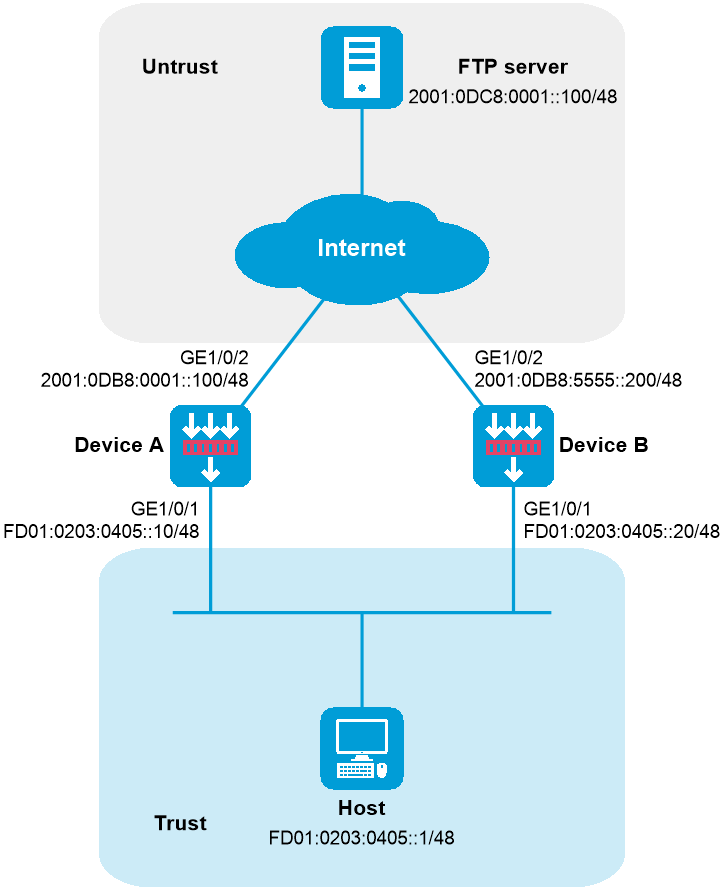
As shown in Figure 1, internal users use IPv6 prefix FD01:0203:0405::/48 and the internal IPv6 address is not routable on the Internet.
Device A and Device B are connected to the same internal network but different external networks. Configure IPv6 source prefix translation to translate the internal IPv6 prefix FD01:0203:0405::/48 to different external prefixes so that the internal address can be translated to two external addresses.
This configuration example was created and verified on E8371 of the F5000-AI160 device.
1. Configure Device A.
Assign IPv6 addresses to interfaces:
# Assign an IPv6 address to interface GigabitEthernet 1/0/1.
<DeviceA> system-view
[DeviceA] interface gigabitethernet 1/0/1
[DeviceA-GigabitEthernet1/0/1] ipv6 address FD01:0203:0405::10 48
[DeviceA-GigabitEthernet1/0/1] quit
# Assign IPv6 addresses to other interfaces in the same way. (Details not shown.)
Configure settings for routing.
This example configures a static route, and the next hop in the route is 2001:0DB8:0001::11.
[DeviceA] ipv6 route-static 2001:0DC8:0001::100 48 2001:0DB8:0001::11
Add interfaces to security zones.
[DeviceA] security-zone name trust
[DeviceA-security-zone-Trust] import interface gigabitethernet 1/0/1
[DeviceA-security-zone-Trust] quit
[DeviceA] security-zone name untrust
[DeviceA-security-zone-Untrust] import interface gigabitethernet 1/0/2
[DeviceA-security-zone-Untrust] quit
Configure a security policy:
# Configure a rule named trust-untrust to permit the packets from the host to the FTP server.
[DeviceA] security-policy ipv6
[DeviceA-security-policy-ipv6] rule name trust-untrust
[DeviceA-security-policy-ipv6-1-trust-untrust] source-zone trust
[DeviceA-security-policy-ipv6-1-trust-untrust] destination-zone untrust
[DeviceA-security-policy-ipv6-1-trust-untrust] source-ip-host FD01:0203:0405::1
[DeviceA-security-policy-ipv6-1-trust-untrust] destination-ip-host 2001:0DC8:0001::100
[DeviceA-security-policy-ipv6-1-trust-untrust] action pass
[DeviceA-security-policy-ipv6-1-trust-untrust] quit
[DeviceA-security-policy-ipv6] quit
Configure IPv6 source prefix translation:
# Configure an IPv6 source prefix mapping from FD01:0203:0405::/48 to 2001:0DF8:0001::/48.
[DeviceA] interface gigabitethernet 1/0/2
[DeviceA-GigabitEthernet1/0/2] nat66 prefix source fd01:0203:0405:: 48 2001:0df8:0001:: 48
[DeviceA-GigabitEthernet1/0/2] quit
2. Configure Device B.
Assign IPv6 addresses to interfaces:
# Assign an IPv6 address to interface GigabitEthernet 1/0/1.
<DeviceB> system-view
[DeviceB] interface gigabitethernet 1/0/1
[DeviceB-GigabitEthernet1/0/1] ipv6 address FD01:0203:0405::20 48
[DeviceB-GigabitEthernet1/0/1] quit
# Assign IPv6 addresses to other interfaces in the same way. (Details not shown.)
Configure settings for routing.
This example configures a static route, and the next hop in the route is 2001:0DB8:5555::11.
[DeviceB] ipv6 route-static 2001:0DC8:0001::100 48 2001:0DB8:5555::11
Add interfaces to security zones.
[DeviceB] security-zone name trust
[DeviceB-security-zone-Trust] import interface gigabitethernet 1/0/1
[DeviceB-security-zone-Trust] quit
[DeviceB] security-zone name untrust
[DeviceB-security-zone-Untrust] import interface gigabitethernet 1/0/2
[DeviceB-security-zone-Untrust] quit
Configure a security policy:
# Configure a rule named trust-untrust to permit the packets from the host to the FTP server.
[DeviceB] security-policy ipv6
[DeviceB-security-policy-ipv6] rule name trust-untrust
[DeviceB-security-policy-ipv6-1-trust-untrust] source-zone trust
[DeviceB-security-policy-ipv6-1-trust-untrust] destination-zone untrust
[DeviceB-security-policy-ipv6-1-trust-untrust] source-ip-host FD01:0203:0405::1
[DeviceB-security-policy-ipv6-1-trust-untrust] destination-ip-host 2001:0DC8:0001::100
[DeviceB-security-policy-ipv6-1-trust-untrust] action pass
[DeviceB-security-policy-ipv6-1-trust-untrust] quit
[DeviceB-security-policy-ipv6] quit
Configure IPv6 source prefix translation:
# Configure an IPv6 source prefix mapping from FD01:0203:0405::/48 to 2001:0DE8:0001::/48.
[DeviceB] interface gigabitethernet 1/0/2
[DeviceB-GigabitEthernet1/0/2] nat66 prefix source fd01:0203:0405:: 48 2001:0de8:0001:: 48
[DeviceB-GigabitEthernet1/0/2] quit
# Verify that the internal host can access the FTP server through Device A or Device B. The internal prefix is mapped to different external prefixes and external prefixes are mapped to the same internal prefix on the two NAT66 devices.
# Verify NAT66 configurations on Device A.
[DeviceA] display nat66 all
NAT66 source information:
Totally 1 source rules.
Interface(outbound): GigabitEthernet1/0/2
Original prefix/prefix-length: FD01:203:405::/48
Translated prefix/prefix-length: 2001:DF8:1::/48
# Verify NAT66 configurations on Device B.
[DeviceB] display nat66 all
NAT66 source information:
Totally 1 source rules.
Interface(outbound): GigabitEthernet1/0/2
Original prefix/prefix-length: FD01:203:405::/48
Translated prefix/prefix-length: 2001:DE8:1::/48
# Verify that NAT66 sessions are established on Device A.
[DeviceA] display nat66 session verbose
Slot 1:
Initiator:
Source IP/port: FD01:203:405::1/35990
Destination IP/port: 2001:DC8:1::100/21
VPN instance/VLAN ID/Inline ID: -/-/-
Protocol: TCP(6)
Inbound interface: GigabitEthernet1/0/1
Source security zone: Trust
Responder:
Source IP/port: 2001:DC8:1::100/21
Destination IP/port: 2001:DF8:1:D50F::1/35990
VPN instance/VLAN ID/Inline ID: -/-/-
Protocol: TCP(6)
Inbound interface: GigabitEthernet1/0/2
Source security zone: Trust
State: TCP_ESTABLISHED
Application: FTP
Rule ID: 0
Rule name: aaa
Start time: 2021-10-31 14:47:44 TTL: 3584s
Initiator->Responder: 0 packets 0 bytes
Responder->Initiator: 0 packets 0 bytes
Total sessions found: 1
# Verify that NAT66 sessions are established on Device B.
[DeviceB] display nat66 session verbose
Slot 1:
Initiator:
Source IP/port: FD01:203:405::1/35992
Destination IP/port: 2001:DC8:1::100/21
VPN instance/VLAN ID/Inline ID: -/-/-
Protocol: TCP(6)
Inbound interface: GigabitEthernet1/0/1
Source security zone: Trust
Responder:
Source IP/port: 2001:DC8:1::100/21
Destination IP/port: 2001:DE8:1:D51F::1/35992
VPN instance/VLAN ID/Inline ID: -/-/-
Protocol: TCP(6)
Inbound interface: GigabitEthernet1/0/2
Source security zone: Trust
State: TCP_ESTABLISHED
Application: FTP
Rule ID: 0
Rule name: aaa
Start time: 2021-10-31 14:50:03 TTL: 3594s
Initiator->Responder: 0 packets 0 bytes
Responder->Initiator: 0 packets 0 bytes
Total sessions found: 1
Device A
#
interface GigabitEthernet1/0/1
ipv6 address FD01:203:405::10/48
#
interface GigabitEthernet1/0/2
nat66 prefix source FD01:203:405:: 48 2001:DF8:1:: 48
ipv6 address 2001:DB8:1::100/48
#
security-zone name Trust
import interface GigabitEthernet1/0/1
#
security-zone name Untrust
import interface GigabitEthernet1/0/2
#
ipv6 route-static 2001:DC8:1:: 48 2001:DB8:1::11
#
security-policy ipv6
rule 0 name trust-untrust
action pass
source-zone trust
destination-zone untrust
source-ip-host FD01:203:405::1
destination-ip-host 2001:DC8:1::100
#
Device B
#
interface GigabitEthernet1/0/1
ipv6 address FD01:203:405::20/48
#
interface GigabitEthernet1/0/2
nat66 prefix source FD01:203:405:: 48 2001:DE8:1:: 48
ipv6 address 2001:DB8:5555::200/48
#
security-zone name Trust
import interface GigabitEthernet1/0/1
#
security-zone name Untrust
import interface GigabitEthernet1/0/2
#
ipv6 route-static 2001:DC8:1:: 48 2001:DB8:5555::11
#
security-policy ipv6
rule 0 name trust-untrust
action pass
source-zone trust
destination-zone untrust
source-ip-host FD01:203:405::1
destination-ip-host 2001:DC8:1::100