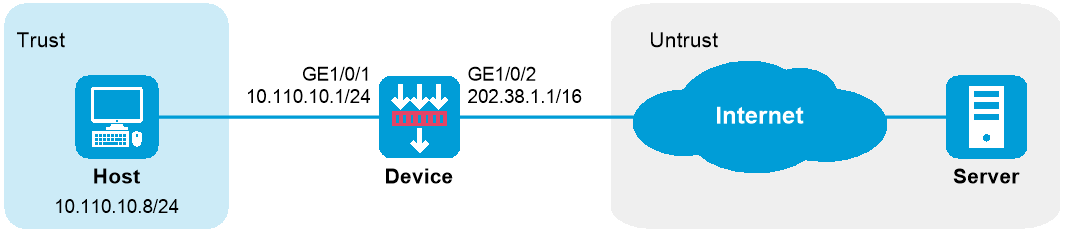
Configure static NAT to allow the host at 10.110.10.8/24 to access the Internet.
Figure 1 Network diagram
This configuration example was created and verified on R9071 of the M9000-AI-E8 device.
# Assign IP addresses to interfaces and configure routes, security zones, zone pairs, and interzone policies. Make sure the network connections are available. (Details not shown.)
# Configure a one-to-one static NAT mapping between the private address 10.110.10.8 and the public address 202.38.1.100.
<Device> system-view
[Device] nat static outbound 10.110.10.8 202.38.1.100
# Enable static NAT on GigabitEthernet 1/0/2.
[Device] interface gigabitethernet 1/0/2
[Device-GigabitEthernet1/0/2] nat static enable
[Device-GigabitEthernet1/0/2] quit
# Verify that the host at 10.110.10.8/24 can access the server on the Internet. (Details not shown.)
# Display static NAT configuration.
[Device] display nat static
Static NAT mappings:
Totally 1 outbound static NAT mappings.
IP-to-IP:
Local IP : 10.110.10.8
Global IP : 202.38.1.100
Config status: Active
Interfaces enabled with static NAT:
Totally 1 interfaces enabled with static NAT.
Interface: GigabitEthernet1/0/2
Config status: Active
# Display NAT sessions.
[Device] display nat session verbose
Slot 1:
Initiator:
Source IP/port: 10.110.10.8/54765
Destination IP/port: 202.38.1.2/23
DS-Lite tunnel peer: -
VPN instance/VLAN ID/Inline ID: -/-/-
Protocol: TCP(6)
Inbound interface: GigabitEthernet1/0/1
Source security zone: Trust
Responder:
Source IP/port: 202.38.1.2/23
Destination IP/port: 202.38.1.100/54765
DS-Lite tunnel peer: -
VPN instance/VLAN ID/Inline ID: -/-/-
Protocol: TCP(6)
Inbound interface: GigabitEthernet1/0/2
Source security zone: Untrust
State: TCP_ESTABLISHED
Application: TELNET
Rule ID: -/-/-
Rule name:
Start time: 2017-05-19 10:57:47 TTL: 1195s
Initiator->Responder: 8 packets 375 bytes
Responder->Initiator: 10 packets 851 bytes
Total sessions found: 1
#
nat static outbound 10.110.10.8 202.38.1.100
#
interface GigabitEthernet1/0/1
ip address 10.110.10.1 255.255.255.0
#
interface GigabitEthernet1/0/2
ip address 202.38.1.1 255.255.0.0
nat static enable
#
security-zone name Trust
import interface GigabitEthernet1/0/1
#
security-zone name Untrust
import interface GigabitEthernet1/0/2
#
security-policy ip
rule 0 name trust-untrust
action pass
source-zone trust
destination-zone untrust
rule 1 name untrust-trust
action pass
source-zone untrust
destination-zone trust