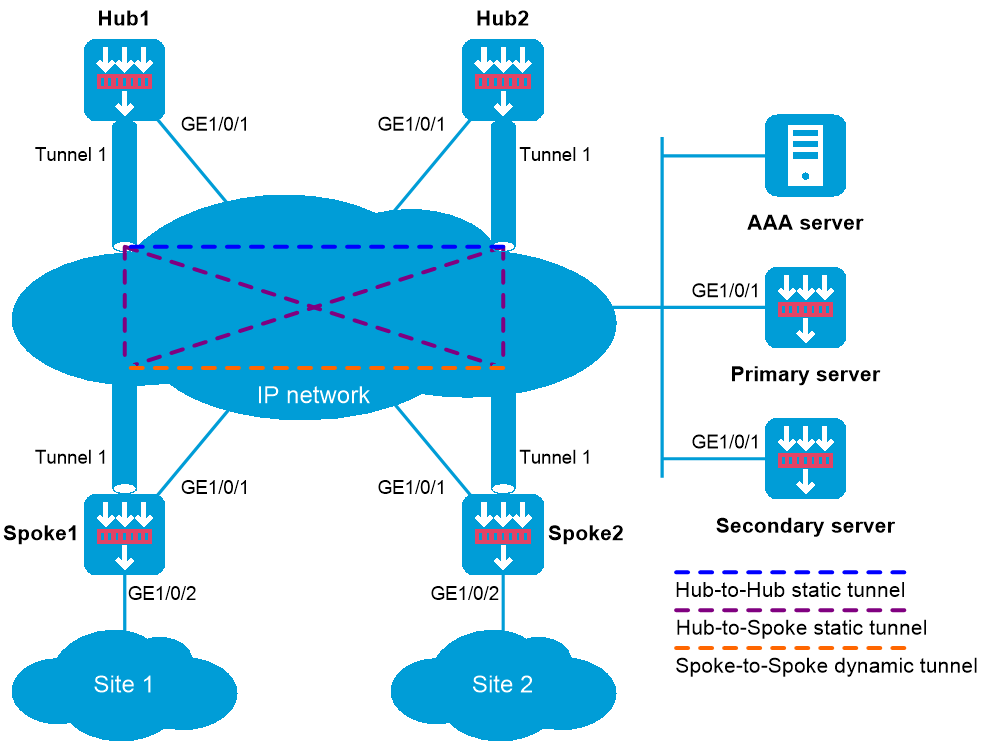
As shown in Figure 1, the primary and secondary VAM servers manage and maintain VAM client information for all hubs and spokes. The AAA server performs authentication and accounting for VAM clients. The two hubs back up each other, and perform data forwarding and route exchange.
Establish a permanent ADVPN tunnel between each spoke and each hub.
Table 4 Interface and IP address assignment
|
Device |
Interface |
IP address |
Device |
Interface |
IP address |
|
Hub 1 |
GE1/0/1 |
1::1/64 |
Spoke 1 |
GE1/0/1 |
1::3/64 |
|
|
Tunnel1 |
192:168::1/64 |
|
GE1/0/2 |
192:168:1::1/64 |
|
Hub 2 |
GE1/0/1 |
1::2/64 |
|
Tunnel1 |
192:168::3/64 |
|
|
Tunnel1 |
192:168::2/64 |
Spoke 2 |
GE1/0/1 |
1::4/64 |
|
AAA server |
|
1::10/64 |
|
GE1/0/2 |
192:168:2::1/64 |
|
Primary server |
GE1/0/1 |
1::11/64 |
|
Tunnel1 |
192:168::4/64 |
|
Secondary server |
GE1/0/1 |
1::12/64 |
|
|
|
This configuration example was created and verified on E8371 of the F5000-AI160 device.
1. Assign an IPv6 global unicast address to interface GigabitEthernet 1/0/1 as planned.
<PrimaryServer> system-view
[PrimaryServer] interface gigabitethernet 1/0/1
[PrimaryServer-GigabitEthernet1/0/1] ipv6 address 1::11/64
[PrimaryServer-GigabitEthernet1/0/1] quit
2. Add the interface to a security zone.
[PrimaryServer] security-zone name untrust
[PrimaryServer-security-zone-Untrust] import interface gigabitethernet 1/0/1
[PrimaryServer-security-zone-Untrust] quit
3. Configure a security policy:
# Configure a rule named advpnlocalout to allow the VAM server to send VAM protocol packets to the VAM clients.
[PrimaryServer] security-policy ipv6
[PrimaryServer-security-policy-ipv6] rule name advpnlocalout
[PrimaryServer-security-policy-ipv6-1-advpnlocalout] source-zone local
[PrimaryServer-security-policy-ipv6-1-advpnlocalout] destination-zone untrust
[PrimaryServer-security-policy-ipv6-1-advpnlocalout] source-ip-host 1::11
[PrimaryServer-security-policy-ipv6-1-advpnlocalout] destination-ip-range 1::1 1::12
[PrimaryServer-security-policy-ipv6-1-advpnlocalout] action pass
[PrimaryServer-security-policy-ipv6-1-advpnlocalout] quit
# Configure a rule named advpnlocalin to allow the VAM server to receive VAM protocol packets from the VAM clients.
[PrimaryServer-security-policy-ipv6] rule name advpnlocalin
[PrimaryServer-security-policy-ipv6-2-advpnlocalin] source-zone untrust
[PrimaryServer-security-policy-ipv6-2-advpnlocalin] destination-zone local
[PrimaryServer-security-policy-ipv6-2-advpnlocalin] source-ip-range 1::1 1::12
[PrimaryServer-security-policy-ipv6-2-advpnlocalin] destination-ip-host 1::11
[PrimaryServer-security-policy-ipv6-2-advpnlocalin] action pass
[PrimaryServer-security-policy-ipv6-2-advpnlocalin] quit
[PrimaryServer-security-policy-ipv6] quit
4. Configure AAA:
# Configure RADIUS scheme abc.
<PrimaryServer> system-view
[PrimaryServer] radius scheme abc
[PrimaryServer-radius-abc] primary authentication ipv6 1::10 1812
[PrimaryServer-radius-abc] primary accounting ipv6 1::10 1813
[PrimaryServer-radius-abc] key authentication simple 123
[PrimaryServer-radius-abc] key accounting simple 123
[PrimaryServer-radius-abc] user-name-format without-domain
[PrimaryServer-radius-abc] quit
[PrimaryServer] radius session-control enable
# Configure AAA methods for ISP domain abc.
[PrimaryServer] domain abc
[PrimaryServer-isp-abc] authentication advpn radius-scheme abc
[PrimaryServer-isp-abc] accounting advpn radius-scheme abc
[PrimaryServer-isp-abc] quit
[PrimaryServer] domain default enable abc
5. Configure the VAM server:
# Create ADVPN domain abc.
[PrimaryServer] vam server advpn-domain abc id 1
# Create hub group 0.
[PrimaryServer-vam-server-domain-abc] hub-group 0
# Specify hub private IPv6 addresses.
[PrimaryServer-vam-server-domain-abc-hub-group-0] hub ipv6 private-address 192:168::1
[PrimaryServer-vam-server-domain-abc-hub-group-0] hub ipv6 private-address 192:168::2
# Specify a spoke private IPv6 network.
[PrimaryServer-vam-server-domain-abc-hub-group-0] spoke ipv6 private-address network 192:168::0 64
[PrimaryServer-vam-server-domain-abc-hub-group-0] quit
# Set the preshared key to 123456.
[PrimaryServer-vam-server-domain-abc] pre-shared-key simple 123456
# Set the authentication mode to CHAP.
[PrimaryServer-vam-server-domain-abc] authentication-method chap
# Enable the VAM server for the ADVPN domain.
[PrimaryServer-vam-server-domain-abc] server enable
[PrimaryServer-vam-server-domain-abc] quit
# Configure the secondary VAM server in the same way that the primary server is configured. (Details not shown.)
1. Assign IP addresses to interfaces as planned:
# Assign an IPv6 global unicast address to interface GigabitEthernet 1/0/1.
<Hub1> system-view
[Hub1] interface gigabitethernet 1/0/1
[Hub1-GigabitEthernet1/0/1] ipv6 address 1::1 64
[Hub1-GigabitEthernet1/0/1] quit
# Create interface Tunnel 1 and set its tunnel mode to the GRE-encapsulated IPv6 ADVPN tunnel mode. Then, assign an IPv6 global unicast addresses and an IPv6 link-local address to the interface.
[Hub1] interface tunnel 1 mode advpn gre ipv6
[Hub1-Tunnel1] ipv6 address 192:168::1 64
[Hub1-Tunnel1] ipv6 address fe80::1 link-local
2. Add the interfaces to a security zone.
[Hub1] security-zone name untrust
[Hub1-security-zone-Untrust] import interface gigabitethernet 1/0/1
[Hub1-security-zone-Untrust] import interface tunnel1
[Hub1-security-zone-Untrust] quit
3. Configure a security policy:
# Configure a rule named advpnlocalout to allow Hub 1 to send VAM protocol packets to the VAM server.
[Hub1] security-policy ipv6
[Hub1-security-policy-ipv6] rule name advpnlocalout
[Hub1-security-policy-ipv6-1-advpnlocalout] source-zone local
[Hub1-security-policy-ipv6-1-advpnlocalout] destination-zone untrust
[Hub1-security-policy-ipv6-1-advpnlocalout] source-ip-host 1::1
[Hub1-security-policy-ipv6-1-advpnlocalout] destination-ip-range 1::10 1::12
[Hub1-security-policy-ipv6-1-ipseclocalout] action pass
[Hub1-security-policy-ipv6-1-ipseclocalout] quit
# Configure a rule named advpnlocalin to allow Hub 1 to receive VAM protocol packets from the VAM server.
[Hub1-security-policy-ipv6] rule name advpnlocalin
[Hub1-security-policy-ipv6-2-advpnlocalin] source-zone untrust
[Hub1-security-policy-ipv6-2-advpnlocalin] destination-zone local
[Hub1-security-policy-ipv6-2-advpnlocalin] source-ip-range 1::10 1::12
[Hub1-security-policy-ipv6-2-advpnlocalin] destination-ip-host 1::1
[Hub1-security-policy-ipv6-2-advpnlocalin] action pass
[Hub1-security-policy-ipv6-2-advpnlocalin] quit
# Configure a rule named ipseclocalout to allow Hub 1 to send IPsec negotiation packets to other VAM clients.
[Hub1-security-policy-ipv6] rule name ipseclocalout
[Hub1-security-policy-ipv6-3-ipseclocalout] source-zone local
[Hub1-security-policy-ipv6-3-ipseclocalout] destination-zone untrust
[Hub1-security-policy-ipv6-3-ipseclocalout] source-ip-host 1::1
[Hub1-security-policy-ipv6-3-ipseclocalout] destination-ip-range 1::2 1::4
[Hub1-security-policy-ipv6-3-ipseclocalout] action pass
[Hub1-security-policy-ipv6-3-ipseclocalout] quit
# Configure a rule named ipseclocalin to allow Hub 1 to receive IPsec negotiation packets from other VAM clients.
[Hub1-security-policy-ipv6] rule name ipseclocalin
[Hub1-security-policy-ipv6-4-ipseclocalin] source-zone untrust
[Hub1-security-policy-ipv6-4-ipseclocalin] destination-zone local
[Hub1-security-policy-ipv6-4-ipseclocalin] source-ip-range 1::2 1::4
[Hub1-security-policy-ipv6-4-ipseclocalin] destination-ip-host 1::1
[Hub1-security-policy-ipv6-4-ipseclocalin] action pass
[Hub1-security-policy-ipv6-4-ipseclocalin] quit
# Configure a rule named ospfout to allow Hub 1 to send OSPF packets to other VAM clients.
[Hub1-security-policy-ipv6] rule name ospflocalout
[Hub1-security-policy-ipv6-5-ospflocalout] source-zone local
[Hub1-security-policy-ipv6-5-ospflocalout] destination-zone untrust
[Hub1-security-policy-ipv6-5-ospflocalout] service ospf
[Hub1-security-policy-ipv6-5-ospflocalout] action pass
[Hub1-security-policy-ipv6-5-ospflocalout] quit
# Configure a rule named ospfin to allow Hub 1 to receive OSPF packets from other VAM clients.
[Hub1-security-policy-ipv6] rule name ospflocalin
[Hub1-security-policy-ipv6-6-ospflocalin] source-zone untrust
[Hub1-security-policy-ipv6-6-ospflocalin] destination-zone local
[Hub1-security-policy-ipv6-6-ospflocalin] service ospf
[Hub1-security-policy-ipv6-6-ospflocalin] action pass
[Hub1-security-policy-ipv6-6-ospflocalin] quit
4. Configure the VAM client:
# Create VAM client Hub1.
<Hub1> system-view
[Hub1] vam client name Hub1
# Specify ADVPN domain abc for the VAM client.
[Hub1-vam-client-Hub1] advpn-domain abc
# Set the preshared key to 123456.
[Hub1-vam-client-Hub1] pre-shared-key simple 123456
# Set the username and password to hub1.
[Hub1-vam-client-Hub1] user hub1 password simple hub1
# Specify the primary and secondary VAM servers.
[Hub1-vam-client-Hub1] server primary ipv6-address 1::11
[Hub1-vam-client-Hub1] server secondary ipv6-address 1::12
# Enable the VAM client.
[Hub1-vam-client-Hub1] client enable
[Hub1-vam-client-Hub1] quit
5. Configure an IPsec profile:
# Configure IKE.
[Hub1] ike keychain abc
[Hub1-ike-keychain-abc] pre-shared-key address ipv6 :: 0 key simple 123456
[Hub1-ike-keychain-abc] quit
[Hub1] ike profile abc
[Hub1-ike-profile-abc] keychain abc
[Hub1-ike-profile-abc] quit
# Configure the IPsec profile.
[Hub1] ipsec transform-set abc
[Hub1-ipsec-transform-set-abc] encapsulation-mode transport
[Hub1-ipsec-transform-set-abc] esp encryption-algorithm des-cbc
[Hub1-ipsec-transform-set-abc] esp authentication-algorithm sha1
[Hub1-ipsec-transform-set-abc] quit
[Hub1] ipsec profile abc isakmp
[Hub1-ipsec-profile-isakmp-abc] transform-set abc
[Hub1-ipsec-profile-isakmp-abc] ike-profile abc
[Hub1-ipsec-profile-isakmp-abc] quit
6. Configure OSPFv3.
[Hub1] ospfv3 1
[Hub1-ospfv3-1] router-id 0.0.0.1
[Hub1-ospfv3-1] area 0
[Hub1-ospfv3-1-area-0.0.0.0] quit
[Hub1-ospfv3-1] quit
7. Configure interface Tunnel 1.
[Hub1] interface tunnel1
[Hub1-Tunnel1] vam ipv6 client Hub1
[Hub1-Tunnel1] ospfv3 1 area 0
[Hub1-Tunnel1] ospfv3 network-type p2mp
[Hub1-Tunnel1] source gigabitethernet 1/0/1
[Hub1-Tunnel1] tunnel protection ipsec profile abc
[Hub1-Tunnel1] quit
1. Assign IP addresses to interfaces as planned:
# Assign an IPv6 global unicast address to interface GigabitEthernet 1/0/1.
<Hub2> system-view
[Hub2] interface gigabitethernet 1/0/1
[Hub2-GigabitEthernet1/0/1] ipv6 address 1::2 64
[Hub2-GigabitEthernet1/0/1] quit
# Create interface Tunnel 1 and set its tunnel mode to the GRE-encapsulated IPv6 ADVPN tunnel mode. Then, assign an IPv6 global unicast addresses and an IPv6 link-local address to the interface.
[Hub2] interface tunnel 1 mode advpn gre ipv6
[Hub2-Tunnel1] ipv6 address 192:168::2 64
[Hub2-Tunnel1] ipv6 address fe80::2 link-local
2. Add the interfaces to a security zone.
[Hub2] security-zone name untrust
[Hub2-security-zone-Untrust] import interface gigabitethernet 1/0/1
[Hub2-security-zone-Untrust] import interface tunnel1
[Hub2-security-zone-Untrust] quit
3. Configure a security policy:
# Configure a rule named advpnlocalout to allow Hub 2 to send VAM protocol packets to the VAM server.
[Hub2] security-policy ipv6
[Hub2-security-policy-ipv6] rule name advpnlocalout
[Hub2-security-policy-ipv6-1-advpnlocalout] source-zone local
[Hub2-security-policy-ipv6-1-advpnlocalout] destination-zone untrust
[Hub2-security-policy-ipv6-1-advpnlocalout] source-ip-host 1::2
[Hub2-security-policy-ipv6-1-advpnlocalout] destination-ip-range 1::10 1::12
[Hub2-security-policy-ipv6-1-ipseclocalout] action pass
[Hub2-security-policy-ipv6-1-ipseclocalout] quit
# Configure a rule named advpnlocalin to allow Hub 2 to receive VAM protocol packets from the VAM server.
[Hub2-security-policy-ipv6] rule name advpnlocalin
[Hub2-security-policy-ipv6-2-advpnlocalin] source-zone untrust
[Hub2-security-policy-ipv6-2-advpnlocalin] destination-zone local
[Hub2-security-policy-ipv6-2-advpnlocalin] source-ip-range 1::10 1::12
[Hub2-security-policy-ipv6-2-advpnlocalin] destination-ip-host 1::2
[Hub2-security-policy-ipv6-2-advpnlocalin] action pass
[Hub2-security-policy-ipv6-2-advpnlocalin] quit
# Configure a rule named ipseclocalout to allow Hub 2 to send IPsec negotiation packets to other VAM clients.
[Hub2-security-policy-ipv6] rule name ipseclocalout
[Hub2-security-policy-ipv6-3-ipseclocalout] source-zone local
[Hub2-security-policy-ipv6-3-ipseclocalout] destination-zone untrust
[Hub2-security-policy-ipv6-3-ipseclocalout] source-ip-host 1::2
[Hub2-security-policy-ipv6-3-ipseclocalout] destination-ip-range 1::1 1::4
[Hub2-security-policy-ipv6-3-ipseclocalout] action pass
[Hub2-security-policy-ipv6-3-ipseclocalout] quit
# Configure a rule named ipseclocalin to allow Hub 2 to receive IPsec negotiation packets from other VAM clients.
[Hub2-security-policy-ipv6] rule name ipseclocalin
[Hub2-security-policy-ipv6-4-ipseclocalin] source-zone untrust
[Hub2-security-policy-ipv6-4-ipseclocalin] destination-zone local
[Hub2-security-policy-ipv6-4-ipseclocalin] source-ip-range 1::1 1::4
[Hub2-security-policy-ipv6-4-ipseclocalin] destination-ip-host 1::2
[Hub2-security-policy-ipv6-4-ipseclocalin] action pass
[Hub2-security-policy-ipv6-4-ipseclocalin] quit
# Configure a rule named ospfout to allow Hub 2 to send OSPF packets to other VAM clients.
[Hub2-security-policy-ipv6] rule name ospflocalout
[Hub2-security-policy-ipv6-5-ospflocalout] source-zone local
[Hub2-security-policy-ipv6-5-ospflocalout] destination-zone untrust
[Hub2-security-policy-ipv6-5-ospflocalout] service ospf
[Hub2-security-policy-ipv6-5-ospflocalout] action pass
[Hub2-security-policy-ipv6-5-ospflocalout] quit
# Configure a rule named ospfin to allow Hub 2 to receive OSPF packets from other VAM clients.
[Hub2-security-policy-ipv6] rule name ospflocalin
[Hub2-security-policy-ipv6-6-ospflocalin] source-zone untrust
[Hub2-security-policy-ipv6-6-ospflocalin] destination-zone local
[Hub2-security-policy-ipv6-6-ospflocalin] service ospf
[Hub2-security-policy-ipv6-6-ospflocalin] action pass
[Hub2-security-policy-ipv6-6-ospflocalin] quit
[Hub2-security-policy-ipv6] quit
4. Configure the VAM client:
# Create VAM client Hub2.
<Hub2> system-view
[Hub2] vam client name Hub2
# Specify ADVPN domain abc for the VAM client.
[Hub2-vam-client-Hub2] advpn-domain abc
# Set the preshared key to 123456.
[Hub2-vam-client-Hub2] pre-shared-key simple 123456
# Set both the username and password to hub2.
[Hub2-vam-client-Hub2] user hub2 password simple hub2
# Specify the primary and secondary VAM servers.
[Hub2-vam-client-Hub2] server primary ipv6-address 1::11
[Hub2-vam-client-Hub2] server secondary ipv6-address 1::12
# Enable the VAM client.
[Hub2-vam-client-Hub2] client enable
[Hub2-vam-client-Hub2] quit
5. Configure an IPsec profile:
# Configure IKE.
[Hub2] ike keychain abc
[Hub2-ike-keychain-abc] pre-shared-key address ipv6 :: 0 key simple 123456
[Hub2-ike-keychain-abc] quit
[Hub2] ike profile abc
[Hub2-ike-profile-abc] keychain abc
[Hub2-ike-profile-abc] quit
# Configure the IPsec profile.
[Hub2] ipsec transform-set abc
[Hub2-ipsec-transform-set-abc] encapsulation-mode transport
[Hub2-ipsec-transform-set-abc] esp encryption-algorithm des-cbc
[Hub2-ipsec-transform-set-abc] esp authentication-algorithm sha1
[Hub2-ipsec-transform-set-abc] quit
[Hub2] ipsec profile abc isakmp
[Hub2-ipsec-profile-isakmp-abc] transform-set abc
[Hub2-ipsec-profile-isakmp-abc] ike-profile abc
[Hub2-ipsec-profile-isakmp-abc] quit
6. Configure OSPFv3.
[Hub2] ospfv3 1
[Hub2-ospfv3-1] router-id 0.0.0.2
[Hub2-ospfv3-1] area 0
[Hub2-ospfv3-1-area-0.0.0.0] quit
[Hub2-ospfv3-1] quit
7. Configure interface Tunnel 1.
[Hub2] interface tunnel1
[Hub2-Tunnel1] vam ipv6 client Hub2
[Hub2-Tunnel1] ospfv3 1 area 0
[Hub2-Tunnel1] ospfv3 network-type p2mp
[Hub2-Tunnel1] source gigabitethernet 1/0/1
[Hub2-Tunnel1] tunnel protection ipsec profile abc
[Hub2-Tunnel1] quit
1. Assign IP addresses to interfaces as planned:
# Assign a global unicast address to interface GigabitEthernet 1/0/1.
<Spoke1> system-view
[Spoke1] interface gigabitethernet 1/0/1
[Spoke1-GigabitEthernet1/0/1] ipv6 address 1::3 64
[Spoke1-GigabitEthernet1/0/1] quit
# Create interface Tunnel 1 and set its tunnel mode to the GRE-encapsulated IPv6 ADVPN tunnel mode. Then, assign an IPv6 global unicast addresses and an IPv6 link-local address to the interface.
[Spoke1] interface tunnel 1 mode advpn gre ipv6
[Spoke1-Tunnel1] ipv6 address 192:168::3 64
[Spoke1-Tunnel1] ipv6 address fe80::3 link-local
# Assign IP addresses to other interfaces. (Details not shown.)
2. Add the interfaces to security zones.
[Spoke1] security-zone name untrust
[Spoke1-security-zone-Untrust] import interface gigabitethernet 1/0/1
[Spoke1-security-zone-Untrust] import interface tunnel1
[Spoke1-security-zone-Untrust] quit
[Spoke1] security-zone name trust
[Spoke1-security-zone-Trust] import interface gigabitethernet 1/0/2
[Spoke1-security-zone-Trust] quit
3. Configure a security policy:
# Configure a rule named advpnlocalout to allow Spoke 1 to send VAM protocol packets to the VAM server.
[Spoke1] security-policy ipv6
[Spoke1-security-policy-ipv6] rule name advpnlocalout
[Spoke1-security-policy-ipv6-1-advpnlocalout] source-zone local
[Spoke1-security-policy-ipv6-1-advpnlocalout] destination-zone untrust
[Spoke1-security-policy-ipv6-1-advpnlocalout] source-ip-host 1::3
[Spoke1-security-policy-ipv6-1-advpnlocalout] destination-ip-range 1::10 1::12
[Spoke1-security-policy-ipv6-1-ipseclocalout] action pass
[Spoke1-security-policy-ipv6-1-ipseclocalout] quit
# Configure a rule named advpnlocalin to allow Spoke 1 to receive VAM protocol packets from the VAM server.
[Spoke1-security-policy-ipv6] rule name advpnlocalin
[Spoke1-security-policy-ipv6-2-advpnlocalin] source-zone untrust
[Spoke1-security-policy-ipv6-2-advpnlocalin] destination-zone local
[Spoke1-security-policy-ipv6-2-advpnlocalin] source-ip-range 1::10 1::12
[Spoke1-security-policy-ipv6-2-advpnlocalin] destination-ip-host 1::3
[Spoke1-security-policy-ipv6-2-advpnlocalin] action pass
[Spoke1-security-policy-ipv6-2-advpnlocalin] quit
# Configure a rule named ipseclocalout to allow Spoke 1 to send IPsec negotiation packets to other VAM clients.
[Spoke1-security-policy-ipv6] rule name ipseclocalout
[Spoke1-security-policy-ipv6-3-ipseclocalout] source-zone local
[Spoke1-security-policy-ipv6-3-ipseclocalout] destination-zone untrust
[Spoke1-security-policy-ipv6-3-ipseclocalout] source-ip-host 1::3
[Spoke1-security-policy-ipv6-3-ipseclocalout] destination-ip-range 1::1 1::4
[Spoke1-security-policy-ipv6-3-ipseclocalout] action pass
[Spoke1-security-policy-ipv6-3-ipseclocalout] quit
# Configure a rule named ipseclocalin to allow Spoke 1 to receive IPsec negotiation packets from other VAM clients.
[Spoke1-security-policy-ipv6] rule name ipseclocalin
[Spoke1-security-policy-ipv6-4-ipseclocalin] source-zone untrust
[Spoke1-security-policy-ipv6-4-ipseclocalin] destination-zone local
[Spoke1-security-policy-ipv6-4-ipseclocalin] source-ip-range 1::1 1::4
[Spoke1-security-policy-ipv6-4-ipseclocalin] destination-ip-host 1::3
[Spoke1-security-policy-ipv6-4-ipseclocalin] action pass
[Spoke1-security-policy-ipv6-4-ipseclocalin] quit
# Configure a rule named ospfout to allow Spoke 1 to send OSPF packets to other VAM clients.
[Spoke1-security-policy-ipv6] rule name ospflocalout
[Spoke1-security-policy-ipv6-5-ospflocalout] source-zone local
[Spoke1-security-policy-ipv6-5-ospflocalout] destination-zone untrust
[Spoke1-security-policy-ipv6-5-ospflocalout] service ospf
[Spoke1-security-policy-ipv6-5-ospflocalout] action pass
[Spoke1-security-policy-ipv6-5-ospflocalout] quit
# Configure a rule named ospfin to allow Spoke 1 to receive OSPF packets from other VAM clients.
[Spoke1-security-policy-ipv6] rule name ospflocalin
[Spoke1-security-policy-ipv6-6-ospflocalin] source-zone untrust
[Spoke1-security-policy-ipv6-6-ospflocalin] destination-zone local
[Spoke1-security-policy-ipv6-6-ospflocalin] service ospf
[Spoke1-security-policy-ipv6-6-ospflocalin] action pass
[Spoke1-security-policy-ipv6-6-ospflocalin] quit
[Spoke1-security-policy-ipv6] quit
4. Configure the VAM client:
# Create VAM client Spoke1.
<Spoke1> system-view
[Spoke1] vam client name Spoke1
# Specify ADVPN domain abc for the VAM client.
[Spoke1-vam-client-Spoke1] advpn-domain abc
# Set the preshared key to 123456.
[Spoke1-vam-client-Spoke1] pre-shared-key simple 123456
# Set both the username and password to spoke1.
[Spoke1-vam-client-Spoke1] user spoke1 password simple spoke1
# Specify the primary and secondary VAM servers.
[Spoke1-vam-client-Spoke1] server primary ipv6-address 1::11
[Spoke1-vam-client-Spoke1] server secondary ipv6-address 1::12
# Enable the VAM client.
[Spoke1-vam-client-Spoke1] client enable
[Spoke1-vam-client-Spoke1] quit
5. Configure an IPsec profile:
# Configure IKE.
[Spoke1] ike keychain abc
[Spoke1-ike-keychain-abc] pre-shared-key address ipv6 :: 0 key simple 123456
[Spoke1-ike-keychain-abc] quit
[Spoke1] ike profile abc
[Spoke1-ike-profile-abc] keychain abc
[Spoke1-ike-profile-abc] quit
# Configure the IPsec profile.
[Spoke1] ipsec transform-set abc
[Spoke1-ipsec-transform-set-abc] encapsulation-mode transport
[Spoke1-ipsec-transform-set-abc] esp encryption-algorithm des-cbc
[Spoke1-ipsec-transform-set-abc] esp authentication-algorithm sha1
[Spoke1-ipsec-transform-set-abc] quit
[Spoke1] ipsec profile abc isakmp
[Spoke1-ipsec-profile-isakmp-abc] transform-set abc
[Spoke1-ipsec-profile-isakmp-abc] ike-profile abc
[Spoke1-ipsec-profile-isakmp-abc] quit
6. Configure OSPFv3.
[Spoke1] ospfv3 1
[Spoke1-ospfv3-1] router-id 0.0.0.3
[Spoke1-ospfv3-1] area 0
[Spoke1-ospfv3-1-area-0.0.0.0] quit
[Spoke1-ospfv3-1] quit
7. Configure interface Tunnel 1.
[Spoke1] interface tunnel1
[Spoke1-Tunnel1] vam ipv6 client Spoke1
[Spoke1-Tunnel1] ospfv3 1 area 0
[Spoke1-Tunnel1] ospfv3 network-type p2mp
[Spoke1-Tunnel1] source gigabitethernet 1/0/1
[Spoke1-Tunnel1] tunnel protection ipsec profile abc
[Spoke1-Tunnel1] quit
1. Assign IP addresses to interfaces as planned:
# Assign a global unicast address to interface GigabitEthernet 1/0/1.
<Spoke2> system-view
[Spoke2] interface gigabitethernet 1/0/1
[Spoke2-GigabitEthernet1/0/1] ipv6 address 1::4 64
[Spoke2-GigabitEthernet1/0/1] quit
# Create interface Tunnel 1 and set its tunnel mode to the GRE-encapsulated IPv6 ADVPN tunnel mode. Then, assign an IPv6 global unicast addresses and an IPv6 link-local address to the interface.
[Spoke2] interface tunnel 1 mode advpn gre ipv6
[Spoke2-Tunnel1] ipv6 address 192:168::4 64
[Spoke2-Tunnel1] ipv6 address fe80::4 link-local
# Assign IP addresses to other interfaces. (Details not shown.)
2. Add the interfaces to security zones.
[Spoke2] security-zone name untrust
[Spoke2-security-zone-Untrust] import interface gigabitethernet 1/0/1
[Spoke2-security-zone-Untrust] import interface tunnel1
[Spoke2-security-zone-Untrust] quit
[Spoke2] security-zone name trust
[Spoke2-security-zone-Trust] import interface gigabitethernet 1/0/2
[Spoke2-security-zone-Trust] quit
3. Configure a security policy:
# Configure a rule named advpnlocalout to allow Spoke 2 to send VAM protocol packets to the VAM server.
[Spoke2] security-policy ipv6
[Spoke2-security-policy-ipv6] rule name advpnlocalout
[Spoke2-security-policy-ipv6-1-advpnlocalout] source-zone local
[Spoke2-security-policy-ipv6-1-advpnlocalout] destination-zone untrust
[Spoke2-security-policy-ipv6-1-advpnlocalout] source-ip-host 1::4
[Spoke2-security-policy-ipv6-1-advpnlocalout] destination-ip-range 1::10 1::12
[Spoke2-security-policy-ipv6-1-ipseclocalout] action pass
[Spoke2-security-policy-ipv6-1-ipseclocalout] quit
# Configure a rule named advpnlocalin to allow Spoke 2 to receive VAM protocol packets from the VAM server.
[Spoke2-security-policy-ipv6] rule name advpnlocalin
[Spoke2-security-policy-ipv6-2-advpnlocalin] source-zone untrust
[Spoke2-security-policy-ipv6-2-advpnlocalin] destination-zone local
[Spoke2-security-policy-ipv6-2-advpnlocalin] source-ip-range 1::10 1::12
[Spoke2-security-policy-ipv6-2-advpnlocalin] destination-ip-host 1::4
[Spoke2-security-policy-ipv6-2-advpnlocalin] action pass
[Spoke2-security-policy-ipv6-2-advpnlocalin] quit
# Configure a rule named ipseclocalout to allow Spoke 2 to send IPsec negotiation packets to other VAM clients.
[Spoke2-security-policy-ipv6] rule name ipseclocalout
[Spoke2-security-policy-ipv6-3-ipseclocalout] source-zone local
[Spoke2-security-policy-ipv6-3-ipseclocalout] destination-zone untrust
[Spoke2-security-policy-ipv6-3-ipseclocalout] source-ip-host 1::4
[Spoke2-security-policy-ipv6-3-ipseclocalout] destination-ip-range 1::1 1::3
[Spoke2-security-policy-ipv6-3-ipseclocalout] action pass
[Spoke2-security-policy-ipv6-3-ipseclocalout] quit
# Configure a rule named ipseclocalin to allow Spoke 2 to receive IPsec negotiation packets from other VAM clients.
[Spoke2-security-policy-ipv6] rule name ipseclocalin
[Spoke2-security-policy-ipv6-4-ipseclocalin] source-zone untrust
[Spoke2-security-policy-ipv6-4-ipseclocalin] destination-zone local
[Spoke2-security-policy-ipv6-4-ipseclocalin] source-ip-range 1::1 1::3
[Spoke2-security-policy-ipv6-4-ipseclocalin] destination-ip-host 1::4
[Spoke2-security-policy-ipv6-4-ipseclocalin] action pass
[Spoke2-security-policy-ipv6-4-ipseclocalin] quit
# Configure a rule named ospfout to allow Spoke 2 to send OSPF packets to other VAM clients.
[Spoke2-security-policy-ipv6] rule name ospflocalout
[Spoke2-security-policy-ipv6-5-ospflocalout] source-zone local
[Spoke2-security-policy-ipv6-5-ospflocalout] destination-zone untrust
[Spoke2-security-policy-ipv6-5-ospflocalout] service ospf
[Spoke2-security-policy-ipv6-5-ospflocalout] action pass
[Spoke2-security-policy-ipv6-5-ospflocalout] quit
# Configure a rule named ospfin to allow Spoke 2 to receive OSPF packets from other VAM clients.
[Spoke2-security-policy-ipv6] rule name ospflocalin
[Spoke2-security-policy-ipv6-6-ospflocalin] source-zone untrust
[Spoke2-security-policy-ipv6-6-ospflocalin] destination-zone local
[Spoke2-security-policy-ipv6-6-ospflocalin] service ospf
[Spoke2-security-policy-ipv6-6-ospflocalin] action pass
[Spoke2-security-policy-ipv6-6-ospflocalin] quit
[Spoke2-security-policy-ipv6] quit
4. Configure the VAM client:
# Create VAM client Spoke2.
<Spoke2> system-view
[Spoke2] vam client name Spoke2
# Specify ADVPN domain abc for the VAM client.
[Spoke2-vam-client-Spoke2] advpn-domain abc
# Set the preshared key to 123456.
[Spoke2-vam-client-Spoke2] pre-shared-key simple 123456
# Set both the username and password to spoke2.
[Spoke2-vam-client-Spoke2] user spoke2 password simple spoke2
# Specify the primary and secondary VAM servers.
[Spoke2-vam-client-Spoke2] server primary ipv6-address 1::11
[Spoke2-vam-client-Spoke2] server secondary ipv6-address 1::12
# Enable the VAM client.
[Spoke2-vam-client-Spoke2] client enable
[Spoke2-vam-client-Spoke2] quit
5. Configure an IPsec profile:
# Configure IKE.
[Spoke2] ike keychain abc
[Spoke2-ike-keychain-abc] pre-shared-key address ipv6 :: 0 key simple 123456
[Spoke2-ike-keychain-abc] quit
[Spoke2] ike profile abc
[Spoke2-ike-profile-abc] keychain abc
[Spoke2-ike-profile-abc] quit
# Configure the IPsec profile.
[Spoke2] ipsec transform-set abc
[Spoke2-ipsec-transform-set-abc] encapsulation-mode transport
[Spoke2-ipsec-transform-set-abc] esp encryption-algorithm des-cbc
[Spoke2-ipsec-transform-set-abc] esp authentication-algorithm sha1
[Spoke2-ipsec-transform-set-abc] quit
[Spoke2] ipsec profile abc isakmp
[Spoke2-ipsec-profile-isakmp-abc] transform-set abc
[Spoke2-ipsec-profile-isakmp-abc] ike-profile abc
[Spoke2-ipsec-profile-isakmp-abc] quit
6. Configure OSPFv3.
[Spoke2] ospfv3 1
[Spoke2-ospfv3-1] router-id 0.0.0.4
[Spoke2-ospfv3-1] area 0
[Spoke2-ospfv3-1-area-0.0.0.0] quit
[Spoke2-ospfv3-1] quit
7. Configure interface Tunnel 1.
[Spoke2] interface tunnel1
[Spoke2-Tunnel1] vam ipv6 client Spoke2
[Spoke2-Tunnel1] ospfv3 1 area 0
[Spoke2-Tunnel1] ospfv3 network-type p2mp
[Spoke2-Tunnel1] source gigabitethernet 1/0/1
[Spoke2-Tunnel1] tunnel protection ipsec profile abc
[Spoke2-Tunnel1] quit
# Display IPv6 address mapping information for all VAM clients registered with the primary VAM server.
[PrimaryServer] display vam server ipv6 address-map
ADVPN domain name: abc
Total private address mappings: 4
Group Private address Public address Type NAT Holding time
0 192:168::1 1::1 Hub No 0H 52M 7S
0 192:168::2 1::2 Hub No 0H 47M 31S
0 192:168::3 1::3 Spoke No 0H 28M 25S
0 192:168::4 1::4 Spoke No 0H 19M 15S
# Display IPv6 address mapping information for all VAM clients registered with the secondary VAM server.
[SecondaryServer] display vam server ipv6 address-map
ADVPN domain name: abc
Total private address mappings: 4
Group Private address Public address Type NAT Holding time
0 192:168::1 1::1 Hub No 0H 52M 7S
0 192:168::2 1::2 Hub No 0H 47M 31S
0 192:168::3 1::3 Spoke No 0H 28M 25S
0 192:168::4 1::4 Spoke No 0H 19M 15S
The output shows that Hub 1, Hub 2, Spoke 1, and Spoke 2 have all registered their address mapping information with the VAM servers.
# Display IPv6 ADVPN tunnel information on Hubs. This example uses Hub 1.
[Hub1] display advpn ipv6 session
Interface : Tunnel1
Number of sessions: 3
Private address Public address Port Type State Holding time
192:168::2 1::2 -- H-H Success 0H 46M 8S
192:168::3 1::3 -- H-S Success 0H 27M 27S
192:168::4 1::4 -- H-S Success 0H 18M 18S
The output shows that Hub 1 has established a permanent tunnel to Hub 2, Spoke 1, and Spoke 2.
# Display IPv6 ADVPN tunnel information on Spokes. This example uses Spoke 1.
[Spoke1] display advpn ipv6 session
Interface : Tunnel1
Number of sessions: 2
Private address Public address Port Type State Holding time
192:168::1 1::1 -- S-H Success 0H 46M 8S
192:168::2 1::2 -- S-H Success 0H 46M 8S
The output shows that Spoke 1 has established a permanent hub-spoke tunnel to Hub 1 and Hub 2.
# Verify that Spoke 1 can ping the private address 192:168::4 of Spoke 2.
[Spoke1] ping ipv6 192:168::4
Ping6(56 data bytes) 192:168::4 --> 192:168::4, press CTRL_C to break
56 bytes from 192:168::4, icmp_seq=0 hlim=64 time=3.000 ms
56 bytes from 192:168::4, icmp_seq=1 hlim=64 time=0.000 ms
56 bytes from 192:168::4, icmp_seq=2 hlim=64 time=1.000 ms
56 bytes from 192:168::4, icmp_seq=3 hlim=64 time=1.000 ms
56 bytes from 192:168::4, icmp_seq=4 hlim=64 time=1.000 ms
--- Ping6 statistics for 192:168::4 ---
5 packets transmitted, 5 packets received, 0.0% packet loss
round-trip min/avg/max/std-dev = 0.000/1.200/3.000/0.980 ms
#
interface GigabitEthernet1/0/1
ipv6 address 1::11/64
#
security-zone name Untrust
import interface GigabitEthernet1/0/1
#
radius session-control enable
#
radius scheme abc
primary authentication ipv6 1::10
primary accounting ipv6 1::10
key authentication simple 123
key accounting simple 123
user-name-format without-domain
#
domain abc
authentication advpn radius-scheme abc
accounting advpn radius-scheme abc
#
domain default enable abc
#
vam server advpn-domain abc id 1
pre-shared-key simple 123456
authentication-method chap
server enable
hub-group 0
hub ipv6 private-address 192:168::1
hub ipv6 private-address 192:168::2
spoke ipv6 private-address range 192:168:: 192:168::FFFF:FFFF:FFFF:FFFF
#
security-policy ipv6
rule 0 name advpnlocalout
action pass
source-zone local
destination-zone untrust
source-ip-host 1::11
destination-ip-range 1::1 1::12
rule 1 name advpnlocalin
action pass
source-zone untrust
destination-zone local
source-ip-range 1::1 1::12
destination-ip-host 1::11
#
#
interface GigabitEthernet1/0/1
ipv6 address 1::12/64
#
security-zone name Untrust
import interface GigabitEthernet1/0/1
#
radius session-control enable
#
radius scheme abc
primary authentication ipv6 1::10
primary accounting ipv6 1::10
key authentication simple 123
key accounting simple 123
user-name-format without-domain
#
domain abc
authentication advpn radius-scheme abc
accounting advpn radius-scheme abc
#
domain default enable abc
#
vam server advpn-domain abc id 1
pre-shared-key simple 123456
authentication-method chap
server enable
hub-group 0
hub ipv6 private-address 192:168::1
hub ipv6 private-address 192:168::2
spoke ipv6 private-address range 192:168:: 192:168::FFFF:FFFF:FFFF:FFFF
#
security-policy ipv6
rule 0 name advpnlocalout
action pass
source-zone local
destination-zone untrust
source-ip-host 1::11
destination-ip-range 1::1 1::12
rule 1 name advpnlocalin
action pass
source-zone untrust
destination-zone local
source-ip-range 1::1 1::12
destination-ip-host 1::11
#
#
ospfv3 1
router-id 0.0.0.1
area 0.0.0.0
#
interface GigabitEthernet1/0/1
ipv6 address 1::1/64
#
interface Tunnel1 mode advpn gre ipv6
ospfv3 1 area 0.0.0.0
ospfv3 network-type p2mp
source GigabitEthernet1/0/1
ipv6 address FE80::1 link-local
ipv6 address 192:168::1/64
tunnel protection ipsec profile abc
vam ipv6 client Hub1
#
security-zone name Untrust
import interface GigabitEthernet1/0/1
import interface Tunnel1
#
ipsec transform-set abc
encapsulation-mode transport
esp encryption-algorithm des-cbc
esp authentication-algorithm sha1
#
ipsec profile abc isakmp
transform-set abc
ike-profile abc
#
ike profile abc
keychain abc
#
ike keychain abc
pre-shared-key address ipv6 :: 0 key simple 123456
#
vam client name Hub1
advpn-domain abc
server primary ipv6-address 1::11
server secondary ipv6-address 1::12
pre-shared-key simple 123456
user hub1 password simple hub1
client enable
#
security-policy ip
#
security-policy ipv6
rule 0 name advpnlocalout
action pass
source-zone local
destination-zone untrust
source-ip-host 1::1
destination-ip-range 1::10 1::12
rule 1 name advpnlocalin
action pass
source-zone untrust
destination-zone local
source-ip-range 1::10 1::12
destination-ip-host 1::1
rule 2 name ipseclocalout
action pass
source-zone local
destination-zone untrust
source-ip-host 1::1
destination-ip-range 1::2 1::4
rule 3 name ipseclocalin
action pass
source-zone untrust
destination-zone local
source-ip-range 1::2 1::4
destination-ip-host 1::1
rule 4 name ospflocalout
action pass
source-zone local
destination-zone untrust
service ospf
rule 5 name ospflocalin
action pass
source-zone untrust
destination-zone local
service ospf
#
#
ospfv3 1
router-id 0.0.0.2
area 0.0.0.0
#
interface GigabitEthernet1/0/1
ipv6 address 1::2/64
#
interface Tunnel1 mode advpn gre ipv6
ospfv3 1 area 0.0.0.0
ospfv3 network-type p2mp
source GigabitEthernet1/0/1
ipv6 address FE80::2 link-local
ipv6 address 192:168::2/64
tunnel protection ipsec profile abc
vam ipv6 client Hub2
#
security-zone name Untrust
import interface GigabitEthernet1/0/1
import interface Tunnel1
#
ipsec transform-set abc
encapsulation-mode transport
esp encryption-algorithm des-cbc
esp authentication-algorithm sha1
#
ipsec profile abc isakmp
transform-set abc
ike-profile abc
#
ike profile abc
keychain abc
#
ike keychain abc
pre-shared-key address ipv6 :: 0 key simple 123456
#
vam client name Hub2
advpn-domain abc
server primary ipv6-address 1::11
server secondary ipv6-address 1::12
pre-shared-key simple 123456
user hub2 password simple hub2
client enable
#
security-policy ip
#
security-policy ipv6
rule 0 name advpnlocalout
action pass
source-zone local
destination-zone untrust
source-ip-host 1::2
destination-ip-range 1::10 1::12
rule 1 name advpnlocalin
action pass
source-zone untrust
destination-zone local
source-ip-range 1::10 1::12
destination-ip-host 1::2
rule 2 name ipseclocalout
action pass
source-zone local
destination-zone untrust
source-ip-host 1::2
destination-ip-range 1::1 1::4
rule 3 name ipseclocalin
action pass
source-zone untrust
destination-zone local
source-ip-range 1::1 1::4
destination-ip-host 1::2
rule 4 name ospflocalout
action pass
source-zone local
destination-zone untrust
service ospf
rule 5 name ospflocalin
action pass
source-zone untrust
destination-zone local
service ospf
#
#
ospfv3 1
router-id 0.0.0.3
area 0.0.0.0
#
interface GigabitEthernet1/0/1
ipv6 address 1::3/64
#
interface GigabitEthernet1/0/2
ipv6 address 192:168:1::1/64
#
interface Tunnel1 mode advpn gre ipv6
ospfv3 1 area 0.0.0.0
ospfv3 network-type p2mp
source GigabitEthernet1/0/1
ipv6 address FE80::3 link-local
ipv6 address 192:168::3/64
tunnel protection ipsec profile abc
vam ipv6 client Spoke1
#
security-zone name Trust
import interface GigabitEthernet1/0/2
#
security-zone name Untrust
import interface GigabitEthernet1/0/1
import interface Tunnel1
#
ipsec transform-set abc
encapsulation-mode transport
esp encryption-algorithm des-cbc
esp authentication-algorithm sha1
#
ipsec profile abc isakmp
transform-set abc
ike-profile abc
#
ike profile abc
keychain abc
#
ike keychain abc
pre-shared-key address 0.0.0.0 0.0.0.0 key simple 123456
#
vam client name Spoke1
advpn-domain abc
server primary ipv6-address 1::11
server secondary ipv6-address 1::12
pre-shared-key simple 123456
user spoke1 password simple spoke1
client enable
#
security-policy ip
#
security-policy ipv6
rule 0 name advpnlocalout
action pass
source-zone local
destination-zone untrust
source-ip-host 1::3
destination-ip-range 1::10 1::12
rule 1 name advpnlocalin
action pass
source-zone untrust
destination-zone local
source-ip-range 1::10 1::12
destination-ip-host 1::3
rule 2 name ipseclocalout
action pass
source-zone local
destination-zone untrust
source-ip-host 1::3
destination-ip-range 1::1 1::4
rule 3 name ipseclocalin
action pass
source-zone untrust
destination-zone local
source-ip-range 1::1 1::4
destination-ip-host 1::3
rule 4 name ospflocalout
action pass
source-zone local
destination-zone untrust
service ospf
rule 5 name ospflocalin
action pass
source-zone untrust
destination-zone local
service ospf
#
#
ospfv3 1
router-id 0.0.0.4
area 0.0.0.0
#
interface GigabitEthernet1/0/1
ipv6 address 1::4/64
#
interface GigabitEthernet1/0/2
ipv6 address 192:168:2::1/64
#
interface Tunnel1 mode advpn gre ipv6
ospfv3 1 area 0.0.0.0
ospfv3 network-type p2mp
source GigabitEthernet1/0/1
ipv6 address FE80::4 link-local
ipv6 address 192:168::4/64
tunnel protection ipsec profile abc
vam ipv6 client Spoke2
#
security-zone name Trust
import interface GigabitEthernet1/0/2
#
security-zone name Untrust
import interface GigabitEthernet1/0/1
import interface Tunnel1
#
ipsec transform-set abc
encapsulation-mode transport
esp encryption-algorithm des-cbc
esp authentication-algorithm sha1
#
ipsec profile abc isakmp
transform-set abc
ike-profile abc
#
ike profile abc
keychain abc
#
ike keychain abc
pre-shared-key address 0.0.0.0 0.0.0.0 key simple 123456
#
vam client name Spoke2
advpn-domain abc
server primary ipv6-address 1::11
server secondary ipv6-address 1::12
pre-shared-key simple 123456
user spoke2 password simple spoke2
client enable
#
security-policy ip
#
security-policy ipv6
rule 0 name advpnlocalout
action pass
source-zone local
destination-zone untrust
source-ip-host 1::4
destination-ip-range 1::10 1::12
rule 1 name advpnlocalin
action pass
source-zone untrust
destination-zone local
source-ip-range 1::10 1::12
destination-ip-host 1::4
rule 2 name ipseclocalout
action pass
source-zone local
destination-zone untrust
source-ip-host 1::4
destination-ip-range 1::1 1::3
rule 3 name ipseclocalin
action pass
source-zone untrust
destination-zone local
source-ip-range 1::1 1::3
destination-ip-host 1::4
rule 4 name ospflocalout
action pass
source-zone local
destination-zone untrust
service ospf
rule 5 name ospflocalin
action pass
source-zone untrust
destination-zone local
service ospf