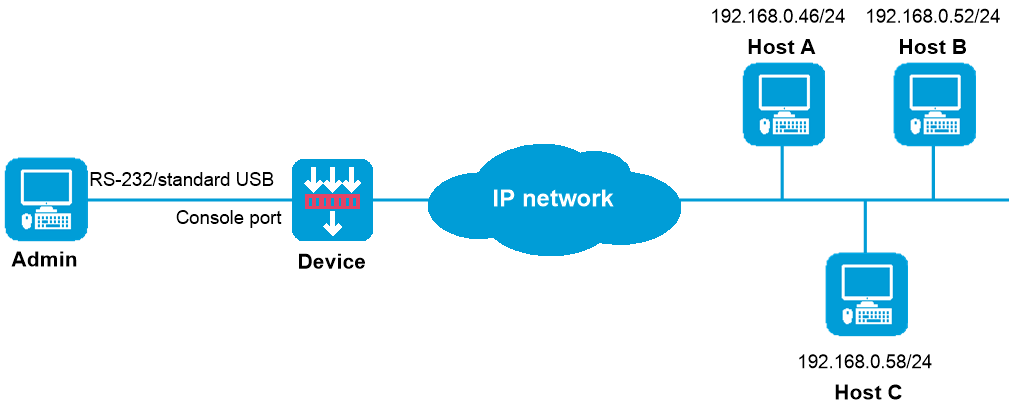
As shown in Figure 1, the device allows Telnet login only from hosts at 192.168.0.46/24 and 192.168.0.52/24. Username and password are required for Telnet login.
When the two hosts log in to the device with different usernames and the same authentication method, they have different access permissions. One has permissions to manage the device, and the other has permissions to execute the read commands of all features.
This configuration example was created and verified on R9071 of the M9000-AI-E8 device.
# Log in to the device through the console port, enter system view, and enable the Telnet server.
<Sysname> system-view
[Sysname] telnet server enable
# Enable scheme authentication for VTY lines 0 to 63.
[Sysname] line vty 0 63
[Sysname-line-vty0-63] authentication-mode scheme
[Sysname-line-vty0-63] quit
# Create local user userA, assign user role network-admin to the user, configure a user password, and remove the default user role from the user.
[Sysname] local-user userA class manage
New local user added.
[Sysname-luser-manage-userA] authorization-attribute user-role network-admin
[Sysname-luser-manage-userA] service-type telnet
[Sysname-luser-manage-userA] password simple User1@1234
[Sysname-luser-manage-userA] undo authorization-attribute user-role network-operator
[Sysname-luser-manage-userA] quit
# Create user role roleB, and allow the user role to access the read commands of all features.
[Sysname] role name roleB
[Sysname-role-roleB] rule 1 permit read feature
[Sysname-role-roleB] quit
# Create local user userB, configure a user password, assign user role roleB to the user, and remove the default user role from the user.
[Sysname] local-user userB class manage
New local user added.
[Sysname-luser-manage-userB] authorization-attribute user-role roleB
[Sysname-luser-manage-userB] service-type telnet
[Sysname-luser-manage-userB] password simple User2@1234
[Sysname-luser-manage-userB] undo authorization-attribute user-role network-operator
[Sysname-luser-manage-userB] quit
# Create an ACL and configure rules to permit only traffic from 192.168.0.46 and 192.168.0.52.
[Sysname] acl basic 2000
[Sysname-acl-ipv4-basic-2000] rule 1 permit source 192.168.0.46 0
[Sysname-acl-ipv4-basic-2000] rule 2 permit source 192.168.0.52 0
[Sysname-acl-ipv4-basic-2000] rule 3 deny source any
[Sysname-acl-ipv4-basic-2000] quit
# Apply ACL 2000 to the Telnet server to control Telnet login based on source IP addresses.
[Sysname] telnet server acl 2000
1. Use user account userA to Telnet to the device. Verify that you can manage and configure the device.
login: userA
Password:
******************************************************************************
* Copyright (c) 2004-2022 New H3C Technologies Co., Ltd. All rights reserved.*
* Without the owner's prior written consent, *
* no decompiling or reverse-engineering shall be allowed. *
******************************************************************************
<Sysname> ?
User view commands:
archer FPGA : archer
archive Archive configuration
backup Backup operation
blade Blade module
boot-loader Software image file management
bootrom Update/read/backup/restore bootrom
bootrom-access Bootrom access control
cd Change current directory
check Integrity check
clock Specify the system clock
copy Copy a file
debugging Enable system debugging functions
debugging-auto-off Automatically turn off all debugging
delete Delete a file
diagnostic Generic OnLine Diagnostics (GOLD) module
diagnostic-logfile Diagnostic log file configuration
dialer Specify Dial-on-Demand Routing(DDR) configuration
information
dir Display files and directories on the storage media
display Display current system information
erase Alias for 'delete'
exception Exception information configuration
exit Alias for 'quit'
---- More ----
2. Use user account userB to Telnet to the device. Verify that you can execute only the read commands of all features.
login: userB
Password:
******************************************************************************
* Copyright (c) 2004-2022 New H3C Technologies Co., Ltd. All rights reserved.*
* Without the owner's prior written consent, *
* no decompiling or reverse-engineering shall be allowed. *
******************************************************************************
<Sysname> ?
User view commands:
archer FPGA : archer
archive Archive configuration
backup Backup operation
blade Blade module
boot-loader Software image file management
bootrom Update/read/backup/restore bootrom
bootrom-access Bootrom access control
cd Change current directory
check Integrity check
clock Specify the system clock
copy Copy a file
debugging Enable system debugging functions
debugging-auto-off Automatically turn off all debugging
delete Delete a file
diagnostic Generic OnLine Diagnostics (GOLD) module
diagnostic-logfile Diagnostic log file configuration
dialer Specify Dial-on-Demand Routing(DDR) configuration
information
dir Display files and directories on the storage media
display Display current system information
erase Alias for 'delete'
exception Exception information configuration
exit Alias for 'quit'
---- More ----
<Sysname>
3. Verify that you cannot Telnet to the device from Host C.
#
telnet server enable
telnet server acl 2000
#
acl basic 2000
rule 1 permit source 192.168.0.46 0
rule 2 permit source 192.168.0.52 0
rule 3 deny
#
line vty 0 63
authentication-mode scheme
user-role network-operator
#
local-user userA class manage
password hash $h$6$3BcJwbpD4nbb4Pjd$fCTiXzLkjWHY0IsLI9E+1fV+WH4jEuu2Lf7Qa2Yog4/
1Z/ecgSXpecjuKxx4/hdRb92G+AZUTJK/AQJAmYVzKA==
service-type telnet
authorization-attribute user-role network-admin
#
local-user userB class manage
password hash $h$6$yvsoiG/zeU07hJ7u$31A5lXblIT86GEpK9wRfw2bJ38QHm+es6VEm4op/KYf
v1jGquN5te31wV0xQ1IZHL6Zv6/v6DcvMf2bp74gHNw==
service-type telnet
authorization-attribute user-role roleB
#
role name roleB
rule 1 permit read feature