Configure an INFOSEC encryption module
Prerequisites
Configure the encryption module according to the manufacturer's instructions and ensure the network connectivity between the encryption module and the system.
Obtain the IP address and port information of the encryption module in advance.
Configuration flow
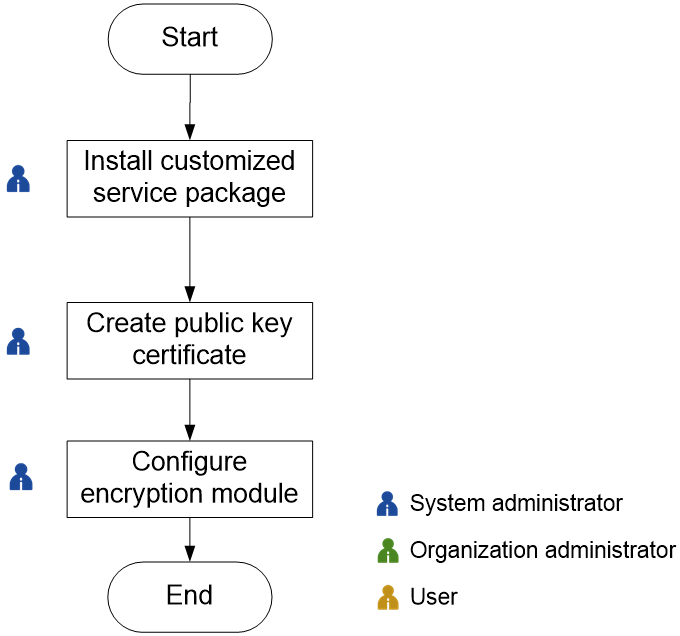
Figure-1 Configuration flow
Table-1 Configuration flow
|
Task |
Description |
|
Install cloud service installation package and components |
Upload and deploy corresponding cloud service installation package and components in advance. For more information, see "Configure cloud services and system components." |
|
Create a public key certificate provided by the manufacturer in the system in advance. |
|
|
Configure INFOSEC encryption module. |
Create public key certificate
|
Obtain the public key certificate file provided by the third-party manufacturer of the encryption module in advance. |
On the top navigation bar, click System.
From the left navigation pane, select System Settings > Security Settings > Public Key Certificate.
Click Create Public Key Certificate. Configure public key certificate parameters.
Table-2 Configuring public key certificate parameters
|
Parameter |
Description |
|
Certificate Name |
Specify the name of the customized certificate. |
|
Public Key Subject |
Specify the subject of the public key certificate. |
|
Public Key Certificate |
Enter the public key certificate. |
Click OK.
Configure the encryption module
On the top navigation bar, click System.
From the left navigation pane, select System Settings > Security Settings > Encryption Module Settings.
Click Create Encryption Module Settings. Configure parameters for the encryption module.
Click Test Connectivity to test the connectivity of the encryption module.
Table-3 Configuring encryption module parameters
|
Parameter |
Description |
|
Platform Name |
Specify the name of the encryption platform. |
|
appId |
Enter the App ID obtained from the manufacturer. |
|
SecretKey |
Enter the secret key obtained from the manufacturer. |
|
IP/Port |
Enter the obtained encryption module IP or port. |
|
Protocol |
HTTP protocol is supported. |
Management and maintenance
Edit public key certificate
On the top navigation bar, click System.
From the left navigation pane, select System Settings > Security Settings > Public Key Certificate.
Select the target public key certificate. Click Edit. Configure public key certificate parameters.
Click OK.
Enable public key certificate
On the top navigation bar, click System.
From the left navigation pane, select System Settings > Security Settings > Public Key Certificate.
Select the target public key certificate. Click Enable.
Click OK.
Delete public key certificate
|
Deleting public key certificates will make corresponding users unable to log in normally. Perform this operation with caution. |
On the top navigation bar, click System.
From the left navigation pane, select System Settings > Security Settings > Public Key Certificate.
Select the target public key certificate. Click Delete.