- Table of Contents
-
- 10-Security Configuration Guide
- 00-Preface
- 01-AAA configuration
- 02-802.1X configuration
- 03-MAC authentication configuration
- 04-Portal configuration
- 05-Port security configuration
- 06-Password control configuration
- 07-Keychain configuration
- 08-Public key management
- 09-PKI configuration
- 10-IPsec configuration
- 11-SSH configuration
- 12-SSL configuration
- 13-Attack detection and prevention configuration
- 14-TCP attack prevention configuration
- 15-IP source guard configuration
- 16-ARP attack protection configuration
- 17-ND attack defense configuration
- 18-uRPF configuration
- 19-MFF configuration
- 20-FIPS configuration
- 21-MACsec configuration
- 22-802.1X client configuration
- 23-Web authentication configuration
- 24-Object group configuration
- 25-Triple authentication configuration
- Related Documents
-
| Title | Size | Download |
|---|---|---|
| 17-ND attack defense configuration | 105.81 KB |
Configuration restrictions and guidelines
ND attack defense configuration task list
Enabling source MAC consistency check for ND messages
Configuring ND attack detection
Configuring ND attack detection
Configuring ND attack detection for a VSI
Enabling ND attack detection logging
Displaying and maintaining ND attack detection
ND attack detection configuration example
Specifying the role of the attached device
Configuring an RA guard policy
Enabling the RA guard logging feature
Displaying and maintaining RA guard
RA guard configuration example
Configuring ND attack defense
Overview
IPv6 Neighbor Discovery (ND) attack defense is able to identify forged ND messages to prevent ND attacks.
The IPv6 ND protocol does not provide any security mechanisms and is vulnerable to network attacks. An attacker can send the following forged ICMPv6 messages to perform ND attacks:
· Forged NS/NA/RS messages with an IPv6 address of a victim host. The gateway and other hosts update the ND entry for the victim with incorrect address information. As a result, all packets intended for the victim are sent to the attacking terminal.
· Forged RA messages with the IPv6 address of a victim gateway. As a result, all hosts attached to the victim gateway maintain incorrect IPv6 configuration parameters and ND entries.
For information about the IPv6 ND protocol, see Layer 3–IP Services Configuration Guide.
Table 1 ND attack defense features at a glance
|
ND attack defense feature |
To block |
|
Source MAC consistency check |
ND messages in which the Ethernet frame header and the source link-layer address option of the ND message contain different source MAC addresses. |
|
ND attack detection |
ND messages in which the mapping between the source IPv6 address and the source MAC address is invalid. |
|
RA guard |
RA messages incompliant with the RA guard policy or identified to be sent from hosts. |
Configuration restrictions and guidelines
In an IRF 3.1 system, do not configure ND attack defense on PEXs.
ND attack defense configuration task list
|
Tasks at a glance |
|
(Optional.) Enabling source MAC consistency check for ND messages (applicable to gateways) |
|
(Optional.) Configuring ND attack detection (applicable to access devices) |
|
(Optional.) Configuring RA guard (applicable to Layer 2 access devices) |
Enabling source MAC consistency check for ND messages
The source MAC consistency check feature is typically configured on gateways to prevent ND attacks.
This feature checks the source MAC address and the source link-layer address for consistency for each arriving ND message.
· If the source MAC address and the source link-layer address are not the same, the device drops the packet.
· If the addresses are the same, the device continues learning ND entries.
The ND logging feature logs source MAC inconsistency events, and it sends the log messages to the information center. The information center can then output log messages from different source modules to different destinations. For more information about the information center, see Network Management and Monitoring Configuration Guide.
To enable source MAC consistency check for ND messages:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enable source MAC consistency check for ND messages. |
ipv6 nd mac-check enable |
By default, source MAC consistency check is disabled for ND messages. |
|
3. (Optional.) Enable the ND logging feature. |
ipv6 nd check log enable |
By default, the ND logging feature is disabled. As a best practice, disable the ND logging feature to avoid excessive ND logs. |
Configuring ND attack detection
About ND attack detection
ND attack detection checks incoming ND messages for user validity to prevent spoofing attacks. It is typically configured on access devices. It supports the following features:
· User validity check.
· ND attack detection for a VSI.
· ND attack detection logging.
ND attack detection defines the following types of interfaces:
· ND trusted interface—The device directly forwards ND messages or data packets received by ND trusted interfaces. It does not perform user validity check.
· ND untrusted interface—The device discards RA and redirect messages received by ND untrusted interfaces. For other types of ND messages received by the ND untrusted interfaces, the device checks the user validity.
ND attack detection compares the source IPv6 address and the source MAC address in an incoming ND message against security entries from other modules.
· If a match is found, the device verifies the user as legal in the receiving VLAN, and it forwards the packet.
· If no match is found, the device verifies the user as illegal, and it discards the ND message.
ND attack detection uses the following security entries for user validity check:
· Static IPv6 source guard binding entries, which are created by using the ipv6 source binding command. For information about IPv6 source guard, see "Configuring IP source guard."
· ND snooping entries. For information about ND snooping, see Layer 3–IP Services Configuration Guide.
· DHCPv6 snooping entries. For information about DHCPv6 snooping, see Layer 3–IP Services Configuration Guide.
Configuration guidelines
Make sure one or more of the following features are configured to prevent ND untrusted interfaces from dropping all received ND messages:
· IPv6 source guard static bindings.
To make the bindings effective for ND attack detection, you must specify the vlan vlan-id option in the ipv6 source binding command, and enable ND attack detection for the same VLAN.
· DHCPv6 snooping.
· ND snooping.
Configuring ND attack detection
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter VLAN view. |
vlan vlan-id |
N/A |
|
3. Enable ND attack detection. |
ipv6 nd detection enable |
By default, ND attack detection is disabled. |
|
4. Return to system view. |
quit |
N/A |
|
5. Enter Layer 2 Ethernet or aggregate interface view. |
interface interface-type interface-number |
N/A |
|
6. (Optional.) Configure the interface as ND trusted interface. |
ipv6 nd detection trust |
By default, all interfaces are ND untrusted interfaces. |
Configuring ND attack detection for a VSI
On a VXLAN network, you can configure user validity check for the associated VSI on the VTEP device. Different from the user validity check within a VLAN, which is performed on ND untrusted interfaces, the user validity check for a VSI is performed on ND untrusted ACs. The security entries used for user validity check and the check process are the same for a VLAN and a VSI.
Ethernet service instances that are associated with the VSI of a VXLAN are ACs. For more information, see VXLAN Configuration Guide.
To configure ND attack detection for a VSI:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter VSI view. |
vsi vsi-name |
N/A |
|
3. Enable ND attack detection. |
ipv6 nd detection enable |
By default, ND attack detection is disabled. |
|
4. Return to system view. |
quit |
N/A |
|
5. Enter Layer 2 Ethernet or aggregate interface view. |
interface interface-type interface-number |
N/A |
|
6. Enter Ethernet service instance view. |
service-instance instance-id |
|
|
7. (Optional.) Configure the AC as ND trusted AC. |
ipv6 nd detection trust |
By default, all ACs are ND untrusted ACs. |
Enabling ND attack detection logging
After you enable ND attack detection logging, the device generates a log to record the following information when it detects invalid ND packets:
· Victim port numbers in a VLAN.
· IDs of the victim Ethernet service instances in a VXLAN.
· Source IP address of the invalid ND packets.
· Source MAC address of the invalid ND packets.
· VLAN ID of the invalid ND packets.
· Total number of dropped ND packets.
To enable ND attack detection logging:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enable ND attack detection logging. |
ipv6 nd detection log enable |
By default, ND attack detection logging is disabled. |
Displaying and maintaining ND attack detection
Execute display commands in any view and reset commands in user view.
|
Task |
Command |
|
Display statistics for ND messages dropped by ND attack detection. |
display ipv6 nd detection statistics [ interface interface-type interface-number ] [ service-instance instance-id ] |
|
Clear ND attack detection statistics. |
reset ipv6 nd detection statistics [ interface interface-type interface-number ] [ service-instance instance-id ] |
ND attack detection configuration example
Network requirements
As shown in Figure 1, configure ND attack detection on Device B to check user validity for ND messages from Host A and Host B.
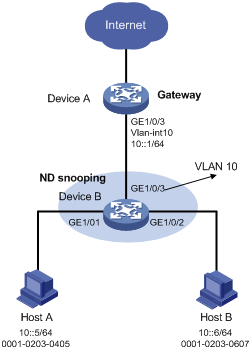
Configuration procedure
# Create VLAN 10.
<DeviceA> system-view
[DeviceA] vlan 10
[DeviceA-vlan10] quit
# Configure GigabitEthernet 1/0/3 to trunk VLAN 10.
[DeviceA] interface gigabitethernet 1/0/3
[DeviceA-GigabitEthernet1/0/3] port link-type trunk
[DeviceA-GigabitEthernet1/0/3] port trunk permit vlan 10
[DeviceA-GigabitEthernet1/0/3] quit
# Assign IPv6 address 10::1/64 to VLAN-interface 10.
[DeviceA] interface vlan-interface 10
[DeviceA-Vlan-interface10] ipv6 address 10::1/64
[DeviceA-Vlan-interface10] quit
2. Configure Device B:
# Create VLAN 10.
<DeviceB> system-view
[DeviceB] vlan 10
[DeviceB-vlan10] quit
# Configure GigabitEthernet 1/0/1, GigabitEthernet 1/0/2, and GigabitEthernet 1/0/3 to trunk VLAN 10.
[DeviceB] interface gigabitethernet 1/0/1
[DeviceB-GigabitEthernet1/0/1] port link-type access
[DeviceB-GigabitEthernet1/0/1] port access vlan 10
[DeviceB-GigabitEthernet1/0/1] quit
[DeviceB] interface gigabitethernet 1/0/2
[DeviceB-GigabitEthernet1/0/2] port link-type access
[DeviceB-GigabitEthernet1/0/2] port access vlan 10
[DeviceB-GigabitEthernet1/0/2] quit
[DeviceB] interface gigabitethernet 1/0/3
[DeviceB-GigabitEthernet1/0/3] port link-type trunk
[DeviceB-GigabitEthernet1/0/3] port trunk permit vlan 10
[DeviceB-GigabitEthernet1/0/3] quit
# Enable ND attack detection for VLAN 10.
[DeviceB] vlan 10
[DeviceB-vlan10] ipv6 nd detection enable
# Enable ND snooping for IPv6 global unicast addresses and ND snooping for IPv6 link-local addresses in VLAN 10.
[DeviceB-vlan10] ipv6 nd snooping enable global
[DeviceB-vlan10] ipv6 nd snooping enable link-local
[DeviceB-vlan10] quit
# Configure GigabitEthernet 1/0/3 as ND trusted interface.
[DeviceB] interface gigabitethernet 1/0/3
[DeviceB-GigabitEthernet1/0/3] ipv6 nd detection trust
The configuration allows Device B to inspect all ND messages received by GigabitEthernet 1/0/1 and GigabitEthernet 1/0/2 based on the ND snooping entries.
Configuring RA guard
About RA guard
RA guard allows Layer 2 access devices to analyze and block unwanted and forged RA messages.
Upon receiving an RA message, the device makes the forwarding or dropping decision based on the role of the attached device or the RA guard policy.
1. If the role of the device attached to the port is router, the device forwards all RA messages received on the port. If the role is host, the device directly drops all RA messages received on the port.
2. If no role is set for the port, the device uses the RA guard policy to match the information found in the RA message.
¡ If the RA message content matches every criterion in the policy, the device forwards the message.
¡ If the RA message content is not validated, the device drops the message.
Specifying the role of the attached device
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter Layer 2 Ethernet or aggregate interface view. |
interface interface-type interface-number |
N/A |
|
3. Specify the role of the device attached to the port. |
ipv6 nd raguard role { host | router } |
By default, the role of the device attached to the port is not specified. Make sure your setting is consistent with the device type. |
Configuring an RA guard policy
Configure an RA guard policy if you do not specify a role for the attached device or if you want to filter the RA messages sent by a router.
To configure an RA guard policy:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Create an RA guard policy and enter its view. |
ipv6 nd raguard policy policy-name |
By default, no RA guard policies exist. If the policy does not contain match criteria, the policy will not take effect and the device drops all received RA messages. |
|
3. (Optional.) Specify an ACL match criterion. |
if-match acl { ipv6-acl-number | name ipv6-acl-name } |
By default, no ACL match criterion exists. |
|
4. (Optional.) Specify a prefix match criterion. |
if-match prefix acl { ipv6-acl-number | name ipv6-acl-name } |
By default, no prefix match criterion exists. |
|
5. (Optional.) Specify a router preference match criterion. |
if-match router-preference maximum { high | low | medium } |
By default, no router preference match criterion exists. |
|
6. (Optional.) Specify an M flag match criterion. |
if-match autoconfig managed-address-flag { off | on } |
By default, no M flag match criterion exists. |
|
7. (Optional.) Specify an O flag match criterion. |
if-match autoconfig other-flag { off | on } |
By default, no O flag match criterion exists. |
|
8. (Optional.) Specify a maximum or minimum hop limit match criterion. |
if-match hop-limit { maximum | minimum } limit |
By default, no hop limit match criterion exists. |
|
9. Quit RA guard policy view. |
quit |
N/A |
|
10. Enter VLAN view. |
vlan vlan-number |
N/A |
|
11. Apply an RA guard policy to the VLAN. |
ipv6 nd raguard apply policy [ policy-name ] |
By default, no RA guard policy is applied to the VLAN. |
Enabling the RA guard logging feature
This feature allows a device to generate logs when it detects forged RA messages. Each log records the following information:
· Name of the interface that received the forged RA message.
· Source IP address of the forged RA message.
· Number of RA messages dropped on the interface.
The RA guard logging feature sends the log messages to the information center. The information center can then output log messages from different source modules to different destinations. For more information about the information center, see Network Management and Monitoring Configuration Guide.
To enable the RA guard logging feature:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enable the RA guard logging feature. |
ipv6 nd raguard log enable |
By default, the RA guard logging feature is disabled. |
Displaying and maintaining RA guard
Execute display commands in any view and reset commands in user view.
|
Task |
Command |
|
Display the RA guard policy configuration. |
display ipv6 nd raguard policy [ policy-name ] |
|
Display RA guard statistics. |
display ipv6 nd raguard statistics [ interface interface-type interface-number ] |
|
Clear RA guard statistics. |
reset ipv6 nd raguard statistics [ interface interface-type interface-number ] |
RA guard configuration example
Network requirements
As shown in Figure 2, GigabitEthernet 1/0/1, GigabitEthernet 1/0/2, and GigabitEthernet 1/0/3 of Device B are in VLAN 10.
Configure RA guard on Device B to filter forged and unwanted RA messages.
· Configure an RA policy in VLAN 10 for GigabitEthernet 1/0/2 to filter all RA messages received from the unknown device.
· Specify host as the role of the host. All RA messages received on GigabitEthernet 1/0/1 are dropped.
· Specify router as the role of the Device A. All RA messages received on GigabitEthernet 1/0/3 are forwarded.
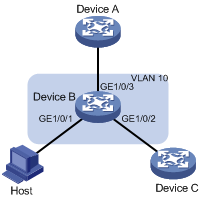
Configuration procedure
# Create an RA guard policy named policy1.
<DeviceB> system-view
[DeviceB] ipv6 nd raguard policy policy1
# Set the maximum router preference to high for the RA guard policy.
[DeviceB-raguard-policy-policy1] if-match router-preference maximum high
# Specify on as the M flag match criterion for the RA guard policy.
[DeviceB-raguard-policy-policy1] if-match autoconfig managed-address-flag on
# Specify on as the O flag match criterion for the RA guard policy.
[DeviceB-raguard-policy-policy1] if-match autoconfig other-flag on
# Set the maximum advertised hop limit to 120 for the RA guard policy.
[DeviceB-raguard-policy-policy1] if-match hop-limit maximum 120
# Set the minimum advertised hop limit to 100 for the RA guard policy.
[DeviceB-raguard-policy-policy1] if-match hop-limit minimum 100
[DeviceB-raguard-policy-policy1] quit
# Assign GigabitEthernet 1/0/1 and GigabitEthernet 1/0/2 to VLAN 10.
[DeviceB] interface gigabitethernet 1/0/1
[DeviceB-GigabitEthernet1/0/1] port link-type access
[DeviceB-GigabitEthernet1/0/1] port access vlan 10
[DeviceB-GigabitEthernet1/0/1] quit
[DeviceB] interface gigabitethernet 1/0/2
[DeviceB-GigabitEthernet1/0/2] port link-type access
[DeviceB-GigabitEthernet1/0/2] port access vlan 10
[DeviceB-GigabitEthernet1/0/2] quit
# Configure GigabitEthernet 1/0/3 to trunk VLAN 10.
[DeviceB] interface gigabitethernet 1/0/3
[DeviceB-GigabitEthernet1/0/3] port link-type trunk
[DeviceB-GigabitEthernet1/0/3] port trunk permit vlan 10
[DeviceB-GigabitEthernet1/0/3] quit
# Apply the RA guard policy policy1 to VLAN 10.
[DeviceB] vlan 10
[DeviceB-vlan10] ipv6 nd raguard apply policy policy1
[DeviceB-vlan10] quit
# Specify host as the role of the device attached to GigabitEthernet 1/0/1.
[DeviceB] interface gigabitethernet 1/0/1
[DeviceB-GigabitEthernet1/0/1] ipv6 nd raguard role host
[DeviceB-GigabitEthernet1/0/1] quit
# Specify router as the role of the device attached to GigabitEthernet 1/0/3.
[DeviceB] interface gigabitethernet 1/0/3
[DeviceB-GigabitEthernet1/0/3] ipv6 nd raguard role router
[DeviceB-GigabitEthernet1/0/3] quit
Verifying the configuration
# Verify that the device forwards or drops RA messages received on GigabitEthernet 1/0/2 based on the RA guard policy. (Details not shown.)
# Verify that the device drops RA messages received on GigabitEthernet 1/0/1. (Details not shown.)
# Verify that the device forwards RA messages received on GigabitEthernet 1/0/3 to other ports in VLAN 10. (Details not shown.)

