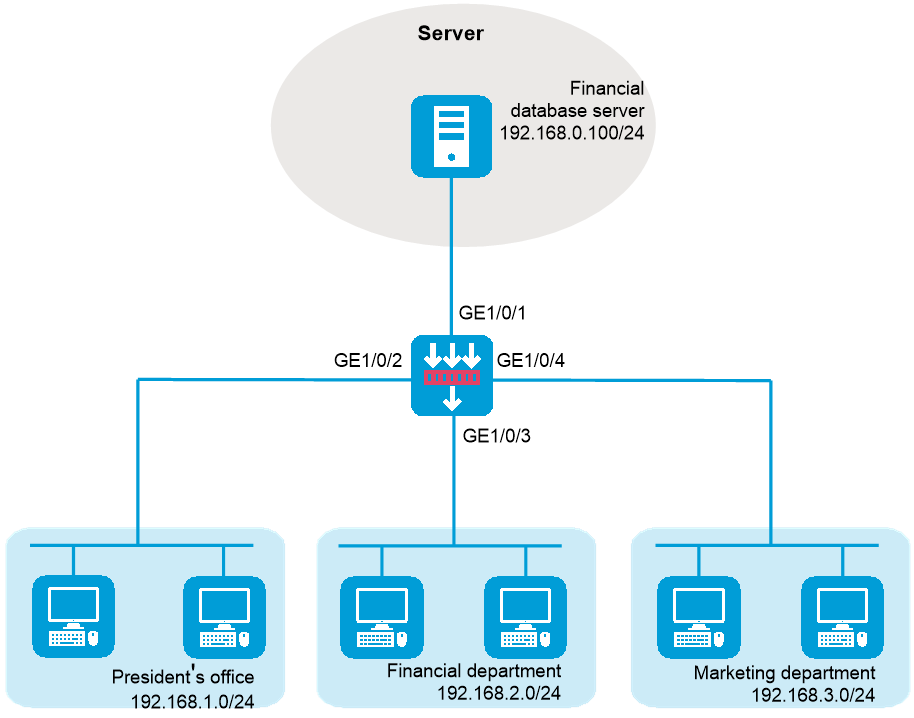
A company interconnects its departments through the device. The financial database server, President's office, Financial department, and Marketing department belong to different security zones. Configure a packet filter to:
Permit access from the President's office at any time to the financial database server.
Permit access from the Financial department to the financial database server only during working hours (from 8:00 to 18:00) on working days.
Deny access from any other department to the financial database server.
Figure-1 Network diagram
Software versions used
This configuration example was created and verified on E9900 of the F5000-AI-55-G device.
Procedure
Assign IP addresses to interfaces:
# Assign an IP address to GigabitEthernet 1/0/1
<Device> system-view
[Device] interface gigabitEthernet 1/0/1
[Device-GigabitEthernet1/0/1] ip address 192.168.0.1 255.255.255.0
[Device- GigabitEthernet1/0/1] quit
# Assign IP addresses to other interfaces in the same way. (Details not shown.)
Add interfaces to security zones.
[Device] security-zone name Server
[Device-security-zone-Server] import interface gigabitEthernet 1/0/1
[Device-security-zone-Server] quit
[Device] security-zone name President
[Device-security-zone-President] import interface gigabitEthernet 1/0/2
[Device-security-zone-President] quit
[Device] security-zone name Finance
[Device-security-zone-Finance] import interface gigabitEthernet 1/0/3
[Device-security-zone-Finance] quit
[Device] security-zone name Market
[Device-security-zone-Market] import interface gigabitEthernet 1/0/4
[Device-security-zone-Market] quit
Create a periodic time range from 8:00 to 18:00 on working days.
[Device] time-range work 08:0 to 18:00 working-day
Configure ACLs:
# Configure ACL 3000 to permit access from the President's office at any time to the financial database server.
[Device] acl advanced 3000
[Device-acl-ipv4-adv-3000] rule permit ip source 192.168.1.0 0.0.0.255 destination 192.168.0.100 0
[Device-acl-ipv4-adv-3000] quit
# Configure ACL 3001 to permit access from the Financial department to the financial database server only during working hours on working days.
[Device] acl advanced 3001
[Device-acl-ipv4-adv-3001] rule permit ip source 192.168.2.0 0.0.0.255 destination 192.168.0.100 0 time-range work
[Device-acl-ipv4-adv-3001] quit
# Configure ACL 3002 to deny access from any other department to the financial database server.
[Device] acl advanced 3002
[Device-acl-ipv4-adv-3002] rule deny ip source any destination 192.168.0.100 0
[Device-acl-ipv4-adv-3002] quit
Applying ACLs to zone pairs for packet filtering:
# Create a zone pair with the source security zone
President and destination security zoneServer . Apply ACL 3000 to the zone pair for packet filtering.[Device] zone-pair security source president destination server
[Device-zone-pair-security-President-Server] packet-filter 3000
[Device-zone-pair-security-President-Server] quit
# Create a zone pair with the source security zone
Finance and destination security zoneServer . Apply ACL 3001 to the zone pair for packet filtering.[Device] zone-pair security source finance destination server
[Device-zone-pair-security-Finance-Server] packet-filter 3001
[Device-zone-pair-security-President-Server] quit
# Create a zone pair with the source security zone
Market and destination security zoneServer . Apply ACL 3002 to the zone pair for packet filtering.[Device] zone-pair security source market destination server
[Device-zone-pair-security-Market-Server] packet-filter 3002
[Device-zone-pair-security-Market-Server] quit
Verifying the configuration
# Verify that a PC in the Financial department can ping the database server during working hours. (All PCs in this example use Windows XP).
C:\> ping 192.168.0.100
Pinging 192.168.0.100 with 32 bytes of data:
Reply from 192.168.0.100: bytes=32 time=1ms TTL=255
Reply from 192.168.0.100: bytes=32 time<1ms TTL=255
Reply from 192.168.0.100: bytes=32 time<1ms TTL=255
Reply from 192.168.0.100: bytes=32 time<1ms TTL=255
Approximate round trip times in milli-seconds:
Minimum = 0ms, Maximum = 1ms, Average = 0ms
# Verify that a PC in the Marketing department cannot ping the database server during working hours.
C:\> ping 192.168.0.100
Pinging 192.168.0.100 with 32 bytes of data:
Request timed out.
Request timed out.
Request timed out.
Request timed out.
# Display configuration and match statistics for IPv4 advanced ACL 3001 and 3002 on the device during working hours.
Advanced IPv4 ACL 3001, 1 rule,
ACL's step is 5
rule 0 permit ip source 192.168.2.0 0.0.0.255 destination 192.168.0.100 0 time-range work
Advanced IPv4 ACL 3002, 1 rule,
ACL's step is 5
rule 0 deny ip destination 192.168.0.100 0
The output shows that the rule in ACL 3001 is active. ACL 3001 and ACL 3002 both have been matched four times as the result of the ping operations.
Configuration files
#
interface GigabitEthernet1/0/1
ip address 192.168.0.1 255.255.255.0
#
security-zone name Server
import interface GigabitEthernet1/0/1
#
security-zone name President
import interface GigabitEthernet1/0/2
#
security-zone name Finance
import interface GigabitEthernet1/0/3
#
security-zone name Market
import interface GigabitEthernet1/0/4
#
time-range work 08:00 to 18:00 working-day
#
acl advanced 3000
rule 0 permit ip source 192.168.1.0 0.0.0.255 destination 192.168.0.100 0
#
acl advanced 3001
rule 5 permit ip source 192.168.2.0 0.0.0.255 destination 192.168.0.100 0 time-range work
#
acl advanced 3002
rule 5 deny ip destination 192.168.0.100 0
#
zone-pair security source President destination Server
packet-filter 3000
#
zone-pair security source Finance destination Server
packet-filter 3001
#
zone-pair security source Market destination Server
packet-filter 3002
#