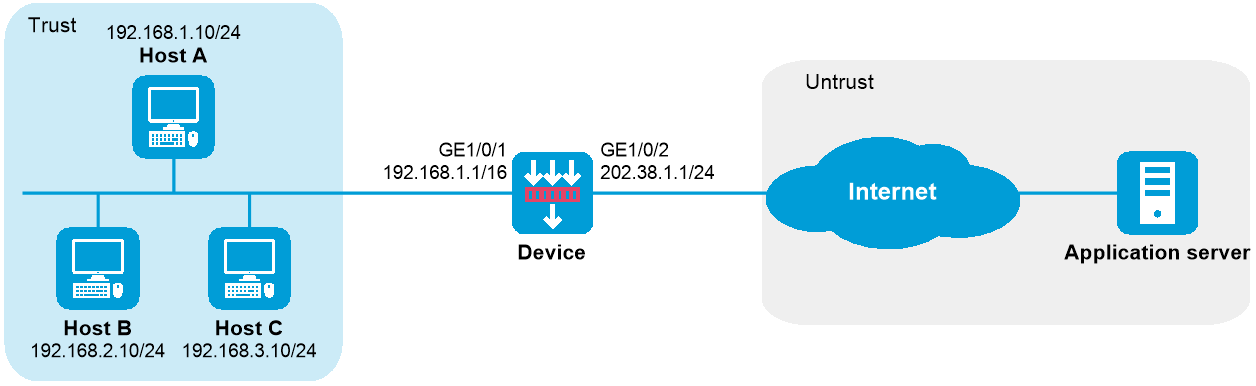
As shown in Figure 1, a company uses private IP address on network 192.168.0.0/16 and public IP addresses 202.38.1.2 and 202.38.1.3. Configure dynamic NAT444 to meet the following requirements:
Only users on subnet 192.168.1.0/24 can use public IP addresses 202.38.1.2 and 202.38.1.3 to access the Internet.
The port range for the public IP addresses is 1024 to 65535.
The port block size is 300.
If the ports in the assigned port block are all used, extend another port block for users.
This configuration example was created and verified on E8371 of the F5000-AI160 device.
# Assign IP addresses to interfaces and configure routes, security zones, zone pairs, and interzone policies. Make sure the network connections are available. (Details not shown.)
# Create NAT address group 0.
<Device> system-view
[Device] nat address-group 0
# Add public IP addresses 202.38.1.2 and 202.38.1.3 to the NAT address group.
[Device-address-group-0] address 202.38.1.2 202.38.1.3
# Configure the port range as 1024 to 65535.
[Device-address-group-0] port-range 1024 65535
# Set the port block size to 300 and the extended port block number to 1.
[Device-address-group-0] port-block block-size 300 extended-block-number 1
[Device-address-group-0] quit
# Configure an ACL to identify packets from subnet 192.168.1.0/24.
[Device] acl basic 2000
[Device-acl-ipv4-basic-2000] rule permit source 192.168.1.0 0.0.0.255
[Device-acl-ipv4-basic-2000] quit
# Configure outbound NAT on GigabitEthernet 1/0/2.
[Device] interface gigabitethernet 1/0/2
[Device-GigabitEthernet1/0/2] nat outbound 2000 address-group 0
[Device-GigabitEthernet1/0/2] quit
# Verify that Host A can access external servers, but Host B and Host C cannot. (Details not shown.)
# Display all NAT configurations and statistics.
[Device] display nat all
NAT address group information:
Totally 1 NAT address groups.
Address group ID: 0
Port range: 1024-65535
Port block size: 300
Extended block number: 1
Address information:
Start address End address
202.38.1.2 202.38.1.3
Exclude address information:
Start address End address
--- ---
NAT outbound information:
Totally 1 NAT outbound rules.
Interface: GigabitEthernet1/0/2
ACL: 2000
Address group ID: 0
Port-preserved: N NO-PAT: N Reversible: N
Config status: Active
NAT logging:
Log enable : Disabled
Flow-begin : Disabled
Flow-end : Disabled
Flow-active : Disabled
Port-block-assign : Disabled
Port-block-withdraw : Disabled
Alarm : Disabled
NO-PAT IP usage : Disabled
NAT mapping behavior:
Mapping mode : Address and Port-Dependent
ACL : ---
Config status: Active
NAT ALG:
DNS : Enabled
FTP : Enabled
H323 : Disabled
ICMP-ERROR : Enabled
ILS : Disabled
MGCP : Disabled
NBT : Disabled
PPTP : Enabled
RTSP : Enabled
RSH : Disabled
SCCP : Disabled
SCTP : Disabled
SIP : Disabled
SQLNET : Disabled
TFTP : Disabled
XDMCP : Disabled
Static NAT load balancing: Disabled
NAT link-switch recreate-session: Disabled
NAT configuration-for-new-connection: Disabled
# Display NAT statistics.
[Device] display nat statistics
Total session entries: 1
Session creation rate: 0
Total EIM entries: 0
Total inbound NO-PAT entries: 0
Total outbound NO-PAT entries: 0
Total static port block entries: 0
Total dynamic port block entries: 430
Active static port block entries: 0
Active dynamic port block entries: 1
# Display the dynamic port block entries.
[Device] display nat port-block dynamic
Slot 1:
Local VPN Local IP Global IP Port block Connections
--- 192.168.1.10 202.38.1.2 65224-65523 1
Total mappings found: 1
#
nat address-group 0
port-range 1024 65535
port-block block-size 300 extended-block-number 1
address 202.38.1.2 202.38.1.3
#
interface GigabitEthernet1/0/1
ip address 192.168.1.1 255.255.0.0
#
interface GigabitEthernet1/0/2
ip address 202.38.1.1 255.255.255.0
nat outbound 2000 address-group 0
#
security-zone name Trust
import interface GigabitEthernet1/0/1
#
security-zone name Untrust
import interface GigabitEthernet1/0/2
#
acl basic 2000
rule 0 permit source 192.168.1.0 0.0.0.255
#
security-policy ip
rule 0 name trust-untrust
action pass
source-zone trust
destination-zone untrust
rule 1 name untrust-trust
action pass
source-zone untrust
destination-zone trust