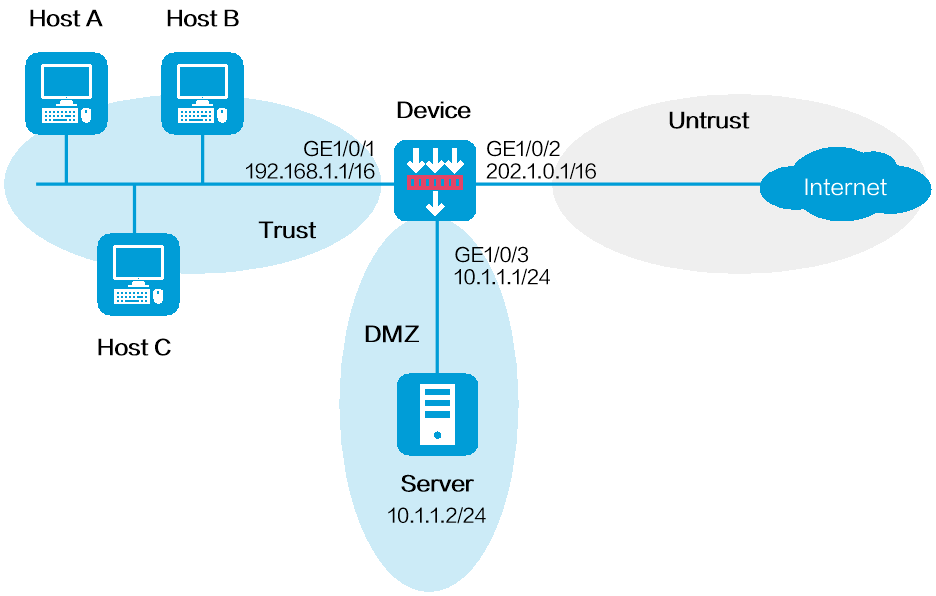
As shown in Figure 1, the device is the gateway for the internal network.
Configure an attack defense policy and apply the policy to security zone Untrust to meet the following requirements:
Provide low-level scanning attack detection for the internal network. If a scanning attack is detected, log the attack and keep the attacker on the blacklist for 10 minutes.
Protect internal hosts and servers against smurf attacks. If a smurf attack is detected, log the attack.
Protect the internal server against SYN flood attacks. If the number of SYN packets sent to the server per second reaches or exceeds 5000, log the attack and drop subsequent packets.
This configuration example was created and verified on E8371 of the F5000-AI160 device.
Assign IP addresses to interfaces:
Assign an IP address to interface GigabitEthernet 1/0/1.
<Device> system-view
[Device] interface gigabitethernet 1/0/1
[Device-GigabitEthernet1/0/1] ip address 192.168.1.1 255.255.0.0
[Device-GigabitEthernet1/0/1] quit
# Assign IP addresses to other interfaces in the same way. (Details not shown.)
Add interfaces to security zones.
[Device] security-zone name trust
[Device-security-zone-Trust] import interface gigabitethernet 1/0/1
[Device-security-zone-Trust] quit
[Device] security-zone name untrust
[Device-security-zone-Untrust] import interface gigabitethernet 1/0/2
[Device-security-zone-Untrust] quit
[Device] security-zone name dmz
[Device-security-zone-DMZ] import interface gigabitethernet 1/0/3
[Device-security-zone-DMZ] quit
Configure a security policy:
# Configure a rule named trust-untrust to allow hosts in security zone trust to access the Internet.
[Device] security-policy ip
[Device-security-policy-ip] rule name trust-untrust
[Device-security-policy-ip-1-trust-untrust] source-zone trust
[Device-security-policy-ip-1-trust-untrust] destination-zone untrust
[Device-security-policy-ip-1-trust-untrust] source-ip-subnet 192.168.0.0 16
[Device-security-policy-ip-1-trust-untrust] action pass
[Device-security-policy-ip-1-trust-untrust] quit
# Configure a rule named untrust-dmz to allow hosts on the Internet to access the server.
[Device-security-policy-ip] rule name untrust-dmz
[Device-security-policy-ip-2-untrust-dmz] source-zone untrust
[Device-security-policy-ip-2-untrust-dmz] destination-zone dmz
[Device-security-policy-ip-2-untrust-dmz] destination-ip-host 10.1.1.2
[Device-security-policy-ip-2-untrust-dmz] action pass
[Device-security-policy-ip-2-untrust-dmz] quit
[Device-security-policy-ip] quit
Configure an attack defense policy:
# Create attack defense policy a1.
[Device] attack-defense policy a1
# Configure signature detection for smurf attacks, and specify logging as the prevention action.
[Device-attack-defense-policy-a1] signature detect smurf action logging
# Configure low-level scanning attack detection, specify logging and block-source as the prevention actions, and set the blacklist entry aging time to 10 minutes.
[Device-attack-defense-policy-a1] scan detect level low action logging block-source timeout 10
# Configure SYN flood attack detection for 10.1.1.2, set the attack prevention triggering threshold to 5000, and specify logging and drop as the prevention actions.
[Device-attack-defense-policy-a1] syn-flood detect ip 10.1.1.2 threshold 5000 action logging drop
[Device-attack-defense-policy-a1] quit
# Apply attack defense policy a1 to security zone Untrust.
[Device] security-zone name untrust
[Device-security-zone-Untrust] attack-defense apply policy a1
[Device-security-zone-Untrust] quit
# Enable the global blacklist feature.
[Device] blacklist global enable
# Verify that attack defense policy a1 is successfully configured.
[Device] display attack-defense policy a1
Attack-defense Policy Information
--------------------------------------------------------------------------
Policy name : a1
Applied list : Untrust
--------------------------------------------------------------------------
Exempt IPv4 ACL : Not configured
Exempt IPv6 ACL : Not configured
--------------------------------------------------------------------------
Actions: CV-Client verify BS-Block source L-Logging D-Drop N-None
Signature attack defense configuration:
Signature name Defense Level Actions
Fragment Disabled low L
Impossible Disabled medium L,D
Teardrop Disabled medium L,D
Tiny fragment Disabled low L
IP option abnormal Disabled medium L,D
Smurf Enabled medium L
Traceroute Disabled low L
Ping of death Disabled medium L,D
Large ICMP Disabled info L
Max length 4000 bytes
Large ICMPv6 Disabled info L
Max length 4000 bytes
TCP invalid flags Disabled medium L,D
TCP null flag Disabled medium L,D
TCP all flags Disabled medium L,D
TCP SYN-FIN flags Disabled medium L,D
TCP FIN only flag Disabled medium L,D
TCP Land Disabled medium L,D
Winnuke Disabled medium L,D
UDP Bomb Disabled medium L,D
UDP Snork Disabled medium L,D
UDP Fraggle Disabled medium L,D
IP option record route Disabled info L
IP option internet timestamp Disabled info L
IP option security Disabled info L
IP option loose source routing Disabled info L
IP option stream ID Disabled info L
IP option strict source routing Disabled info L
IP option route alert Disabled info L
ICMP echo request Disabled info L
ICMP echo reply Disabled info L
ICMP source quench Disabled info L
ICMP destination unreachable Disabled info L
ICMP redirect Disabled info L
ICMP time exceeded Disabled info L
ICMP parameter problem Disabled info L
ICMP timestamp request Disabled info L
ICMP timestamp reply Disabled info L
ICMP information request Disabled info L
ICMP information reply Disabled info L
ICMP address mask request Disabled info L
ICMP address mask reply Disabled info L
ICMPv6 echo request Disabled info L
ICMPv6 echo reply Disabled info L
ICMPv6 group membership query Disabled info L
ICMPv6 group membership report Disabled info L
ICMPv6 group membership reduction Disabled info L
ICMPv6 destination unreachable Disabled info L
ICMPv6 time exceeded Disabled info L
ICMPv6 parameter problem Disabled info L
ICMPv6 packet too big Disabled info L
IPv6 extension header abnormal Disabled Info L
IPv6 extension header exceeded Disabled Info L
Limit 7
Scan attack defense configuration:
Defense : Enabled
Level : low
Actions : L,BS(10)
Flood attack defense configuration:
Flood type Global thres(pps) Global actions Service ports Non-specific
DNS flood 1000 - 53 Disabled
HTTP flood 1000 - 80 Disabled
SIP flood 1000 - 5060 Disabled
SYN flood 5000 L,D - Enabled
ACK flood 1000 - - Disabled
SYN-ACK flood 1000 - - Disabled
RST flood 1000 - - Disabled
FIN flood 1000 - - Disabled
UDP flood 1000 - - Disabled
ICMP flood 1000 - - Disabled
ICMPv6 flood 1000 - - Disabled
Flood attack defense for protected IP addresses:
Address VPN instance Flood type Thres(pps) Actions Ports
10.1.1.2 -- SYN-FLOOD 5000 L,D -
# Verify that the attack detection and prevention takes effect on security zone Untrust.
[Device] display attack-defense statistics security-zone untrust
Attack policy name: a1
Scan attack defense statistics:
AttackType AttackTimes Dropped
Port scan 2 0
IP sweep 3 0
Flood attack defense statistics:
AttackType AttackTimes Dropped
SYN flood 1 5000
Signature attack defense statistics:
AttackType AttackTimes Dropped
Smurf 1 0
# Verify that the IPv4 blacklist collaborates with the scanning attack detection.
[Device] display blacklist ip
IP address VPN instance DS-Lite tunnel peer Type TTL(sec) Dropped
5.5.5.5 -- -- Dynamic 600 353452
#
interface GigabitEthernet1/0/1
port link-mode route
ip address 192.168.1.1 255.255.0.0
#
interface GigabitEthernet1/0/2
port link-mode route
ip address 202.1.0.1 255.255.0.0
#
interface GigabitEthernet1/0/3
port link-mode route
ip address 10.1.1.1 255.255.255.0
#
#
security-zone name Trust
import interface GigabitEthernet1/0/1
#
security-zone name DMZ
import interface GigabitEthernet1/0/3
#
security-zone name Untrust
import interface GigabitEthernet1/0/2
attack-defense apply policy a1
#
blacklist global enable
#
attack-defense policy a1
scan detect level low action logging block-source
syn-flood detect ip 10.1.1.2 threshold 5000 action logging drop
signature detect smurf action logging
#
security-policy ip
rule 1 name trust-untrust
action pass
source-zone trust
destination-zone untrust
source-ip-subnet 192.168.0.0 255.255.0.0
rule 2 name untrust-dmz
action pass
source-zone untrust
destination-zone dmz
destination-ip-host 10.1.1.2