本举例是在M9000-AI-E8的R9071版本上进行配置和验证的。
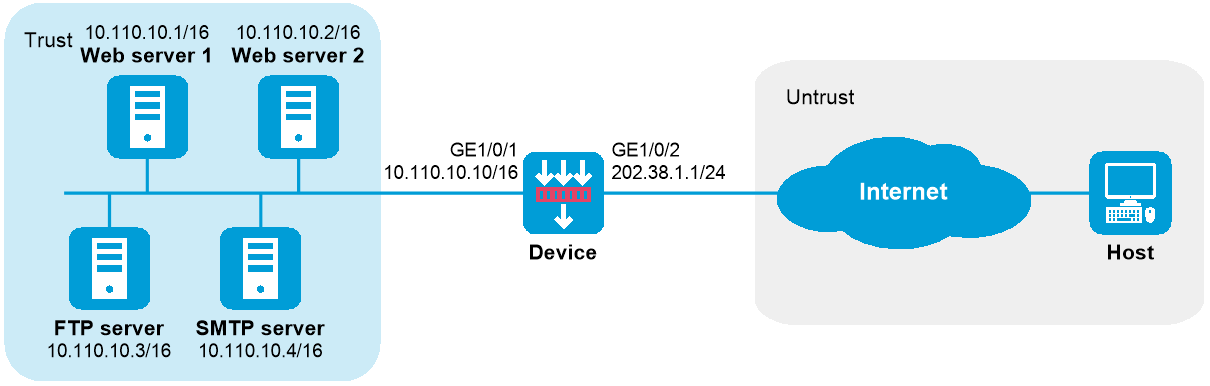
如下图所示,某公司内部对外提供Web、FTP和SMTP服务,而且提供两台Web服务器。公司内部网址为10.110.0.0/16。其中,内部FTP服务器地址为10.110.10.3/16,内部Web服务器1的IP地址为10.110.10.1/16,内部Web服务器2的IP地址为10.110.10.2/16,内部SMTP服务器IP地址为10.110.10.4/16。公司拥有202.38.1.1至202.38.1.3三个公网IP地址。需要实现如下功能:
外部的主机可以访问内部的服务器。
选用202.38.1.1作为公司对外提供服务的IP地址,Web服务器2对外采用8080端口。
图-1 外网用户通过外网地址访问内网服务器配置组网图
# 配置接口IP地址、路由、安全域及域间策略保证网络可达,具体配置步骤略。
# 进入接口GigabitEthernet1/0/2。
<Device> system-view
[Device] interface gigabitethernet 1/0/2
# 配置内部FTP服务器,允许外网主机使用地址202.38.1.1、端口号21访问内网FTP服务器。
[Device-GigabitEthernet1/0/2] nat server protocol tcp global 202.38.1.1 21 inside 10.110.10.3 ftp
# 配置内部Web服务器1,允许外网主机使用地址202.38.1.1、端口号80访问内网Web服务器1。
[Device-GigabitEthernet1/0/2] nat server protocol tcp global 202.38.1.1 80 inside 10.110.10.1 http
# 配置内部Web服务器2,允许外网主机使用地址202.38.1.1、端口号8080访问内网Web服务器2。
[Device-GigabitEthernet1/0/2] nat server protocol tcp global 202.38.1.1 8080 inside 10.110.10.2 http
# 配置内部SMTP服务器,允许外网主机使用地址202.38.1.1以及SMTP协议定义的端口访问内网SMTP服务器。
[Device-GigabitEthernet1/0/2] nat server protocol tcp global 202.38.1.1 smtp inside 10.110.10.4 smtp
[Device-GigabitEthernet1/0/2] quit
# 以上配置完成后,外网Host能够通过NAT地址访问各内网服务器。通过查看如下显示信息,可以验证以上配置成功。
[Device] display nat all
NAT internal server information:
Totally 4 internal servers.
Interface: GigabitEthernet1/0/2
Protocol: 6(TCP)
Global IP/port: 202.38.1.1/21
Local IP/port : 10.110.10.3/21
Rule name : ServerRule_1
NAT counting : 0
Config status : Active
Interface: GigabitEthernet1/0/2
Protocol: 6(TCP)
Global IP/port: 202.38.1.1/25
Local IP/port : 10.110.10.4/25
Rule name : ServerRule_4
NAT counting : 0
Config status : Active
Interface: GigabitEthernet1/0/2
Protocol: 6(TCP)
Global IP/port: 202.38.1.1/80
Local IP/port : 10.110.10.1/80
Rule name : ServerRule_2
NAT counting : 0
Config status : Active
Interface: GigabitEthernet1/0/2
Protocol: 6(TCP)
Global IP/port: 202.38.1.1/8080
Local IP/port : 10.110.10.2/80
Rule name : ServerRule_3
NAT counting : 0
Config status : Active
NAT logging:
Log enable : Disabled
Flow-begin : Disabled
Flow-end : Disabled
Flow-active : Disabled
Port-block-assign : Disabled
Port-block-withdraw : Disabled
Alarm : Disabled
NO-PAT IP usage : Disabled
NAT mapping behavior:
Mapping mode : Address and Port-Dependent
ACL : ---
Config status: Active
NAT ALG:
DNS : Enabled
FTP : Enabled
H323 : Disabled
ICMP-ERROR : Enabled
ILS : Disabled
MGCP : Disabled
NBT : Disabled
PPTP : Enabled
RTSP : Enabled
RSH : Disabled
SCCP : Disabled
SCTP : Disabled
SIP : Disabled
SQLNET : Disabled
TFTP : Disabled
XDMCP : Disabled
Static NAT load balancing: Disabled
NAT link-switch recreate-session: Disabled
NAT configuration-for-new-connection: Disabled
# 通过以下显示命令,可以看到Host访问FTP server时生成NAT会话信息。
[Device] display nat session verbose
Slot 1:
Initiator:
Source IP/port: 202.38.1.2/52802
Destination IP/port: 202.38.1.1/21
DS-Lite tunnel peer: -
VPN instance/VLAN ID/Inline ID: -/-/-
Protocol: TCP(6)
Inbound interface: GigabitEthernet1/0/2
Source security zone: Untrust
Responder:
Source IP/port: 10.110.10.3/21
Destination IP/port: 202.38.1.2/52802
DS-Lite tunnel peer: -
VPN instance/VLAN ID/Inline ID: -/-/-
Protocol: TCP(6)
Inbound interface: GigabitEthernet1/0/1
Source security zone: Trust
State: TCP_ESTABLISHED
Application: FTP
Rule ID: -/-/-
Rule name:
Start time: 2017-05-21 11:13:39 TTL: 3597s
Initiator->Responder: 7 packets 313 bytes
Responder->Initiator: 6 packets 330 bytes
Total sessions found: 1
#
interface GigabitEthernet1/0/1
ip address 10.110.10.10 255.255.0.0
#
interface GigabitEthernet1/0/2
ip address 202.38.1.1 255.255.255.0
nat server protocol tcp global 202.38.1.1 21 inside 10.110.10.3 21
nat server protocol tcp global 202.38.1.1 25 inside 10.110.10.4 25
nat server protocol tcp global 202.38.1.1 80 inside 10.110.10.1 80
nat server protocol tcp global 202.38.1.1 8080 inside 10.110.10.2 80
#
security-zone name Trust
import interface GigabitEthernet1/0/1
#
security-zone name Untrust
import interface GigabitEthernet1/0/2
#
security-policy ip
rule 0 name trust-untrust
action pass
source-zone trust
destination-zone untrust
rule 1 name untrust-trust
action pass
source-zone untrust
destination-zone trust