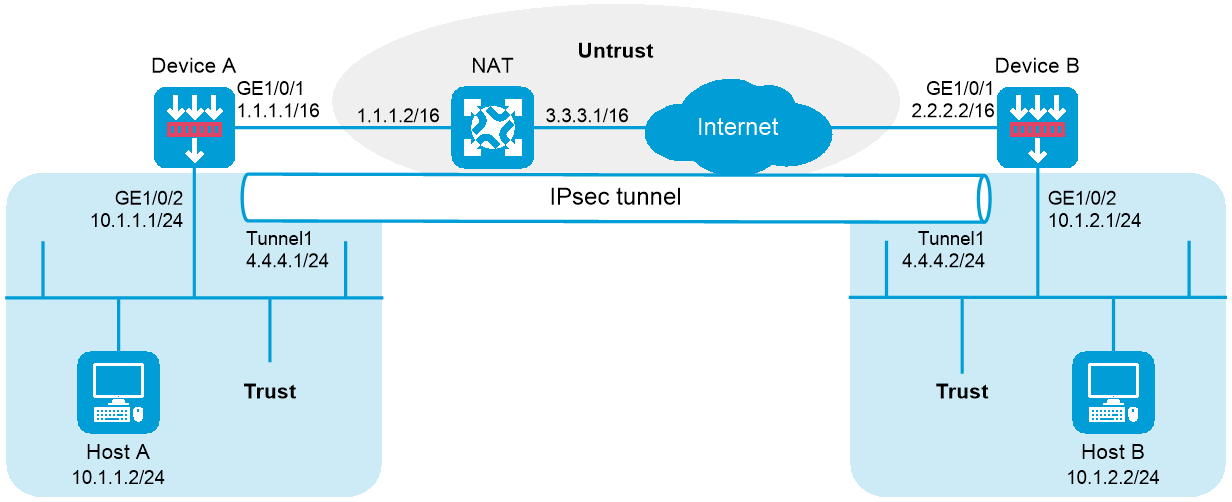
Device A is behind the NAT device. Hosts behind Device A use public IP address 3.3.3.1 to access the external network.
Configure IPsec tunnel interface-based IPsec on Device A and Device B to protect the traffic between subnet 10.1.1.0/24 and subnet 10.1.2.0/24.
Configure Device A and Device B to use the default IKEv2 proposal and the default IKEv2 policy in IKEv2 negotiation to set up IPsec SAs.
Configure the two devices to use the preshared key authentication method in IKEv2 negotiation phase 1.
Figure 1 Network diagram
This configuration example was created and verified on R9071 of the M9000-AI-E8 device.
1. Assign IP addresses to interfaces:
# Assign an IP address to interface GigabitEthernet 1/0/1.
<DeviceA> system-view
[DeviceA] interface gigabitethernet 1/0/1
[DeviceA-GigabitEthernet1/0/1] ip address 1.1.1.1 255.255.0.0
[DeviceA-GigabitEthernet1/0/1] quit
# Assign IP addresses to other interfaces in the same way. (Details not shown.)
2. Configure settings for routing.
This example configures static routes, and the next hop in the routes is 1.1.1.2.
[DeviceA] ip route-static 2.2.2.2 16 1.1.1.2
3. Add interfaces to security zones.
[DeviceA] security-zone name trust
[DeviceA-security-zone-Trust] import interface gigabitethernet 1/0/2
[DeviceA-security-zone-Trust] quit
[DeviceA] security-zone name untrust
[DeviceA-security-zone-Untrust] import interface gigabitethernet 1/0/1
[DeviceA-security-zone-Untrust] quit
4. Configure a security policy:
Configure rules to permit traffic between the Untrust and Local security zones, so the devices can set up an IPsec tunnel:
# Configure a rule named ipseclocalout to allow Device A to send IPsec negotiation packets to Device B.
[DeviceA] security-policy ip
[DeviceA-security-policy-ip] rule name ipseclocalout
[DeviceA-security-policy-ip-1-ipseclocalout] source-zone local
[DeviceA-security-policy-ip-1-ipseclocalout] destination-zone untrust
[DeviceA-security-policy-ip-1-ipseclocalout] source-ip-host 1.1.1.1
[DeviceA-security-policy-ip-1-ipseclocalout] destination-ip-host 2.2.2.2
[DeviceA-security-policy-ip-1-ipseclocalout] action pass
[DeviceA-security-policy-ip-1-ipseclocalout] quit
# Configure a rule named ipseclocalin to allow Device A to receive the IPsec negotiation packets sent from Device B.
[DeviceA-security-policy-ip] rule name ipseclocalin
[DeviceA-security-policy-ip-2-ipseclocalin] source-zone untrust
[DeviceA-security-policy-ip-2-ipseclocalin] destination-zone local
[DeviceA-security-policy-ip-2-ipseclocalin] source-ip-host 2.2.2.2
[DeviceA-security-policy-ip-2-ipseclocalin] destination-ip-host 1.1.1.1
[DeviceA-security-policy-ip-2-ipseclocalin] action pass
[DeviceA-security-policy-ip-2-ipseclocalin] quit
Configure rules to permit the traffic between Host A and Host B:
# Configure a rule named trust-untrust to permit the packets from Host A to Host B.
[DeviceA-security-policy-ip] rule name trust-untrust
[DeviceA-security-policy-ip-3-trust-untrust] source-zone trust
[DeviceA-security-policy-ip-3-trust-untrust] destination-zone untrust
[DeviceA-security-policy-ip-3-trust-untrust] source-ip-subnet 10.1.1.0 24
[DeviceA-security-policy-ip-3-trust-untrust] destination-ip-subnet 10.1.2.0 24
[DeviceA-security-policy-ip-3-trust-untrust] action pass
[DeviceA-security-policy-ip-3-trust-untrust] quit
# Configure a rule named untrust-trust to permit the packets from Host B to Host A.
[DeviceA-security-policy-ip] rule name untrust-trust
[DeviceA-security-policy-ip-4-untrust-trust] source-zone untrust
[DeviceA-security-policy-ip-4-untrust-trust] destination-zone trust
[DeviceA-security-policy-ip-4-untrust-trust] source-ip-subnet 10.1.2.0 24
[DeviceA-security-policy-ip-4-untrust-trust] destination-ip-subnet 10.1.1.0 24
[DeviceA-security-policy-ip-4-untrust-trust] action pass
[DeviceA-security-policy-ip-4-untrust-trust] quit
[DeviceA-security-policy-ip] quit
5. Configure an IPsec transform set to specify the packet encapsulation mode, security protocols, and algorithms.
The IPsec transform set settings at both sides of the IPsec tunnel must be the same.
[DeviceA] ipsec transform-set transform1
[DeviceA-ipsec-transform-set-transform1] protocol esp
[DeviceA-ipsec-transform-set-transform1] esp encryption-algorithm 3des-cbc
[DeviceA-ipsec-transform-set-transform1] esp authentication-algorithm md5
[DeviceA-ipsec-transform-set-transform1] quit
6. Configure an IKEv2 keychain to specify the key information used for IKEv2 communication.
The preshared key used by both sides of the communication must be the same.
[DeviceA] ikev2 keychain keychain1
[DeviceA-ikev2-keychain-keychain1] peer peer1
[DeviceA-ikev2-keychain-keychain1-peer-peer1] address 2.2.2.2 16
[DeviceA-ikev2-keychain-keychain1-peer-peer1] identity address 2.2.2.2
[DeviceA-ikev2-keychain-keychain1-peer-peer1] pre-shared-key plaintext 123
[DeviceA-ikev2-keychain-keychain1-peer-peer1] quit
[DeviceA-ikev2-keychain-keychain1] quit
7. Configure an IKEv2 profile to specify the security parameters used for setting up IKEv2 SAs.
[DeviceA] ikev2 profile profile1
[DeviceA-ikev2-profile-profile1] keychain keychain1
[DeviceA-ikev2-profile-profile1] identity local fqdn www.devicea.com
[DeviceA-ikev2-profile-profile1] match remote identity address 2.2.2.2 255.255.0.0
[DeviceA-ikev2-profile-profile1] authentication-method local pre-share
[DeviceA-ikev2-profile-profile1] authentication-method remote pre-share
[DeviceA-ikev2-profile-profile1] quit
8. Configure an IPsec profile to establish an IPsec tunnel to protect the specified data:
[DeviceA] ipsec profile abc isakmp
[DeviceA-ipsec-profile-isakmp-abc] transform-set transform1
[DeviceA-ipsec-profile-isakmp-abc] ikev2-profile profile1
[DeviceA-ipsec-profile-isakmp-abc] quit
9. Configure an IPsec tunnel interface, which encapsulates the traffic to be protected with IPsec:
# Create an IPsec tunnel interface, and apply the IPsec profile.
[DeviceA] interface tunnel 1 mode ipsec
[DeviceA-Tunnel1] ip address 4.4.4.1 255.255.255.0
[DeviceA-Tunnel1] source 1.1.1.1
[DeviceA-Tunnel1] destination 2.2.2.2
[DeviceA-Tunnel1] tunnel protection ipsec profile abc
[DeviceA-Tunnel1] quit
# Add the IPsec tunnel interface to security zone Untrust.
[DeviceA] security-zone name untrust
[DeviceA-security-zone-Untrust] import interface tunnel 1
[DeviceA-security-zone-Untrust] quit
# Configure a static route to direct the traffic to be protected to the IPsec tunnel interface.
[DeviceA] ip route-static 10.1.2.0 255.255.255.0 tunnel 1
1. Assign IP addresses to interfaces:
# Assign an IP address to interface GigabitEthernet 1/0/1.
<DeviceB> system-view
[DeviceB] interface gigabitethernet 1/0/1
[DeviceB-GigabitEthernet1/0/1] ip address 2.2.2.2 255.255.0.0
[DeviceB-GigabitEthernet1/0/1] quit
# Assign IP addresses to other interfaces in the same way. (Details not shown.)
2. Configure settings for routing.
This example configures static routes, and the next hop in the routes is 2.2.2.1.
[DeviceB] ip route-static 3.3.3.1 16 2.2.2.1
3. Add interfaces to security zones.
[DeviceB] security-zone name trust
[DeviceB-security-zone-Trust] import interface gigabitethernet 1/0/2
[DeviceB-security-zone-Trust] quit
[DeviceB] security-zone name untrust
[DeviceB-security-zone-Untrust] import interface gigabitethernet 1/0/1
[DeviceB-security-zone-Untrust] quit
4. Configure a security policy:
Configure rules to permit traffic between the Untrust and Local security zones, so the devices can set up an IPsec tunnel:
# Configure a rule named ipseclocalout to allow Device B to send IPsec negotiation packets to Device A.
[DeviceB] security-policy ip
[DeviceB-security-policy-ip] rule name ipseclocalout
[DeviceB-security-policy-ip-1-ipseclocalout] source-zone local
[DeviceB-security-policy-ip-1-ipseclocalout] destination-zone untrust
[DeviceB-security-policy-ip-1-ipseclocalout] source-ip-host 2.2.2.2
[DeviceB-security-policy-ip-1-ipseclocalout] destination-ip-host 1.1.1.1
[DeviceB-security-policy-ip-1-ipseclocalout] action pass
[DeviceB-security-policy-ip-1-ipseclocalout] quit
# Configure a rule named ipseclocalin to allow Device B to receive the IPsec negotiation packets sent from Device A.
[DeviceB-security-policy-ip] rule name ipseclocalin
[DeviceB-security-policy-ip-2-ipseclocalin] source-zone untrust
[DeviceB-security-policy-ip-2-ipseclocalin] destination-zone local
[DeviceB-security-policy-ip-2-ipseclocalin] source-ip-host 1.1.1.1
[DeviceB-security-policy-ip-2-ipseclocalin] destination-ip-host 2.2.2.2
[DeviceB-security-policy-ip-2-ipseclocalin] action pass
[DeviceB-security-policy-ip-2-ipseclocalin] quit
Configure rules to permit traffic between Host B and Host A:
# Configure a rule named trust-untrust to permit the packets from Host B to Host A.
[DeviceB-security-policy-ip] rule name trust-untrust
[DeviceB-security-policy-ip-3-trust-untrust] source-zone trust
[DeviceB-security-policy-ip-3-trust-untrust] destination-zone untrust
[DeviceB-security-policy-ip-3-trust-untrust] source-ip-subnet 10.1.2.0 24
[DeviceB-security-policy-ip-3-trust-untrust] destination-ip-subnet 10.1.1.0 24
[DeviceB-security-policy-ip-3-trust-untrust] action pass
[DeviceB-security-policy-ip-3-trust-untrust] quit
# Configure a rule named untrust-trust to permit the packets from Host A to Host B.
[DeviceB-security-policy-ip] rule name untrust-trust
[DeviceB-security-policy-ip-4-untrust-trust] source-zone untrust
[DeviceB-security-policy-ip-4-untrust-trust] destination-zone trust
[DeviceB-security-policy-ip-4-untrust-trust] source-ip-subnet 10.1.1.0 24
[DeviceB-security-policy-ip-4-untrust-trust] destination-ip-subnet 10.1.2.0 24
[DeviceB-security-policy-ip-4-untrust-trust] action pass
[DeviceB-security-policy-ip-4-untrust-trust] quit
[DeviceB-security-policy-ip] quit
5. Configure an IPsec transform set to specify the packet encapsulation mode, security protocols, and algorithms.
The IPsec transform set settings at both sides of the IPsec tunnel must be the same.
[DeviceB] ipsec transform-set transform1
[DeviceB-ipsec-transform-set-transform1] protocol esp
[DeviceB-ipsec-transform-set-transform1] esp encryption-algorithm 3des-cbc
[DeviceB-ipsec-transform-set-transform1] esp authentication-algorithm md5
[DeviceB-ipsec-transform-set-transform1] quit
6. Configure an IKEv2 keychain to specify the key information used for IKEv2 communication.
[DeviceB]ikev2 keychain keychain1
[DeviceB-ikev2-keychain-keychain1] peer peer1
[DeviceB-ikev2-keychain-keychain1-peer-peer1] address 3.3.3.1 16
[DeviceB-ikev2-keychain-keychain1-peer-peer1] identity address 3.3.3.1
[DeviceB-ikev2-keychain-keychain1-peer-peer1] pre-shared-key plaintext 123
[DeviceB-ikev2-keychain-keychain1-peer-peer1] quit
[DeviceB-ikev2-keychain-keychain1] quit
7. Configure an IKEv2 profile to specify the security parameters used for setting up IKEv2 SAs.
[DeviceB] ikev2 profile profile1
[DeviceB-ikev2-profile-profile1] keychain keychain1
[DeviceB-ikev2-profile-profile1] match remote identity fqdn www.devicea.com
[DeviceB-ikev2-profile-profile1] authentication-method local pre-share
[DeviceB-ikev2-profile-profile1] authentication-method remote pre-share
[DeviceB-ikev2-profile-profile1] quit
8. Configure an IPsec profile to establish an IPsec tunnel to protect the specified data:
[DeviceB] ipsec profile abc isakmp
[DeviceB-ipsec-profile-isakmp-abc] transform-set transform1
[DeviceB-ipsec-profile-isakmp-abc] ikev2-profile profile1
[DeviceB-ipsec-profile-isakmp-abc] quit
9. Configure an IPsec tunnel interface, which encapsulates the traffic to be protected with IPsec:
# Create an IPsec tunnel interface, and apply the IPsec profile.
[DeviceB] interface tunnel 1 mode ipsec
[DeviceB-Tunnel1] ip address 4.4.4.2 255.255.255.0
[DeviceB-Tunnel1] source 2.2.2.2
[DeviceB-Tunnel1] destination 3.3.3.1
[DeviceB-Tunnel1] tunnel protection ipsec profile abc
[DeviceB-Tunnel1] quit
# Add the IPsec tunnel interface to security zone Untrust.
[DeviceB] security-zone name untrust
[DeviceB-security-zone-Untrust] import interface tunnel 1
[DeviceB-security-zone-Untrust] quit
# Configure a static route to direct the traffic to be protected to the IPsec tunnel interface.
[DeviceB] ip route-static 10.1.1.0 255.255.255.0 tunnel 1
After the configuration is completed, Device A will automatically initiate IKE negotiation with Device B. After IKE negotiation succeeds, the tunnel interface will come up and traffic between two subnets will be IPsec-protected. This example uses Device A to verify the configuration.
# Display brief IP configuration for interfaces on Device A.
[DeviceA] display ip interface brief
*down: administratively down
(s): spoofing (l): loopback
Interface Physical Protocol IP address/Mask VPN instance Description
GE1/0/1 up up 1.1.1.1/16 -- --
GE1/0/2 up up 10.1.1.1/24 -- --
Tun1 up up 4.4.4.1/24 -- --
# Display tunnel interface information on Device A.
[DeviceA] display interface Tunnel 1
Tunnel1
Current state: UP
Line protocol state: UP
Description: Tunnel1 Interface
Bandwidth: 64 kbps
Maximum transmission unit: 1444
Internet address: 4.4.4.1/24 (primary)
Tunnel source 1.1.1.1, destination 2.2.2.2
Tunnel TTL 255
Tunnel protocol/transport IPsec/IP
Output queue - Urgent queuing: Size/Length/Discards 0/100/0
Output queue - Protocol queuing: Size/Length/Discards 0/500/0
Output queue - FIFO queuing: Size/Length/Discards 0/75/0
Last clearing of counters: Never
Last 300 seconds input rate: 0 bytes/sec, 0 bits/sec, 0 packets/sec
Last 300 seconds output rate: 0 bytes/sec, 0 bits/sec, 0 packets/sec
Input: 0 packets, 0 bytes, 0 drops
Output: 0 packets, 0 bytes, 0 drops
# Display IPsec SAs on Device A.
[DeviceA] display ipsec sa
-------------------------------
Interface: Tunnel1
-------------------------------
-----------------------------
IPsec profile: abc
Mode: ISAKMP
-----------------------------
Tunnel id: 0
Encapsulation mode: tunnel
Perfect Forward Secrecy:
Transmitting entity: Initiator
Path MTU: 1388
Tunnel:
local address/port: 1.1.1.1/500
remote address/port: 2.2.2.2/500
Flow:
sour addr: 0.0.0.0/0.0.0.0 port: 0 protocol: ip
dest addr: 0.0.0.0/0.0.0.0 port: 0 protocol: ip
[Inbound ESP SAs]
SPI: 2701952073 (0xa10c8449)
Connection ID: 4294967296
Transform set: ESP-ENCRYPT-SM1-CBC-128 ESP-AUTH-SM3
SA duration (kilobytes/sec): 1843200/3600
SA remaining duration (kilobytes/sec): 1843200/3180
Max received sequence-number: 0
Anti-replay check enable: Y
Anti-replay window size: 64
UDP encapsulation used for NAT traversal: N
Status: Active
[Outbound ESP SAs]
SPI: 3607077598 (0xd6ffa2de)
Connection ID: 12884901889
Transform set: ESP-ENCRYPT-SM1-CBC-128 ESP-AUTH-SM3
SA duration (kilobytes/sec): 1843200/3600
SA remaining duration (kilobytes/sec): 1843200/3180
Max sent sequence-number: 0
UDP encapsulation used for NAT traversal: N
Status: Active
# Verify that a private IP address in subnet 10.1.1.0/24 can ping a private IP address in subnet 10.1.2.0/24 successfully.
[DeviceA] ping -a 10.1.1.2 10.1.2.2
Ping 10.1.2.1 (10.1.2.1) from 10.1.1.1: 56 data bytes, press CTRL_C to break
56 bytes from 10.1.2.1: icmp_seq=0 ttl=255 time=1.000 ms
56 bytes from 10.1.2.1: icmp_seq=1 ttl=255 time=1.000 ms
56 bytes from 10.1.2.1: icmp_seq=2 ttl=255 time=0.000 ms
56 bytes from 10.1.2.1: icmp_seq=3 ttl=255 time=1.000 ms
56 bytes from 10.1.2.1: icmp_seq=4 ttl=255 time=0.000 ms
--- Ping statistics for 10.1.2.1 ---
5 packet(s) transmitted, 5 packet(s) received, 0.0% packet loss
round-trip min/avg/max/std-dev = 0.000/0.600/1.000/0.490 ms
Device A
#
interface GigabitEthernet1/0/1
ip address 1.1.1.1 255.255.0.0
#
interface GigabitEthernet1/0/2
ip address 10.1.1.1 255.255.255.0
#
interface Tunnel1 mode ipsec
ip address 4.4.4.1 255.255.255.0
source 1.1.1.1
destination 2.2.2.2
tunnel protection ipsec profile abc
#
security-zone name Trust
import interface GigabitEthernet1/0/2
#
security-zone name Untrust
import interface GigabitEthernet1/0/1
import interface Tunnel1
#
ip route-static 2.2.0.0 16 1.1.1.2
ip route-static 10.1.2.0 24 Tunnel1
#
ipsec transform-set transform1
encapsulation-mode tunnel
protocol esp
esp encryption-algorithm 3des-cbc
esp authentication-algorithm md5
#
ipsec profile abc isakmp
transform-set transform1
ikev2-profile profile1
#
ikev2 keychain keychain1
peer peer1
address 2.2.2.2 255.255.0.0
identity address 2.2.2.2
pre-shared-key plaintext 123
#
ikev2 profile profile1
authentication-method local pre-share
authentication-method remote pre-share
keychain keychain1
identity local fqdn www.devicea.com
match remote identity address 2.2.2.2 255.255.0.0
#
security-policy ip
rule 0 name ipseclocalout
action pass
source-zone local
destination-zone untrust
source-ip-host 1.1.1.1
destination-ip-host 2.2.2.2
rule 1 name ipseclocalin
action pass
source-zone untrust
destination-zone local
source-ip-host 2.2.2.2
destination-ip-host 1.1.1.1
rule 2 name trust-untrust
action pass
source-zone trust
destination-zone untrust
source-ip-subnet 10.1.1.0 255.255.255.0
destination-ip-subnet 10.1.2.0 255.255.255.0
rule 3 name untrust-trust
action pass
source-zone untrust
destination-zone trust
source-ip-subnet 10.1.2.0 255.255.255.0
destination-ip-subnet 10.1.1.0 255.255.255.0
#
Device B
#
interface GigabitEthernet1/0/1
ip address 2.2.2.2 255.255.0.0
#
interface GigabitEthernet1/0/2
ip address 10.1.2.1 255.255.255.0
#
interface Tunnel1 mode ipsec
ip address 4.4.4.2 255.255.255.0
source 2.2.2.2
destination 3.3.3.1
tunnel protection ipsec profile abc
#
security-zone name Trust
import interface GigabitEthernet1/0/2
#
security-zone name Untrust
import interface GigabitEthernet1/0/1
import interface Tunnel1
#
ip route-static 3.3.0.0 16 2.2.2.1
ip route-static 10.1.1.0 24 Tunnel1
#
ipsec transform-set transform1
encapsulation-mode tunnel
protocol esp
esp encryption-algorithm 3des-cbc
esp authentication-algorithm md5
#
ipsec profile abc isakmp
transform-set transform1
ikev2-profile profile1
#
ikev2 keychain keychain1
peer peer1
address 3.3.3.1 255.255.0.0
identity address 3.3.3.1
pre-shared-key plaintext 123
#
ikev2 profile profile1
authentication-method local pre-share
authentication-method remote pre-share
keychain keychain1
match remote identity fqdn www.devicea.com
#
security-policy ip
rule 0 name ipseclocalout
action pass
source-zone local
destination-zone untrust
source-ip-host 2.2.2.2
destination-ip-host 3.3.3.1
rule 1 name ipseclocalin
action pass
source-zone untrust
destination-zone local
source-ip-host 3.3.3.1
destination-ip-host 2.2.2.2
rule 2 name trust-untrust
action pass
source-zone trust
destination-zone untrust
source-ip-subnet 10.1.2.0 255.255.255.0
destination-ip-subnet 10.1.1.0 255.255.255.0
rule 3 name untrust-trust
action pass
source-zone untrust
destination-zone trust
source-ip-subnet 10.1.1.0 255.255.255.0
destination-ip-subnet 10.1.2.0 255.255.255.0