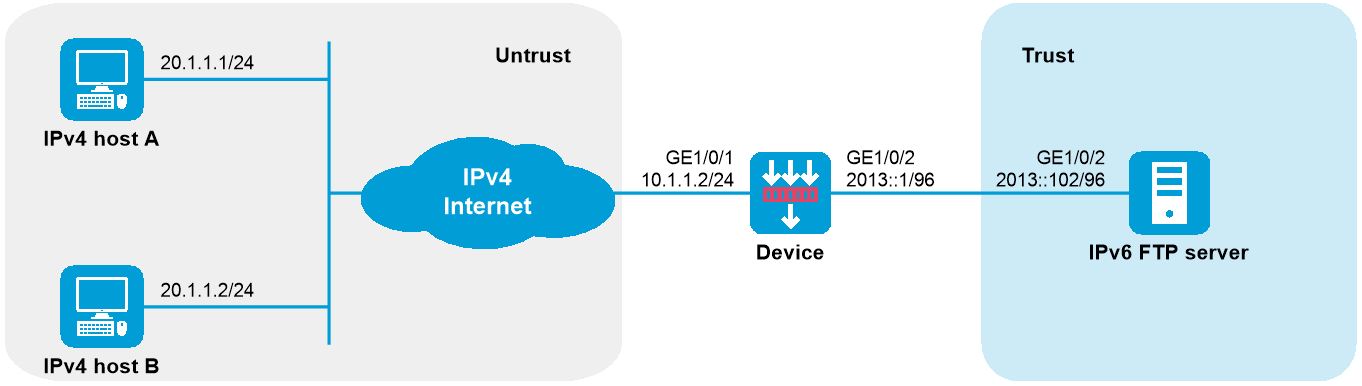
As shown in Figure 1, a company upgrades the network to IPv6, and it has an IPv4 address 10.1.1.1.
To allow the IPv6 FTP server to provide FTP services to IPv4 hosts, configure the following AFT policies on the device:
Map the IPv6 FTP server's IPv6 address and TCP port number to the company's IPv4 address and TCP port number.
Configure a NAT64 prefix to translate source IPv4 addresses of IPv4 packets to source IPv6 addresses.
This configuration example was created and verified on R9071 of the M9000-AI-E8 device.
1. Assign IP addresses to interfaces:
# Assign an IP address to interface GigabitEthernet 1/0/1.
<Device> system-view
[Device] interface gigabitethernet 1/0/1
[Device-GigabitEthernet1/0/1] ip address 10.1.1.2 24
[Device-GigabitEthernet1/0/1] quit
# Assign IP addresses to other interfaces in the same way. (Details not shown.)
2. Add interfaces to security zones.
[Device] security-zone name trust
[Device-security-zone-Trust] import interface gigabitethernet 1/0/2
[Device-security-zone-Trust] quit
[Device] security-zone name untrust
[Device-security-zone-Untrust] import interface gigabitethernet 1/0/1
[Device-security-zone-Untrust] quit
3. Configure security policies:
# In the IPv4 security policy, configure a rule named aftlocalin to allow the device to perform AFT on the IPv4 traffic destined for the IPv6 FTP server.
[Device] security-policy ip
[Device-security-policy-ip] rule name aftlocalin
[Device-security-policy-ip-1-aftlocalin] source-zone untrust
[Device-security-policy-ip-1-aftlocalin] destination-zone local
[Device-security-policy-ip-1-aftlocalin] destination-ip-host 10.1.1.1
[Device-security-policy-ip-1-aftlocalin] action pass
[Device-security-policy-ip-1-aftlocalin] quit
[Device-security-policy-ip] quit
# In the IPv6 security policy, configure a rule named aftlocalout to allow the device to forward the AFT-translated packets to the IPv6 server.
[Device] security-policy ipv6
[Device-security-policy-ipv6] rule name aftlocalout
[Device-security-policy-ipv6-1-aftlocalout] source-zone local
[Device-security-policy-ipv6-1-aftlocalout] destination-zone trust
[Device-security-policy-ipv6-1-aftlocalout] source-ip-subnet 2012:: 96
[Device-security-policy-ipv6-1-aftlocalout] destination-ip-host 2013::102
[Device-security-policy-ipv6-1-aftlocalout] action pass
[Device-security-policy-ipv6-1-aftlocalout] quit
[Device-security-policy-ipv6] quit
4. Configure AFT settings:
# Map IPv4 address 10.1.1.1 with TCP port 21 to IPv6 address 2013::102 with TCP port 21 for the IPv6 internal FTP server.
[Device] aft v6server protocol tcp 10.1.1.1 21 2013::102 21
# Configure the device to use NAT64 prefix 2012:: 96 to translate source addresses of IPv4 packets.
[Device] aft prefix-nat64 2012:: 96
# Enable AFT on the interfaces connected to the IPv4 Internet and IPv6 network, respectively.
[Device] interface gigabitethernet 1/0/1
[Device-GigabitEthernet1/0/1] aft enable
[Device-GigabitEthernet1/0/1] quit
[Device] interface gigabitethernet 1/0/2
[Device-GigabitEthernet1/0/2] aft enable
[Device-GigabitEthernet1/0/2] quit
# Verify that IPv4 hosts can use FTP to access the IPv6 FTP server. (Details not shown.)
# Display detailed information about IPv4 AFT sessions on the device.
[Device] display aft session ipv4 verbose
Initiator:
Source IP/port: 20.1.1.1/11025
Destination IP/port: 10.1.1.1/21
DS-Lite tunnel peer: -
VPN instance/VLAN ID/Inline ID: -/-/-
Protocol: TCP(6)
Inbound interface: GigabitEthernet1/0/1
Source security zone: Untrust
Responder:
Source IP/port: 10.1.1.1/21
Destination IP/port: 20.1.1.1/11025
DS-Lite tunnel peer: -
VPN instance/VLAN ID/Inline ID: -/-/-
Protocol: TCP(6)
Inbound interface: GigabitEthernet1/0/2
Source security zone: Local
State: TCP_ESTABLISHED
Application: FTP
Rule ID: -/-/-
Rule name:
Start time: 2014-03-13 09:07:30 TTL: 3577s
Initiator->Responder: 3 packets 124 bytes
Responder->Initiator: 2 packets 108 bytes
Total sessions found: 1
# Display detailed information about IPv6 AFT sessions on the device.
[Device] display aft session ipv6 verbose
Initiator:
Source IP/port: 2012::1401:0101/1029
Destination IP/port: 2013::102/21
VPN instance/VLAN ID/Inline ID: -/-/-
Protocol: TCP(6)
Inbound interface: GigabitEthernet1/0/1
Source security zone: Local
Responder:
Source IP/port: 2013::102/21
Destination IP/port: 2012::1401:0101/1029
VPN instance/VLAN ID/Inline ID: -/-/-
Protocol: TCP(6)
Inbound interface: GigabitEthernet1/0/2
Source security zone: Trust
State: TCP_ESTABLISHED
Application: FTP
Rule ID: 0
Rule name: aftlocalout
Start time: 2014-03-13 09:07:30 TTL: 3582s
Initiator->Responder: 3 packets 184 bytes
Responder->Initiator: 2 packets 148 bytes
Total sessions found: 1
#
interface GigabitEthernet1/0/1
ip address 10.1.1.2 255.255.255.0
aft enable
#
interface GigabitEthernet1/0/2
aft enable
ipv6 address 2013::1/96
#
security-zone name Trust
import interface GigabitEthernet1/0/2
#
security-zone name Untrust
import interface GigabitEthernet1/0/1
#
aft prefix-nat64 2012:: 96
aft v6server protocol tcp 10.1.1.1 21 2013::102 21
#
security-policy ip
rule 0 name aftlocalin
action pass
source-zone untrust
destination-zone local
destination-ip-host 10.1.1.1
#
security-policy ipv6
rule 0 name aftlocalout
action pass
source-zone local
destination-zone trust
source-ip-subnet 2012::/96
destination-ip-host 2013::102