NTP server
This help contains the following topics:
Introduction
Network Time Protocol (NTP) is used to synchronize system clocks among distributed time servers and clients on a network. NTP runs over UDP and uses UDP port 123.
Operating mechanism
Figure-1 shows how NTP synchronizes the system time between two devices (Device A and Device B, in this example).
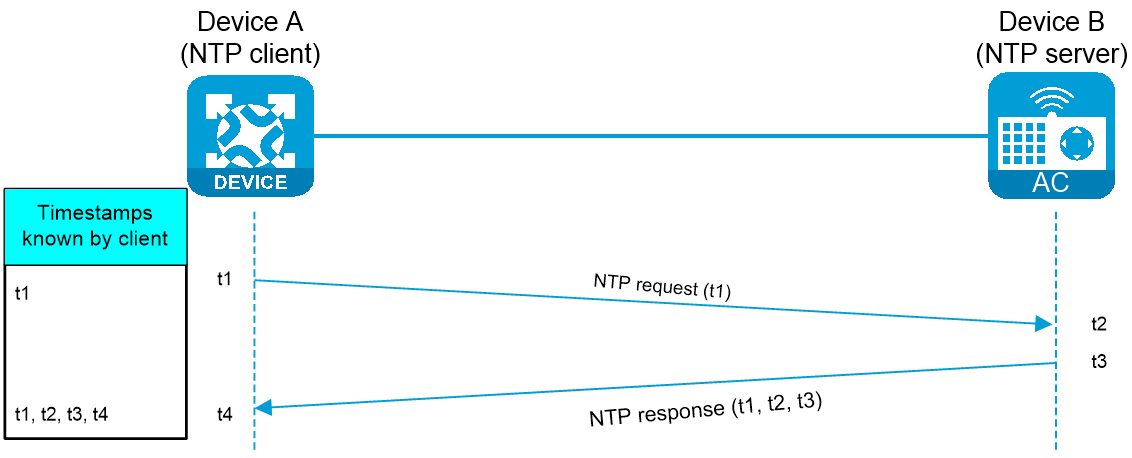
The synchronization process is as follows:
Device A sends Device B an NTP request, which is timestamped when it leaves Device A. The timestamp is t1.
Device B replies with an NTP response that carries t1, t2 (timestamp when the NTP request arrived at Device B), and t3 (timestamp when the NTP response left Device B).
When Device A receives the NTP response, the local time of Device A is t4.
Up to now, Device A can calculate the following parameters based on the timestamps:
The roundtrip delay of the NTP message: Delay = (t4 – t1) – (t3 – t2).
Time difference between Device A and Device B: Offset = [ (t2 – t1) + (t3 – t4) ] / 2.
Based on these parameters, Device A can be synchronized to Device B.
NTP architecture
NTP uses stratums 0 to 16 to define clock accuracy. A lower stratum level represents higher clock accuracy.
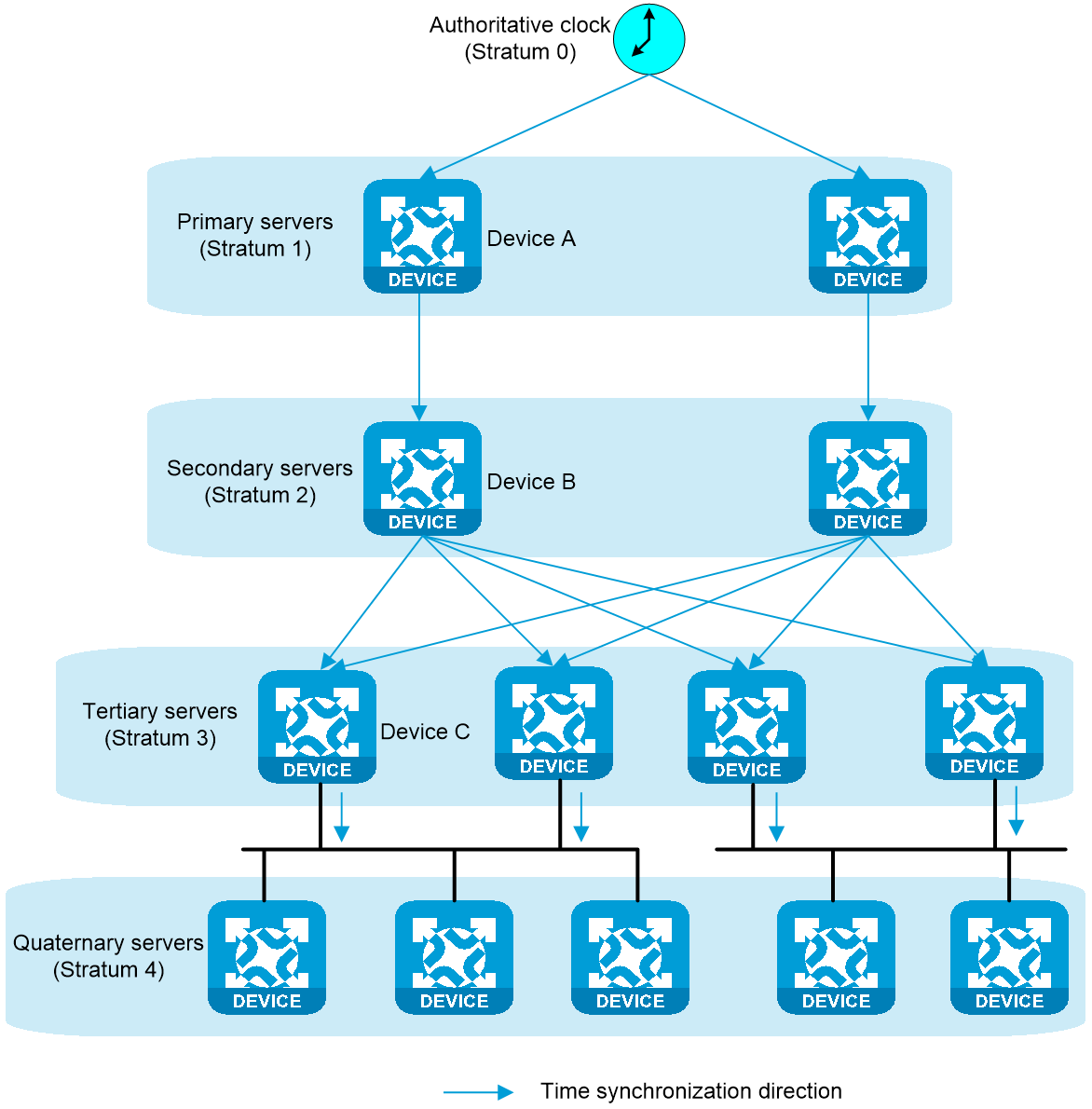
As shown in Figure-2, a stratum 1 NTP server (Device A) gets its time from an authoritative time source, such as an atomic clock. It provides time for other devices as the primary NTP server. The accuracy of each server is the stratum, with the topmost level (primary servers) assigned as one and each level downwards (secondary servers) in the hierarchy assigned as one greater than the preceding level. For example, the stratum is 2 for Device B, and 3 for Device C. Device B acts as an NTP client that synchronizes the NTP clock from Device A, and also acts as an NTP server that transmits the NTP clock to Device C.
To ensure time accuracy and availability, you can specify multiple NTP servers for a device. The device selects an optimal NTP server as the clock source based on parameters such as stratum. The clock that the device selects is called the reference source. For more information about clock selection, see the related protocols and standards.
If the devices in a network cannot synchronize with an authoritative time source, you can perform the following tasks:
Select a device that has a relatively accurate clock from the network.
Use the local clock of the device as the reference clock to synchronize other devices in the network.
NTP authentication
Use this feature to authenticate the NTP messages for security purposes. If an NTP message passes authentication, the device can receive it and obtain time synchronization information. If the NTP message fails the authentication, the device discards the message. This feature prevents the device from synchronizing time with an unauthorized time server.
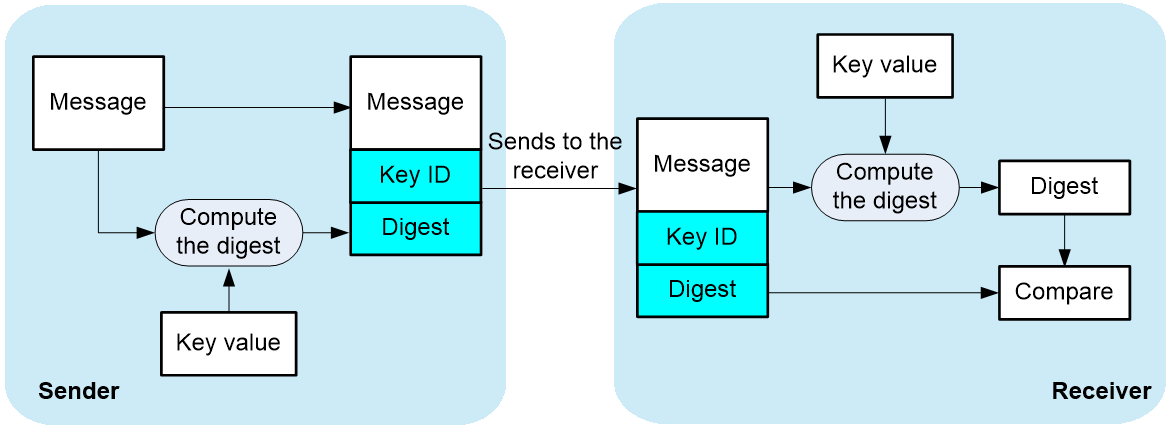
As shown in Figure-3, NTP authentication is performed as follows:
The sender uses the key identified by the key ID to calculate a digest for the NTP message through the MD5 or HMAC authentication algorithm. Then it sends the calculated digest together with the NTP message and key ID to the receiver.
Upon receiving the message, the receiver performs the following actions:
Finds the key according to the key ID in the message.
Uses the key and the MD5 or HMAC authentication algorithm to calculate the digest for the message.
Compares the digest with the digest contained in the NTP message.
If they are different, the receiver discards the message.
If they are the same and an NTP association is not required to be established, the receiver provides a response packet.
If they are the same and an NTP association is required to be established or has existed, the local device determines whether the sender is allowed to use the authentication ID. If the sender is allowed to use the authentication ID, the receiver accepts the message. If the sender is not allowed to use the authentication ID, the receiver discards the message.
Application scenarios
Various tasks, including network management, charging, auditing, and distributed computing depend on accurate and synchronized system time setting on the network devices. NTP is typically used in large networks to dynamically synchronize time among network devices.
NTP guarantees higher clock accuracy than manual system clock setting. In a small network that does not require high clock accuracy, you can keep time synchronized among devices by changing their system clocks one by one.
Restrictions and guidelines
The device, when acting as an NTP client, requires the clock stratum of the NTP server to be in the inclusive range of 0 to 14. If the clock stratum of the NTP server exceeds 14, some NTP clients will not synchronize with the NTP server's clock.
Configuration guide
Analysis
Configure NTP as shown in the following figure:
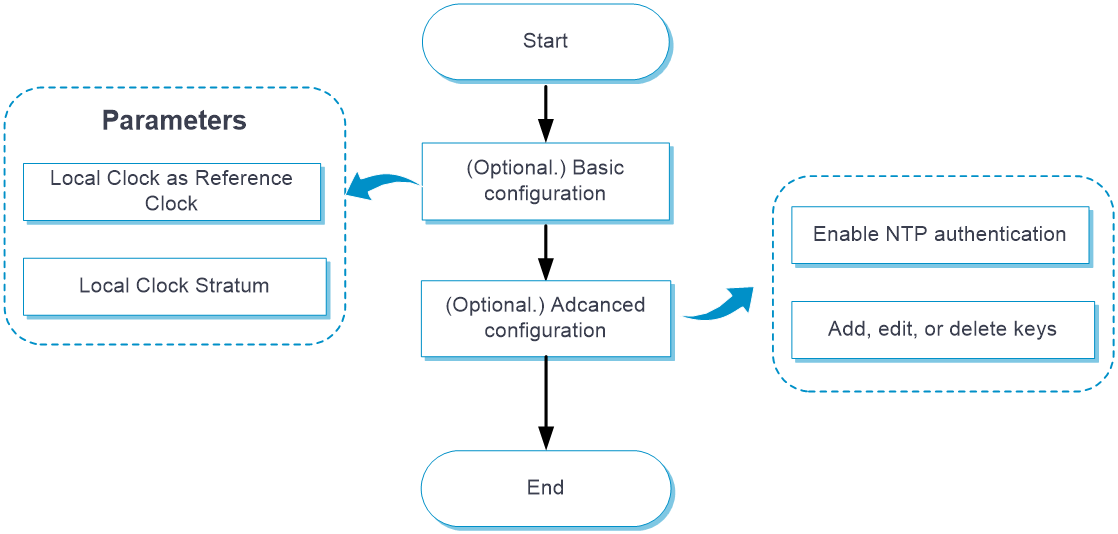
Basic configuration
You do not need to configure this feature on the device if it only transmits the NTP clock received from the upper-level device to lower-level devices. Configured with this feature, the device uses the locally generated clock signal as the reference source and transmits the clock signal to lower-level devices. |
From the left navigation pane, select Configure > Network Config > More > NTPServer.
In the Basic Settings area, turn on the NTP Service (Local Clock as Reference Clock) feature.
Configure the local clock stratum. A smaller value represents a higher clock stratum.
Click Submit.
Advanced configuration
Use advanced NTP configuration to configure NTP authentication.
From the left navigation pane, select Configure > Network Config > More > NTPServer.
In the Advanced Settings area, turn on the NTP Authentication feature.
Click Add.
Enter the key number and key, and select a key verification algorithm. The following supported key verification algorithms are in descending order of security: hmac-sha-512, hmac-sha-384, hmac-sha-256, hmac-sha-1, and md5. Click the OK icon in the Actions column. To cancel the NTP authentication key configuration, click the Cancel icon in the Actions column.
Click Submit.
For an NTP client to pass the authentication and synchronize time from the device after you enable NTP authentication on the device, perform the following tasks:
Configure the same key number, key, and key verification algorithm on the NTP client.
When you specify a NTP server for the NTP client, specify that key.
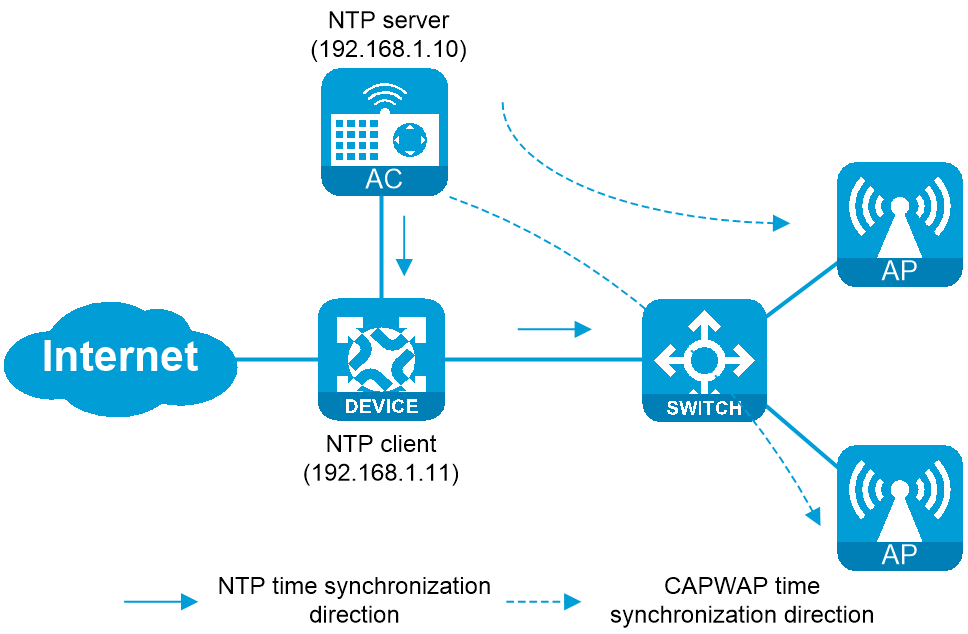
Example: Configuring an AC as the reference source
Network configuration
As shown in Figure-4, no available external reference sources exist on the wireless network. Configure the AC as the reference source so that other devices synchronize time from the AC’s local clock. To ensure time synchronization security, all devices must be authenticated during time synchronization. Configure the key number as 1, key as test1234, and key verification algorithm as hmac-sha-512 for NTP authentication.
In this example, the APs synchronize time from the AC through the CAPWAP protocol. (Details not shown.)
Procedure
Configure the NTP service
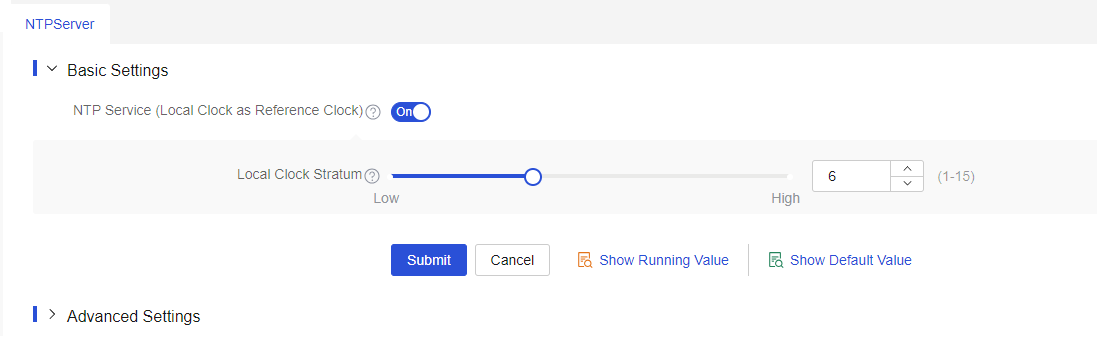
From the left navigation pane, select Configure > Network Config > More > NTPServer.
In the Basic Settings area, turn on the NTP Service (Local Clock as Reference Clock) feature.
Configure the local clock stratum as 6.
Click Submit.
Figure-5 Configuring the local clock as the reference source
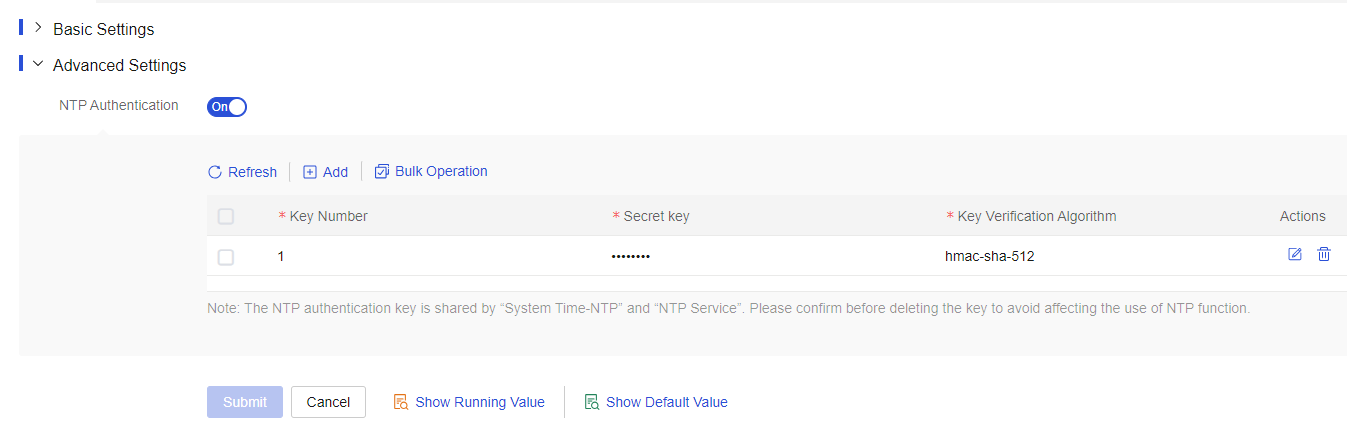
In the Advanced Settings area, turn on the NTP Authentication feature.
Click Add.
Enter 1 in the Key Number column and test1234 in the Secret Key column, and select the hmac-sha-512 key verification algorithm. Click the OK icon in the Actions column.
Click Submit.
Figure-6 Configuring an NTP authentication key
Verify the configuration
Log in to the NTP client and configure NTP client settings. Verify that the time of the NTP client is the same as that of the AC.
