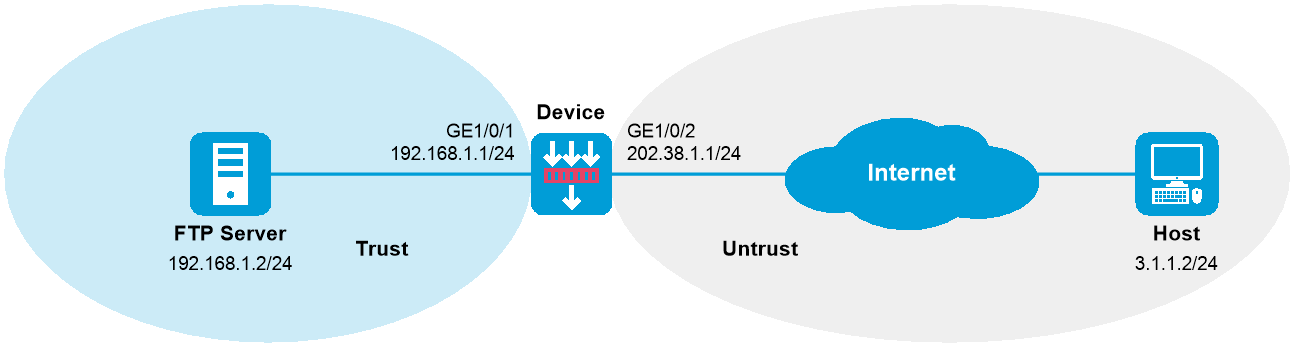
As shown in Figure 1, a company provides FTP services to external users through an FTP server by using the public IP address 202.38.1.1/24. The private IP address of the FTP server is 192.168.1.2/24.
Configure bandwidth management to use the private IP address after DNAT to limit the total bandwidth to 30720 kbps for all external hosts to access the FTP server.
Figure 1 Network diagram
This configuration example was created and verified on E8371 of the F5000-AI160 device.
1. Assign IP addresses to interfaces:
# Assign an IP address to interface GigabitEthernet 1/0/1.
<Device> system-view
[Device] interface gigabitethernet 1/0/1
[Device-GigabitEthernet1/0/1] ip address 10.1.1.1 255.255.255.0
[Device-GigabitEthernet1/0/1] quit
# Assign IP addresses to other interfaces in the same way. (Details not shown.)
2. Configure settings for routing.
This example configures static routes, and the next hop in the routes is 202.38.1.3.
[Device] ip route-static 3.1.1.2 24 202.38.1.3
3. Add interfaces to security zones.
[Device] security-zone name trust
[Device-security-zone-Trust] import interface gigabitethernet 1/0/1
[Device-security-zone-Trust] quit
[Device] security-zone name untrust
[Device-security-zone-Untrust] import interface gigabitethernet 1/0/2
[Device-security-zone-Untrust] quit
4. Configure a security policy:
# Configure a rule named untrust-trust to allow the hosts in the untrust security zone to access the FTP server in the trust security zone.
[Device] security-policy ip
[Device-security-policy-ip] rule name untrust-trust
[Device-security-policy-ip-1-untrust-trust] source-zone untrust
[Device-security-policy-ip-1-untrust-trust] destination-zone trust
[Device-security-policy-ip-1-untrust-trust] destination-ip-host 192.168.1.2
[Device-security-policy-ip-1-untrust-trust] action pass
[Device-security-policy-ip-1-untrust-trust] quit
[Device-security-policy-ip] quit
5. Configure NAT:
# Configure a NAT server mapping to allow external hosts to access the FTP server by using the address 202.38.1.1 and port 21..
[Device] interface gigabitethernet 1/0/2
[Device-GigabitEthernet1/0/2] nat server protocol tcp global 202.38.1.1 21 inside 192.168.1.2 ftp
6. Create address object group obj1, and add address 192.168.1.2 to the group.
[Device] object-group ip address obj1
[Device-obj-grp-ip-obj1] network host address 192.168.1.2
[Device-obj-grp-ip-obj1] quit
7. Configure a traffic profile:
# Create a traffic profile named ftp, and enter traffic profile view.
[Device] traffic-policy
[Device-traffic-policy] profile name ftp
# Set the total maximum bandwidth to 30720 kbps.
[Device-traffic-policy-profile-ftp] bandwidth downstream guaranteed 30720
[Device-traffic-policy-profile-ftp] quit
8. Configure a traffic rule:
# Create a traffic rule named ftp, and enter traffic rule view.
[Device-traffic-policy] rule name ftp
# Configure address object group obj1 as a match criterion, and specify traffic profile ftp for traffic rule ftp.
[Device-traffic-policy-rule-1-ftp] destination-address address-set obj1
[Device-traffic-policy-rule-1-ftp] application app ftp
[Device-traffic-policy-rule-1-ftp] application app ftp-data
[Device-traffic-policy-rule-1-ftp] action qos profile ftp
[Device-traffic-policy-rule-1-ftp] quit
[Device-traffic-policy] quit
# Enabling after-NAT destination matching.
[Device] traffic-policy
[Device-traffic-policy] destination-matching after-nat
[Device-traffic-policy] quit
# Verify that the bandwidth is limited to 30720 kbps for all external hosts to access the FTP server.
#
object-group ip address obj1
0 network host address 192.168.1.2
#
interface GigabitEthernet1/0/1
ip address 192.168.1.1 255.255.255.0
#
interface GigabitEthernet1/0/2
ip address 202.38.1.1 255.255.255.0
nat server protocol tcp global 202.38.1.1 21 inside 192.168.1.2 21
#
security-zone name Trust
import interface GigabitEthernet1/0/1
#
security-zone name Untrust
import interface GigabitEthernet1/0/2
#
ip route-static 3.1.1.0 24 202.38.1.3
#
traffic-policy
destination-matching after-nat
rule 1 name ftp
action qos profile ftp
destination-address address-set obj1
application app ftp
application app ftp-data
profile name ftp
bandwidth downstream guaranteed 30720
#
security-policy ip
rule 0 name untrust-trust
action pass
source-zone untrust
destination-zone trust
destination-ip-host 192.168.1.2
#