About classic networks
Classic network is a type of private cloud network created to provide a secure and isolated virtualization environment for auto-configuration and management of cloud hosts and bare metal nodes in a private cloud. Classic network supports IPv4 and IPv6 versions.
You can perform the following tasks in a classic network:
Create subnets and routers, and attach routers to subnets to enable subnets bound with the same router to reach each other.
Attach elastic networks to subnets to enable Internet access, and connect firewalls to subnets to provide advanced security protection for communication with the external network.
Create security groups for cloud hosts and define intra-security group and inter-security group access rules to enhance cloud host security protection.
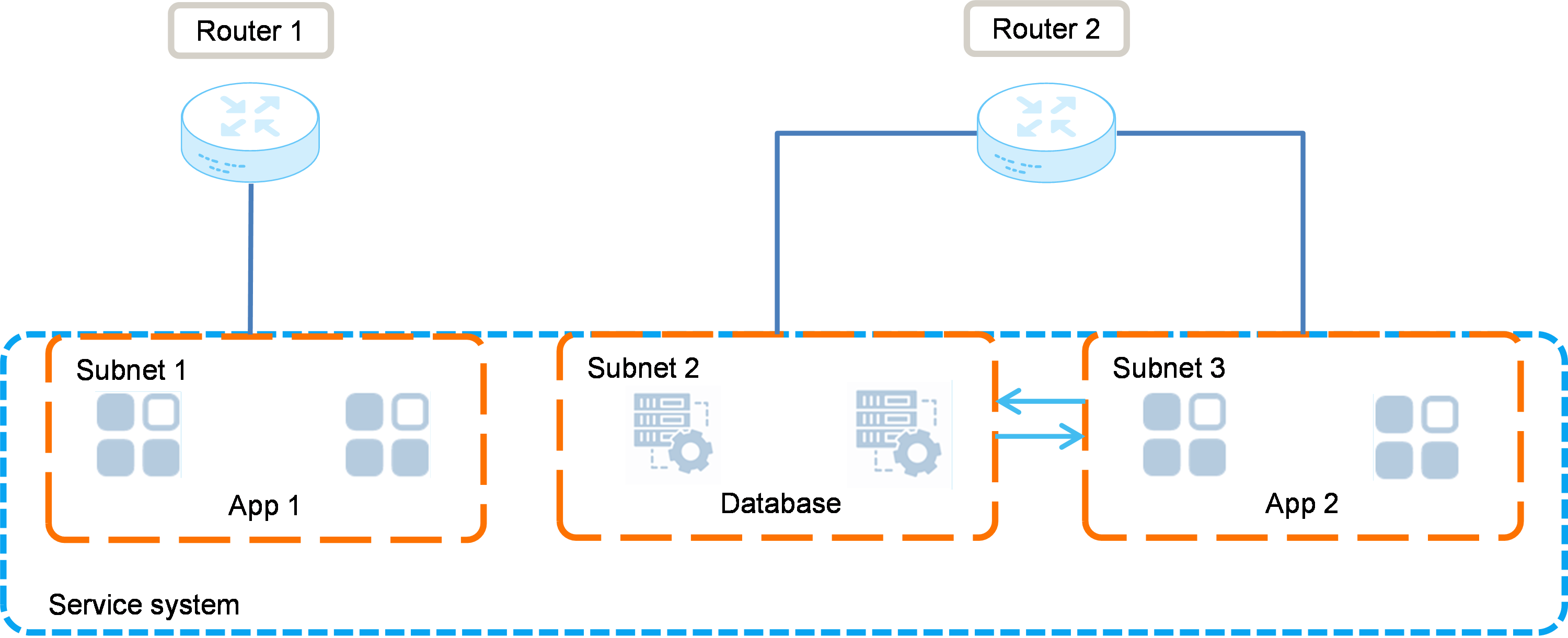
Service system isolation and interconnection
To isolate services, deploy the services in different subnets. For the isolated services to communicate with each other, attach the same router to the subnets.
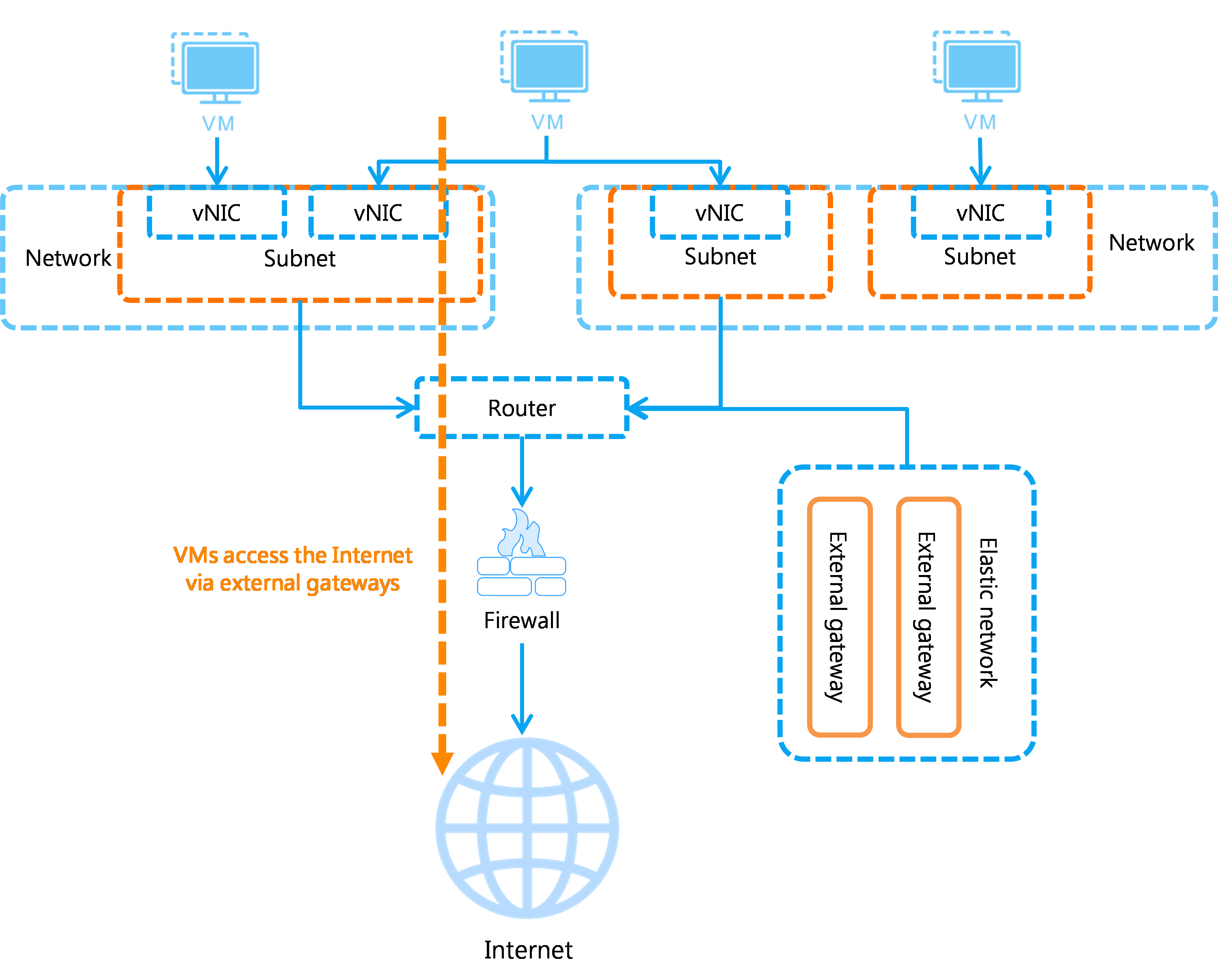
Public network access from cloud hosts
For a cloud host to access the public network, configure an external gateway for the router of the cloud host's subnet, and attach a gateway to the router. Then, all cloud hosts in the subnet can access the Internet through the external gateway.
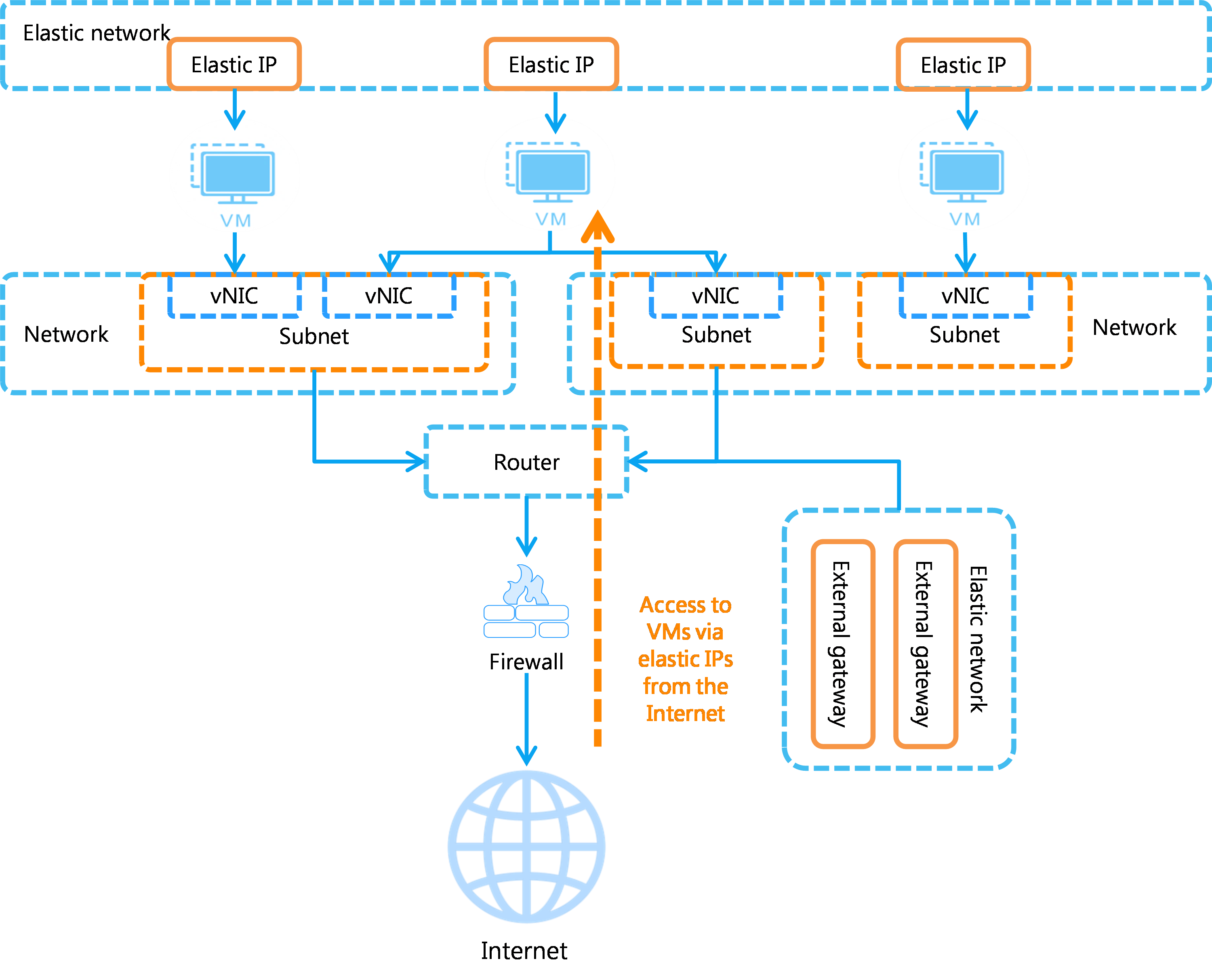
Cloud host access from the public network
To access a cloud host from the Internet, configure an external gateway for the router of the host's subnet, and attach a firewall to the router. Then, all cloud hosts in the subnet can access the Internet through the elastic IP addresses.
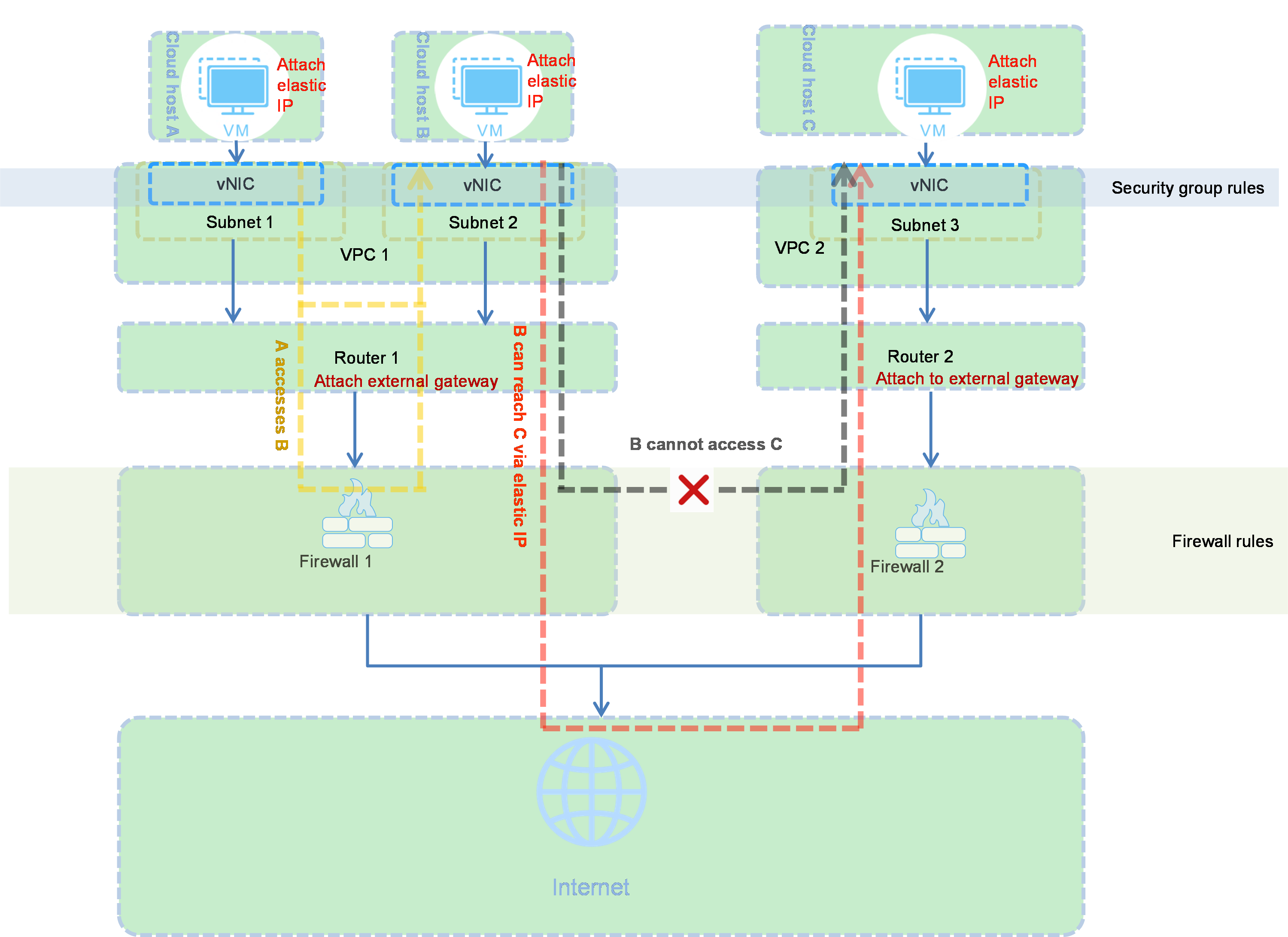
Cloud host security protection
Cloud host security is provided by private network, security group, and firewall.
By default, cloud hosts in the same private network can reach each other. For cloud hosts in different private networks to reach each other, firewall settings and public IP addresses must be configured.
Security groups are created on a router to isolate cloud hosts from the same or different subnets, providing cloud host-level protection. For cloud hosts in a security group, whether traffic can be received from a source or sent to a destination is controlled by the rules configured for the security group.
Firewall provides network-level protection for inter-cloud host access and communication between cloud hosts and the external network. It is applicable to scenarios with high security requirements.
Figure-1 Cloud host security protection
Relationship with other cloud services
Cloud host/bare metal node
Classic networks provide a secure and isolated private network environment for cloud hosts and bare metal nodes in a private cloud.
Elastic IP address
Elastic networks provide IP address pools for elastic IP addresses in the system.
A router uses its associated elastic network to configure the external gateway and connect to the firewall. Then, the cloud hosts in the subnet associated with the router can access the Internet.
Associating cloud hosts with elastic IP addresses and binding a router to an external gateway allow accesses to cloud hosts in the classic network from the Internet.
Security group
A security group contains a group of cloud hosts that have the same security protection requirements and trust each other.
Firewall
A firewall controls communication between cloud hosts and the external network. For a cloud host to communicate with the external network, you must attach the router of the host's subnet to a firewall.
VPN
Virtual private network (VPN) establishes an encrypted communication tunnel for two specific peers to achieve secure transmission. You can use VPN to connect cloud networks and traditional networks to safeguard communication between cloud resources and datacenter resources.
Load balancing
Load balancing distributes private network traffic to multiple cloud hosts to balance loads.
Concepts
Subnet
A subnet of a classic network is created by a system administrator on the System > Organization Management > Quotas page for organizations to assign private IP addresses to cloud hosts. For cloud hosts with different service requirements, you can create multiple subnets.
Router
A router configured for a subnet provides Source Network Address Translation (SNAT) for the subnet. When a cloud host attempts to access the external network through a router, the router replaces the source IP address with a public IP address and generates an NAT forwarding entry. When a response comes from the external network, the router checks the NAT table and replaces the private IP address back. This enables cloud hosts to communicate with the external network.