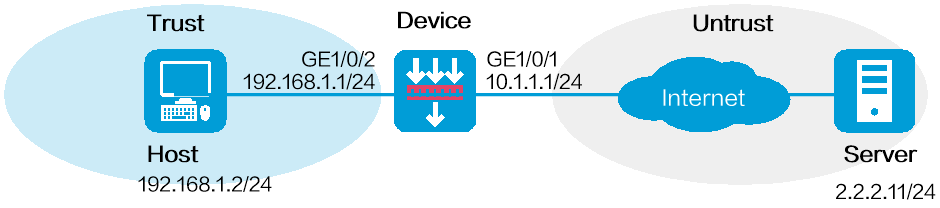
Configure an ASPF policy on the device to inspect the FTP traffic flows passing through the device. Only return packets for FTP connections initiated by users on the internal network are permitted to pass through the device and get into the internal network. All other types of packets from the external network to the internal network are blocked.
Figure 1 Network diagram
This configuration example was created and verified on R9071 of the M9000-AI-E8 device.
1. Configure the device.
# Assign IP addresses to the device interfaces.
<Device> system-view
[Device] interface gigabitethernet 1/0/1
[Device-GigabitEthernet1/0/1] ip address 10.1.1.1 255.255.255.0
[Device-GigabitEthernet1/0/1] quit
[Device] interface gigabitethernet 1/0/2
[Device-GigabitEthernet1/0/2] ip address 192.168.1.1 255.255.255.0
[Device-GigabitEthernet1/0/2] quit
# Add the device interfaces to security zones.
[Device] security-zone name trust
[Device-security-zone-Trust] import interface gigabitethernet 1/0/2
[Device-security-zone-Trust] quit
[Device] security-zone name untrust
[Device-security-zone-Untrust] import interface gigabitethernet 1/0/1
[Device-security-zone-Untrust] quit
2. Configure settings for routing.
This example configures a static route, and the next hop in the route is 10.1.1.2.
[Device] ip route-static 2.2.2.0 24 10.1.1.2
3. Configure ACL 3500 to permit the IP packets from the host to the Internet.
[Device] acl advanced 3500
[Device-acl-ipv4-adv-3500] rule permit ip source 192.168.1.0 0.0.0.255
[Device-acl-ipv4-adv-3500] quit
4. Create ASPF policy 1 for FTP inspection.
[Device] aspf policy 1
[Device-aspf-policy-1] detect ftp
[Device-aspf-policy-1] quit
5. Create a zone pair with the source security zone Trust and destination zone Untrust. Apply the ACL to the zone pair to permit the IP packets between the host and the Internet, and apply the ASPF policy to the zone pair.
[Device] zone-pair security source trust destination untrust
[Device-zone-pair-security-Trust-Untrust] packet-filter 3500
[Device-zone-pair-security-Trust-Untrust] aspf apply policy 1
[Device-zone-pair-security-Trust-Untrust] quit
# Verify that an ASPF session has been established for the FTP connection between the host and the server.
<Device> display aspf session ipv4
Slot 0:
Initiator:
Source IP/port: 192.168.1.2/1877
Destination IP/port: 2.2.2.11/21
VPN instance/VLAN ID/Inline ID: -/-/-
Protocol: TCP(6)
Inbound interface: GigabitEthernet1/0/1
Source security zone: Trust
Total sessions found: 1
# Verify that only return packets that match the entries can enter the internal network. (Details not shown.)
#
interface GigabitEthernet1/0/1
port link-mode route
ip address 10.1.1.1 255.255.255.0
#
interface GigabitEthernet1/0/2
port link-mode route
ip address 192.168.1.1 255.255.255.0
#
security-zone name Untrust
import interface GigabitEthernet1/0/1
#
security-zone name Trust
import interface GigabitEthernet1/0/2
#
ip route-static 2.2.2.0 24 10.1.1.2
#
aspf policy 1
detect ftp
#
zone-pair security source Trust destination Untrust
packet-filter 3500
aspf apply policy 1
#
acl advanced 3500
rule 0 permit ip source 192.168.1.0 0.0.0.255
#