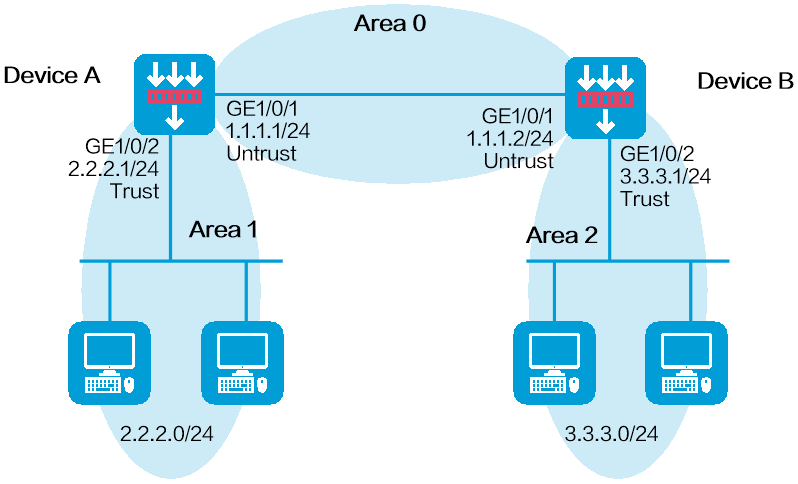
As shown in Figure 1, all devices run OSPF and the AS is divided into three areas. Device A and Device B act as ABRs to forward routes between areas. After configuration, each router should learn all routes to the AS.
This configuration example was created and verified on R9071 of the M9000-AI-E8 device.
1. Configure IP addresses for interfaces correctly according to Figure 1.
<DeviceA> system-view
[DeviceA] interface gigabitethernet 1/0/1
[DeviceA-GigabitEthernet1/0/1] ip address 1.1.1.1 255.255.255.0
[DeviceA-GigabitEthernet1/0/1] quit
[DeviceA] interface gigabitethernet 1/0/2
[DeviceA-GigabitEthernet1/0/2] ip address 2.2.2.1 255.255.255.0
[DeviceA-GigabitEthernet1/0/2] quit
2. Add each interface on Device A to a security zone.
[DeviceA] security-zone name trust
[DeviceA-security-zone-Trust] import interface gigabitethernet 1/0/2
[DeviceA-security-zone-Trust] quit
[DeviceA] security-zone name untrust
[DeviceA-security-zone-Untrust] import interface gigabitethernet 1/0/1
[DeviceA-security-zone-Untrust] quit
3. Configure security policies.
a. Configure a security policy to allow OSPF neighbor relationship establishment by permitting traffic between security zone untrust and security zone local.
# Create security policy rule ospflocalin and permit Device A to receive OSPF packets from Device B.
[DeviceA] security-policy ip
[DeviceA-security-policy-ip] rule name ospflocalin
[DeviceA-security-policy-ip-0-ospflocalin] source-zone untrust
[DeviceA-security-policy-ip-0-ospflocalin] destination-zone local
[DeviceA-security-policy-ip-0-ospflocalin] service ospf
[DeviceA-security-policy-ip-0-ospflocalin] action pass
[DeviceA-security-policy-ip-0-ospflocalin] quit
# Create security policy rule ospflocalout and permit Device A to send OSPF packets to Device B.
[DeviceA-security-policy-ip] rule name ospflocalout
[DeviceA-security-policy-ip-1-ospflocalout] source-zone local
[DeviceA-security-policy-ip-1-ospflocalout] destination-zone untrust
[DeviceA-security-policy-ip-1-ospflocalout] service ospf
[DeviceA-security-policy-ip-1-ospflocalout] action pass
[DeviceA-security-policy-ip-1-ospflocalout] quit
b. Configure a security policy to permit traffic between security zone untrust and security zone trust.
# Create security policy rule trust-untrust and permit packets from security zone trust to security zone untrust to pass.
[DeviceA-security-policy-ip] rule name trust-untrust
[DeviceA-security-policy-ip-2-trust-untrust] source-zone trust
[DeviceA-security-policy-ip-2-trust-untrust] destination-zone untrust
[DeviceA-security-policy-ip-2-trust-untrust] source-ip-subnet 2.2.2.0 24
[DeviceA-security-policy-ip-2-trust-untrust] destination-ip-subnet 3.3.3.0 24
[DeviceA-security-policy-ip-2-trust-untrust] action pass
[DeviceA-security-policy-ip-2-trust-untrust] quit
# Create security policy rule untrust-trust and permit packets from security zone untrust to security zone trust to pass.
[DeviceA-security-policy-ip] rule name untrust-trust
[DeviceA-security-policy-ip-3-untrust-trust] source-zone untrust
[DeviceA-security-policy-ip-3-untrust-trust] destination-zone trust
[DeviceA-security-policy-ip-3-untrust-trust] source-ip-subnet 3.3.3.0 24
[DeviceA-security-policy-ip-3-untrust-trust] destination-ip-subnet 2.2.2.0 24
[DeviceA-security-policy-ip-3-untrust-trust] action pass
[DeviceA-security-policy-ip-3-untrust-trust] quit
[DeviceA-security-policy-ip] quit
4. Enable basic OSPF functions.
[DeviceA] router id 2.2.2.1
[DeviceA] ospf
[DeviceA-ospf-1] area 0
[DeviceA-ospf-1-area-0.0.0.0] network 1.1.1.0 0.0.0.255
[DeviceA-ospf-1-area-0.0.0.0] quit
[DeviceA-ospf-1] area 1
[DeviceA-ospf-1-area-0.0.0.1] network 2.2.2.0 0.0.0.255
[DeviceA-ospf-1-area-0.0.0.1] quit
[DeviceA-ospf-1] quit
1. Configure IP addresses for interfaces correctly according to Figure 1.
<DeviceB> system-view
[DeviceB] interface gigabitethernet 1/0/1
[DeviceB-GigabitEthernet1/0/1] ip address 1.1.1.2 255.255.255.0
[DeviceB-GigabitEthernet1/0/1] quit
[DeviceB] interface gigabitethernet 1/0/2
[DeviceB-Gigabitethernet1/0/2] ip address 3.3.3.1 255.255.255.0
[DeviceB-Gigabitethernet1/0/2] quit
2. Add each interface on Device B to a security zone.
[DeviceB] security-zone name untrust
[DeviceB-security-zone-Untrust] import interface gigabitethernet 1/0/1
[DeviceB-security-zone-Untrust] quit
[DeviceB] security-zone name trust
[DeviceB-security-zone-Trust] import interface gigabitethernet 1/0/2
[DeviceB-security-zone-Trust] quit
3. Configure security policies.
a. Configure a security policy to allow OSPF neighbor relationship establishment by permitting traffic between security zone untrust and security zone local.
# Create security policy rule ospflocalin and permit Device B to receive OSPF packets from Device A.
[DeviceB] security-policy ip
[DeviceB-security-policy-ip] rule name ospflocalin
[DeviceB-security-policy-ip-0-ospflocalin] source-zone untrust
[DeviceB-security-policy-ip-0-ospflocalin] destination-zone local
[DeviceB-security-policy-ip-0-ospflocalin] service ospf
[DeviceB-security-policy-ip-0-ospflocalin] action pass
[DeviceB-security-policy-ip-0-ospflocalin] quit
# Create security policy rule ospflocalout and permit Device B to send OSPF packets to Device A.
[DeviceB-security-policy-ip] rule name ospflocalout
[DeviceB-security-policy-ip-1-ospflocalout] source-zone local
[DeviceB-security-policy-ip-1-ospflocalout] destination-zone untrust
[DeviceB-security-policy-ip-1-ospflocalout] service ospf
[DeviceB-security-policy-ip-1-ospflocalout] action pass
[DeviceB-security-policy-ip-1-ospflocalout] quit
b. Configure a security policy to permit traffic between security zone untrust and security zone trust.
# Create security policy rule trust-untrust and permit packets from security zone trust to security zone untrust to pass.
[DeviceB-security-policy-ip] rule name trust-untrust
[DeviceB-security-policy-ip-2-trust-untrust] source-zone trust
[DeviceB-security-policy-ip-2-trust-untrust] destination-zone untrust
[DeviceB-security-policy-ip-2-trust-untrust] source-ip-subnet 3.3.3.0 24
[DeviceB-security-policy-ip-2-trust-untrust] destination-ip-subnet 2.2.2.0 24
[DeviceB-security-policy-ip-2-trust-untrust] action pass
[DeviceB-security-policy-ip-2-trust-untrust] quit
# Create security policy rule untrust-trust and permit packets from security zone untrust to security zone trust to pass.
[DeviceB-security-policy-ip] rule name untrust-trust
[DeviceB-security-policy-ip-3-untrust-trust] source-zone untrust
[DeviceB-security-policy-ip-3-untrust-trust] destination-zone trust
[DeviceB-security-policy-ip-3-untrust-trust] source-ip-subnet 2.2.2.0 24
[DeviceB-security-policy-ip-3-untrust-trust] destination-ip-subnet 3.3.3.0 24
[DeviceB-security-policy-ip-3-untrust-trust] action pass
[DeviceB-security-policy-ip-3-untrust-trust] quit
[DeviceB-security-policy-ip] quit
4. Enable basic OSPF functions.
[DeviceB] router id 3.3.3.1
[DeviceB] ospf
[DeviceB-ospf-1] area 0
[DeviceB-ospf-1-area-0.0.0.0] network 1.1.1.0 0.0.0.255
[DeviceB-ospf-1-area-0.0.0.0] quit
[DeviceB-ospf-1] area 2
[DeviceB-ospf-1-area-0.0.0.2] network 3.3.3.0 0.0.0.255
[DeviceB-ospf-1-area-0.0.0.2] quit
[DeviceB-ospf-1] quit
# View detailed information about OSPF neighbors on Device A.
[DeviceA] display ospf peer verbose
OSPF Process 1 with Router ID 2.2.2.1
Neighbors
Area 0.0.0.0 interface 1.1.1.1(GigabitEthernet1/0/1)'s neighbors
Router ID: 3.3.3.1 Address: 1.1.1.2 GR State: Normal
State: Full Mode: Nbr is master Priority: 1
DR: 1.1.1.1 BDR: 1.1.1.2 MTU: 0
Options is 0x42 (-|O|-|-|-|-|E|-)
Dead timer due in 32 sec
Neighbor is up for 00:07:08
Authentication Sequence: [ 0 ]
Neighbor state change count: 5
BFD status: Disabled
# View OSPF routing information on Device A.
[DeviceA] display ospf routing
OSPF Process 1 with Router ID 2.2.2.1
Routing Table
Routing for network
Destination Cost Type NextHop AdvRouter Area
3.3.3.0/24 2 Inter 1.1.1.2 3.3.3.1 0.0.0.0
2.2.2.0/24 1 Stub 0.0.0.0 2.2.2.1 0.0.0.1
1.1.1.0/24 1 Transit 0.0.0.0 2.2.2.1 0.0.0.0
Total nets: 3
Intra area: 2 Inter area: 1 ASE: 0 NSSA: 0
# Verify that devices in area 1 can ping PCs in area 2, and vice versa.
#
router id 2.2.2.1
#
ospf 1
area 0.0.0.0
network 1.1.1.0 0.0.0.255
area 0.0.0.1
network 2.2.2.0 0.0.0.255
#
interface GigabitEthernet1/0/1
port link-mode route
ip address 1.1.1.1 255.255.255.0
#
interface GigabitEthernet1/0/2
port link-mode route
ip address 2.2.2.1 255.255.255.0
#
security-zone name Untrust
import interface GigabitEthernet1/0/1
#
security-zone name Trust
import interface GigabitEthernet1/0/2
#
security-policy ip
rule 0 name ospflocalin
action pass
source-zone untrust
destination-zone local
service ospf
rule 1 name ospflocalout
action pass
source-zone local
destination-zone untrust
service ospf
rule 2 name trust-untrust
action pass
source-zone trust
destination-zone untrust
source-ip-subnet 2.2.2.0 255.255.255.0
destination-ip-subnet 3.3.3.0 255.255.255.0
rule 3 name untrust-trust
action pass
source-zone untrust
destination-zone trust
source-ip-subnet 3.3.3.0 255.255.255.0
destination-ip-subnet 2.2.2.0 255.255.255.0
#
#
router id 3.3.3.1
#
ospf 1
area 0.0.0.0
network 1.1.1.0 0.0.0.255
area 0.0.0.2
network 3.3.3.0 0.0.0.255
#
interface GigabitEthernet1/0/1
port link-mode route
ip address 1.1.1.2 255.255.255.0
#
interface GigabitEthernet1/0/2
port link-mode route
ip address 3.3.3.1 255.255.255.0
#
security-zone name Untrust
import interface GigabitEthernet1/0/1
#
security-zone name Trust
import interface GigabitEthernet1/0/2
#
security-policy ip
rule 0 name ospflocalin
action pass
source-zone untrust
destination-zone local
service ospf
rule 1 name ospflocalout
action pass
source-zone local
destination-zone untrust
service ospf
rule 2 name trust-untrust
action pass
source-zone trust
destination-zone untrust
source-ip-subnet 3.3.3.0 255.255.255.0
destination-ip-subnet 2.2.2.0 255.255.255.0
rule 3 name untrust-trust
action pass
source-zone untrust
destination-zone trust
source-ip-subnet 2.2.2.0 255.255.255.0
destination-ip-subnet 3.3.3.0 255.255.255.0