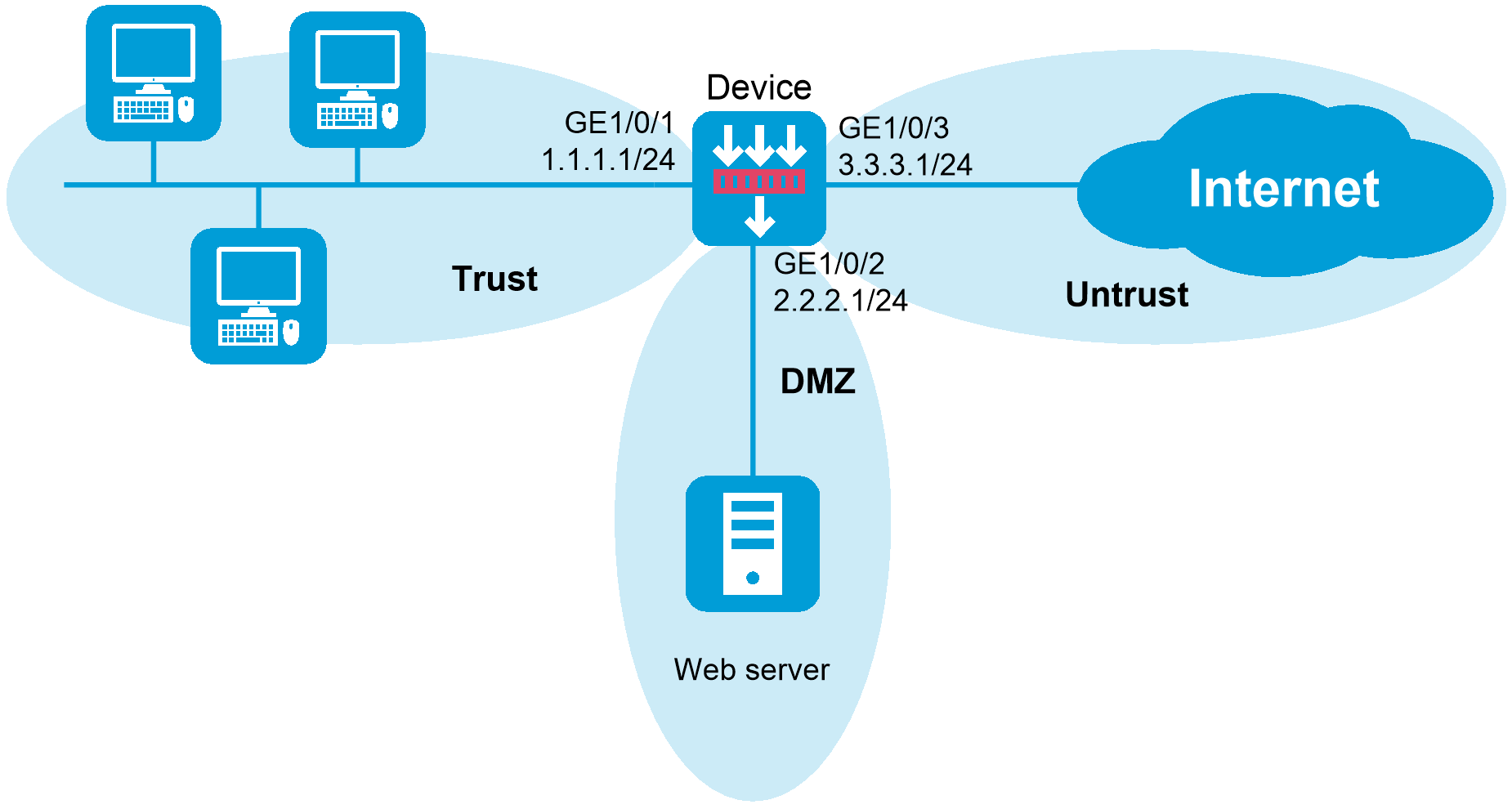
As shown in Figure 1, a security protection device (Device) connects the corporate network to the Internet. The corporate network needs to provide Web services for only internal users.
To ensure corporate network security, configure the device as follows:
Assign GigabitEthernet 1/0/1, GigabitEthernet 1/0/2, and GigabitEthernet 1/0/3 to security zones Trust, DMZ, and Untrust, respectively.
Configure zone pairs and apply interzone policies to control access as follows:
Allow internal users to access the Web server and the Internet.
Forbid external users to access the internal network and the Web server.
Forbid the Web server to access the internal network.
This configuration example was created and verified on R9071 of the M9000-AI-E8 device.
1. Assign IP address to the interfaces.
# Assign an IP address to GigabitEthernet 1/0/1.
<Device> system-view
[Device] interface gigabitethernet 1/0/1
[Device-GigabitEthernet1/0/1] ip address 1.1.1.1 255.255.255.0
[Device-GigabitEthernet1/0/1] quit
# Assign IP addresses to other interfaces in the same way. (Details not shown.)
2. Add interfaces to security zones.
[Device] security-zone name trust
[Device-security-zone-Trust] import interface gigabitethernet 1/0/1
[Device-security-zone-Trust] quit
[Device] security-zone name dmz
[Device-security-zone-DMZ] import interface gigabitethernet 1/0/2
[Device-security-zone-DMZ] quit
[Device] security-zone name untrust
[Device-security-zone-Untrust] import interface gigabitethernet 1/0/3
[Device-security-zone-Untrust] quit
3. Configure ACLs.
# Configure ACL 3001 to allow internal hosts to access the Internet.
[Device] acl advanced 3001
[Device-acl-ipv4-adv-3500] rule permit ip source 1.1.1.0 0.0.0.255 destination 3.3.3.0 0.0.0.255
[Device-acl-ipv4-adv-3500] quit
# Configure ACL 3002 to allow internal hosts to access the Web server.
[Device] acl advanced 3002
[Device-acl-ipv4-adv-3002] rule permit ip source 1.1.1.0 0.0.0.255 destination 2.2.2.0 0.0.0.255
[Device-acl-ipv4-adv-3500] quit
4. Configure zone pairs.
# Create a zone pair with the source security zone Trust and destination security zone Untrust. Apply ACL 3001 to the zone pair.
[Device] zone-pair security source trust destination untrust
[Device-zone-pair-security-Trust-Untrust] packet-filter 3001
[Device-zone-pair-security-Trust-Untrust] quit
# Create a zone pair with the source security zone Trust and destination security zone DMZ. Apply ACL 3002 to the zone pair.
[Device] zone-pair security source trust destination dmz
[Device-zone-pair-security-Trust-DMZ] packet-filter 3002
[Device-zone-pair-security-Trust-DMZ] quit
# Verify that internal hosts can access the Internet and the Web server. (Details not shown.)
# Verify that access requests initiated from the Internet and the DMZ zone to the internal network are denied. (Details not shown.)
#
interface GigabitEthernet1/0/1
ip address 1.1.1.1 255.255.255.0
#
interface GigabitEthernet1/0/2
ip address 2.2.2.1 255.255.255.0
#
interface GigabitEthernet1/0/3
ip address 3.3.3.1 255.255.255.0
#
security-zone name Trust
import interface GigabitEthernet1/0/1
#
security-zone name DMZ
import interface GigabitEthernet1/0/2
#
security-zone name Untrust
import interface GigabitEthernet1/0/3
#
acl advanced 3001
rule 0 permit ip source 1.1.1.0 0.0.0.255 destination 3.3.3.0 0.0.0.255
#
acl advanced 3002
rule 0 permit ip source 1.1.1.0 0.0.0.255 destination 2.2.2.0 0.0.0.255
#
zone-pair security source Trust destination Untrust
packet-filter 3001
#
zone-pair security source Trust destination DMZ
packet-filter 3002
#