本举例是在M9000-AI-E8的R9071版本上进行配置和验证的。
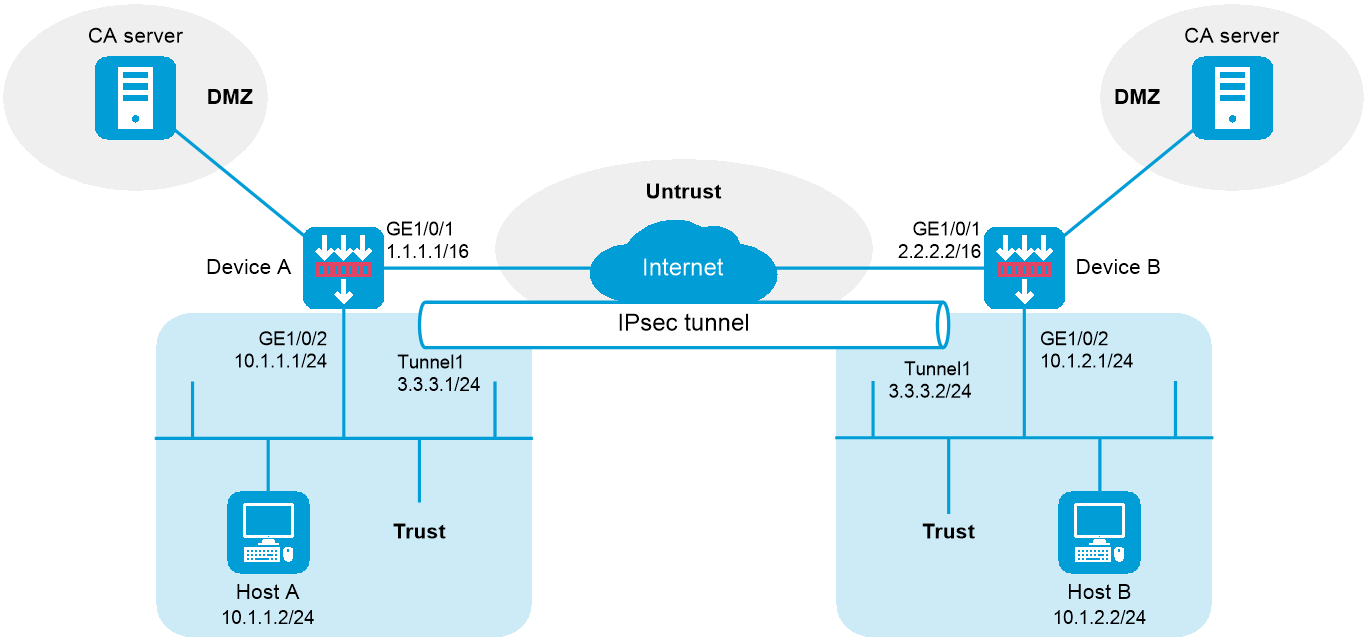
如下图所示,在Device A和Device B之间使用IPsec隧道接口建立IPsec连接,将发送给对端私网的数据流路由到IPsec隧道接口上,由IPsec隧道接口上动态协商建立的IPsec安全隧道对Host A所在子网(10.1.1.0/24)与Host B所在子网(10.1.2.0/24)之间的所有数据流进行安全保护。具体要求如下:
Device A和Device B之间采用IKEv2协商方式建立IPsec SA。
Device A和DeviceB均使用RSA数字签名的认证方法。
Device A侧子网的IP地址为动态分配,并作为发起方。
图-1 IKEv2 RSA数字签名认证配置组网图
|
在开始下面的配置之前,假设Device A已获取到CA证书ca.cer和服务器证书server.pfx。 |
配置接口IP地址
# 根据组网图中规划的信息,配置各接口的IP地址,具体配置步骤如下。
<DeviceA> system-view
[DeviceA] interface gigabitethernet 1/0/1
[DeviceA-GigabitEthernet1/0/1] ip address 1.1.1.1 255.255.0.0
[DeviceA-GigabitEthernet1/0/1] quit
请参考以上步骤配置其他接口的IP地址,具体配置步骤略。
配置路由
本举例仅以静态路由方式配置路由信息。实际组网中,请根据具体情况选择相应的路由配置方式。
# 请根据组网图中规划的信息,配置静态路由,本举例假设到达对端网关设备的下一跳IP地址为1.1.1.2,实际使用中请以具体组网情况为准,具体配置步骤如下。
[DeviceA] ip route-static 2.2.2.2 16 1.1.1.2
配置接口加入安全域。
# 请根据组网图中规划的信息,将接口加入对应的安全域,具体配置步骤如下。
[DeviceA] security-zone name trust
[DeviceA-security-zone-Trust] import interface gigabitethernet 1/0/2
[DeviceA-security-zone-Trust] quit
[DeviceA] security-zone name untrust
[DeviceA-security-zone-Untrust] import interface gigabitethernet 1/0/1
[DeviceA-security-zone-Untrust] quit
配置安全策略
配置安全策略放行Untrust与Local安全域之间的流量,用于设备之间可以建立IPsec隧道。
# 配置名称为ipseclocalout的安全策规则,使Device A可以向Device B发送IPsec隧道协商报文,具体配置步骤如下。
[DeviceA] security-policy ip
[DeviceA-security-policy-ip] rule name ipseclocalout
[DeviceA-security-policy-ip-1-ipseclocalout] source-zone local
[DeviceA-security-policy-ip-1-ipseclocalout] destination-zone untrust
[DeviceA-security-policy-ip-1-ipseclocalout] source-ip-host 1.1.1.1
[DeviceA-security-policy-ip-1-ipseclocalout] destination-ip-host 2.2.2.2
[DeviceA-security-policy-ip-1-ipseclocalout] action pass
[DeviceA-security-policy-ip-1-ipseclocalout] quit
# 配置名称为ipseclocalin的安全策略规则,使Device A可以接收和处理来自Device B的IPsec隧道协商报文,具体配置步骤如下。
[DeviceA-security-policy-ip] rule name ipseclocalin
[DeviceA-security-policy-ip-2-ipseclocalin] source-zone untrust
[DeviceA-security-policy-ip-2-ipseclocalin] destination-zone local
[DeviceA-security-policy-ip-2-ipseclocalin] source-ip-host 2.2.2.2
[DeviceA-security-policy-ip-2-ipseclocalin] destination-ip-host 1.1.1.1
[DeviceA-security-policy-ip-2-ipseclocalin] action pass
[DeviceA-security-policy-ip-2-ipseclocalin] quit
配置安全策略放行Host A与Host B之间的流量
# 配置名称为trust-untrust的安全策略规则,使Host A访问Host B的报文可通,具体配置步骤如下。
[DeviceA-security-policy-ip] rule name trust-untrust
[DeviceA-security-policy-ip-3-trust-untrust] source-zone trust
[DeviceA-security-policy-ip-3-trust-untrust] destination-zone untrust
[DeviceA-security-policy-ip-3-trust-untrust] source-ip-subnet 10.1.1.0 24
[DeviceA-security-policy-ip-3-trust-untrust] destination-ip-subnet 10.1.2.0 24
[DeviceA-security-policy-ip-3-trust-untrust] action pass
[DeviceA-security-policy-ip-3-trust-untrust] quit
# 配置名称为untrust-trust的安全策略规则,使Host B访问Host A的报文可通,具体配置步骤如下。
[DeviceA-security-policy-ip] rule name untrust-trust
[DeviceA-security-policy-ip-4-untrust-trust] source-zone untrust
[DeviceA-security-policy-ip-4-untrust-trust] destination-zone trust
[DeviceA-security-policy-ip-4-untrust-trust] source-ip-subnet 10.1.2.0 24
[DeviceA-security-policy-ip-4-untrust-trust] destination-ip-subnet 10.1.1.0 24
[DeviceA-security-policy-ip-4-untrust-trust] action pass
[DeviceA-security-policy-ip-4-untrust-trust] quit
[DeviceA-security-policy-ip] quit
配置IPsec安全提议,协商封装报文使用的各种安全协议
# 创建IPsec安全提议,两端配置的安全提议参数需要完全相同,具体配置步骤如下。
[DeviceA] ipsec transform-set tran1
[DeviceA-ipsec-transform-set-tran1] encapsulation-mode tunnel
[DeviceA-ipsec-transform-set-tran1] protocol esp
[DeviceA-ipsec-transform-set-tran1] esp encryption-algorithm des-cbc
[DeviceA-ipsec-transform-set-tran1] esp authentication-algorithm sha1
[DeviceA-ipsec-transform-set-tran1] quit
配置PKI实体,设置PKI实体的身份信息
[DeviceA] pki entity entity1
[DeviceA-pki-entity-entity1] common-name devicea
[DeviceA-pki-entity-entity1] quit
配置PKI域,约定PKI证书申请的相关信息
[DeviceA] pki domain domain1
[DeviceA-pki-domain-domain1] public-key rsa general name rsa1
[DeviceA-pki-domain-domain1] undo crl check enable
[DeviceA-pki-domain-domain1] quit
[DeviceA] pki import domain domain1 der ca filename ca.cer
[DeviceA] pki import domain domain1 p12 local filename server.pfx
配置证书访问策略,对用户访问权限进行进一步的控制
[DeviceA] pki certificate access-control-policy policy1
[DeviceA-pki-cert-acp-policy1] rule 1 permit group1
[DeviceA] pki certificate attribute-group group1
[DeviceA-pki-cert-attribute-group-group1] attribute 1 subject-name dn ctn 1
对端证书subject-name DN中需包含(ctn)规则中定义的字符串才被认为是有效的证书。本例使用的证书subject-name DN中包含字符“1”,因此在这里使用参数ctn 1。
配置IKEv2 profile,约定建立IKE SA所需的安全参数
[DeviceA] ikev2 profile profile1
[DeviceA-ikev2-profile-profile1] authentication-method local rsa-signature
[DeviceA-ikev2-profile-profile1] authentication-method remote rsa-signature
[DeviceA-ikev2-profile-profile1] certificate domain domain1
[DeviceA-ikev2-profile-profile1] identity local dn
[DeviceA-ikev2-profile-profile1] match remote certificate policy1
[DeviceA-ikev2-profile-profile1] quit
配置IPsec安全框架,建立IPsec隧道,保护需要防护的数据流
[DeviceA] ipsec profile abc isakmp
[DeviceA-ipsec-profile-isakmp-abc] transform-set tran1
[DeviceA-ipsec-profile-isakmp-abc] ikev2-profile profile1
[DeviceA-ipsec-profile-isakmp-abc] quit
配置IPsec隧道接口,用于对需要保护的流量进行IPsec封装
# 创建IPsec隧道接口,并引用IPsec安全框架。
[DeviceA] interface tunnel 1 mode ipsec
[DeviceA-Tunnel1] ip address 3.3.3.1 255.255.255.0
[DeviceA-Tunnel1] source 1.1.1.1
[DeviceA-Tunnel1] destination 2.2.2.2
[DeviceA-Tunnel1] tunnel protection ipsec profile abc
[DeviceA-Tunnel1] quit
# 将IPsec隧道接口加入Untrust安全域。
[DeviceA] security-zone name untrust
[DeviceA-security-zone-Untrust] import interface tunnel 1
[DeviceA-security-zone-Untrust] quit
# 请根据组网图中规划的信息,配置静态路由,将需要保护的流量引入IPsec隧道接口,本举例的IPsec隧道接口为Tunnel1。
[DeviceA] ip route-static 10.1.2.0 255.255.255.0 tunnel 1
|
在开始下面的配置之前,假设Device B已获取到CA证书ca.cer和服务器证书server.pfx。 |
配置接口IP地址
# 根据组网图中规划的信息,配置各接口的IP地址,具体配置步骤如下。
<DeviceB> system-view
[DeviceB] interface gigabitethernet 1/0/1
[DeviceB-GigabitEthernet1/0/1] ip address 2.2.2.2 255.255.0.0
[DeviceB-GigabitEthernet1/0/1] quit
请参考以上步骤配置其他接口的IP地址,具体配置步骤略。
配置路由
本举例仅以静态路由方式配置路由信息。实际组网中,请根据具体情况选择相应的路由配置方式。
# 请根据组网图中规划的信息,配置静态路由,本举例假设对端网关设备的下一跳IP地址为2.2.2.1,实际使用中请以具体组网情况为准,具体配置步骤如下。
[DeviceB] ip route-static 1.1.1.1 16 2.2.2.1
配置接口加入安全域。
# 请根据组网图中规划的信息,将接口加入对应的安全域,具体配置步骤如下。
[DeviceB] security-zone name trust
[DeviceB-security-zone-Trust] import interface gigabitethernet 1/0/2
[DeviceB-security-zone-Trust] quit
[DeviceB] security-zone name untrust
[DeviceB-security-zone-Untrust] import interface gigabitethernet 1/0/1
[DeviceB-security-zone-Untrust] quit
配置安全策略
配置安全策略放行Untrust与Local安全域之间的流量,用于设备之间可以建立IPsec隧道。
# 配置名称为ipseclocalout的安全策规则,使Device B可以向Device A发送IPsec隧道协商报文,具体配置步骤如下。
[DeviceB] security-policy ip
[DeviceB-security-policy-ip] rule name ipseclocalout
[DeviceB-security-policy-ip-1-ipseclocalout] source-zone local
[DeviceB-security-policy-ip-1-ipseclocalout] destination-zone untrust
[DeviceB-security-policy-ip-1-ipseclocalout] source-ip-host 2.2.2.2
[DeviceB-security-policy-ip-1-ipseclocalout] destination-ip-host 1.1.1.1
[DeviceB-security-policy-ip-1-ipseclocalout] action pass
[DeviceB-security-policy-ip-1-ipseclocalout] quit
# 配置名称为ipseclocalin的安全策略规则,使Device B可以接收和处理来自Device A的IPsec隧道协商报文,具体配置步骤如下。
[DeviceB-security-policy-ip] rule name ipseclocalin
[DeviceB-security-policy-ip-2-ipseclocalin] source-zone untrust
[DeviceB-security-policy-ip-2-ipseclocalin] destination-zone local
[DeviceB-security-policy-ip-2-ipseclocalin] source-ip-host 1.1.1.1
[DeviceB-security-policy-ip-2-ipseclocalin] destination-ip-host 2.2.2.2
[DeviceB-security-policy-ip-2-ipseclocalin] action pass
[DeviceB-security-policy-ip-2-ipseclocalin] quit
配置安全策略放行Host B与Host A之间的流量
# 配置名称为trust-untrust的安全策略规则,使Host B访问Host A的报文可通,具体配置步骤如下。
[DeviceB-security-policy-ip] rule name trust-untrust
[DeviceB-security-policy-ip-3-trust-untrust] source-zone trust
[DeviceB-security-policy-ip-3-trust-untrust] destination-zone untrust
[DeviceB-security-policy-ip-3-trust-untrust] source-ip-subnet 10.1.2.0 24
[DeviceB-security-policy-ip-3-trust-untrust] destination-ip-subnet 10.1.1.0 24
[DeviceB-security-policy-ip-3-trust-untrust] action pass
[DeviceB-security-policy-ip-3-trust-untrust] quit
# 配置名称为untrust-trust的安全策略规则,使Host A访问Host B的报文可通,具体配置步骤如下。
[DeviceB-security-policy-ip] rule name untrust-trust
[DeviceB-security-policy-ip-4-untrust-trust] source-zone untrust
[DeviceB-security-policy-ip-4-untrust-trust] destination-zone trust
[DeviceB-security-policy-ip-4-untrust-trust] source-ip-subnet 10.1.1.0 24
[DeviceB-security-policy-ip-4-untrust-trust] destination-ip-subnet 10.1.2.0 24
[DeviceB-security-policy-ip-4-untrust-trust] action pass
[DeviceB-security-policy-ip-4-untrust-trust] quit
[DeviceB-security-policy-ip] quit
配置IPsec安全提议,协商封装报文使用的各种安全协议
# 创建IPsec安全提议,两端配置的安全提议参数需要完全相同,具体配置步骤如下。
[DeviceB] ipsec transform-set tran1
[DeviceB-ipsec-transform-set-tran1] encapsulation-mode tunnel
[DeviceB-ipsec-transform-set-tran1] protocol esp
[DeviceB-ipsec-transform-set-tran1] esp encryption-algorithm des-cbc
[DeviceB-ipsec-transform-set-tran1] esp authentication-algorithm sha1
[DeviceB-ipsec-transform-set-tran1] quit
配置PKI实体,设置PKI实体的身份信息
[DeviceB] pki entity entity2
[DeviceB-pki-entity-entity2] common-name deviceb
[DeviceB-pki-entity-entity2] quit
配置PKI域,约定PKI证书申请的相关信息
[DeviceB] pki domain domain2
[DeviceB-pki-domain-domain2] public-key rsa general name rsa1
[DeviceB-pki-domain-domain2] undo crl check enable
[DeviceB-pki-domain-domain2] quit
[DeviceB] pki import domain domain2 der ca filename ca.cer
[DeviceB] pki import domain domain2 p12 local filename server.pfx
配置证书访问策略,对用户访问权限进行进一步的控制
[DeviceB] pki certificate access-control-policy policy1
[DeviceB-pki-cert-acp-policy1] rule 1 permit group1
[DeviceB] pki certificate attribute-group group1
[DeviceB-pki-cert-attribute-group-group1] attribute 1 subject-name dn ctn 1
对端证书subject-name DN中需包含(ctn)规则中定义的字符串才被认为是有效的证书。本例使用的证书subject-name DN中包含字符“1”,因此在这里使用参数ctn 1。
配置IKEv2 profile,约定建立IKE SA所需的安全参数
[DeviceB] ikev2 profile profile2
[DeviceB-ikev2-profile-profile2] authentication-method local rsa-signature
[DeviceB-ikev2-profile-profile2] authentication-method remote rsa-signature
[DeviceB-ikev2-profile-profile2] certificate domain domain2
[DeviceB-ikev2-profile-profile2] identity local dn
[DeviceB-ikev2-profile-profile2] match remote certificate policy1
[DeviceB-ikev2-profile-profile2] quit
配置IPsec安全框架,建立IPsec隧道,保护需要防护的数据流
[DeviceB] ipsec profile abc isakmp
[DeviceB-ipsec-profile-isakmp-abc] transform-set tran1
[DeviceB-ipsec-profile-isakmp-abc] ikev2-profile profile2
[DeviceB-ipsec-profile-isakmp-abc] quit
配置IPsec隧道接口,用于对需要保护的流量进行IPsec封装
# 创建IPsec隧道接口,并引用IPsec安全框架。
[DeviceB] interface tunnel 1 mode ipsec
[DeviceB-Tunnel1] ip address 3.3.3.2 255.255.255.0
[DeviceB-Tunnel1] source 2.2.2.2
[DeviceB-Tunnel1] destination 1.1.1.1
[DeviceB-Tunnel1] tunnel protection ipsec profile abc
[DeviceB-Tunnel1] quit
# 将IPsec隧道接口加入Untrust安全域。
[DeviceB] security-zone name untrust
[DeviceB-security-zone-Untrust] import interface tunnel 1
[DeviceB-security-zone-Untrust] quit
# 请根据组网图中规划的信息,配置静态路由,将需要保护的流量引入IPsec隧道接口,本举例的IPsec隧道接口为Tunnel1。
[DeviceB] ip route-static 10.1.1.0 255.255.255.0 tunnel 1
以上配置完成后,Device A会自动与Device B进行IKEv2协商。当IKEv2协商完成后,Device A和Device B上的IPsec 隧道接口都将up,即可以满足上述组网需求,对两个子网之间的数据流进行安全保护。
# 通过display ip interface brief命令可查看接口状态如下:
[DeviceA] display ip interface brief
*down: administratively down
(s): spoofing (l): loopback
Interface Physical Protocol IP address/Mask VPN instance Description
GE1/0/1 up up 1.1.1.1/16 -- --
GE1/0/2 up up 10.1.1.1/24 -- --
Tun1 up up 3.3.3.1/24 -- --
# 通过display interface tunnel命令可查看隧道状态如下:
[DeviceA] display interface Tunnel 1
Tunnel1
Current state: UP
Line protocol state: UP
Description: Tunnel1 Interface
Bandwidth: 64 kbps
Maximum transmission unit: 1444
Internet address: 3.3.3.1/24 (primary)
Tunnel source 1.1.1.1, destination 2.2.2.2
Tunnel TTL 255
Tunnel protocol/transport IPsec/IP
Output queue - Urgent queuing: Size/Length/Discards 0/100/0
Output queue - Protocol queuing: Size/Length/Discards 0/500/0
Output queue - FIFO queuing: Size/Length/Discards 0/75/0
Last clearing of counters: Never
Last 300 seconds input rate: 0 bytes/sec, 0 bits/sec, 0 packets/sec
Last 300 seconds output rate: 0 bytes/sec, 0 bits/sec, 0 packets/sec
Input: 0 packets, 0 bytes, 0 drops
Output: 0 packets, 0 bytes, 0 drops
# 通过display ipsec sa命令查看协商生成的IPsec SA:
[DeviceA] display ipsec sa
-------------------------------
Interface: Tunnel1
-------------------------------
-----------------------------
IPsec profile: abc
Mode: ISAKMP
-----------------------------
Tunnel id: 0
Encapsulation mode: tunnel
Perfect Forward Secrecy:
Transmitting entity: Initiator
Path MTU: 1388
Tunnel:
local address/port: 1.1.1.1/500
remote address/port: 2.2.2.2/500
Flow:
sour addr: 0.0.0.0/0.0.0.0 port: 0 protocol: ip
dest addr: 0.0.0.0/0.0.0.0 port: 0 protocol: ip
[Inbound ESP SAs]
SPI: 2701952073 (0xa10c8449)
Connection ID: 4294967296
Transform set: ESP-ENCRYPT-DES-CBC ESP-AUTH-SHA1
SA duration (kilobytes/sec): 1843200/3600
SA remaining duration (kilobytes/sec): 1843200/3180
Max received sequence-number: 0
Anti-replay check enable: Y
Anti-replay window size: 64
UDP encapsulation used for NAT traversal: N
Status: Active
[Outbound ESP SAs]
SPI: 3607077598 (0xd6ffa2de)
Connection ID: 12884901889
Transform set: ESP-ENCRYPT-DES-CBC ESP-AUTH-SHA1
SA duration (kilobytes/sec): 1843200/3600
SA remaining duration (kilobytes/sec): 1843200/3180
Max sent sequence-number: 0
UDP encapsulation used for NAT traversal: N
Status: Active
# 在Device A上用私网地址可以Ping通Device B连接的私网地址:
[DeviceA] ping -a 10.1.1.2 10.1.2.2
Ping 10.1.2.1 (10.1.2.1) from 10.1.1.1: 56 data bytes, press CTRL_C to break
56 bytes from 10.1.2.1: icmp_seq=0 ttl=255 time=1.000 ms
56 bytes from 10.1.2.1: icmp_seq=1 ttl=255 time=1.000 ms
56 bytes from 10.1.2.1: icmp_seq=2 ttl=255 time=0.000 ms
56 bytes from 10.1.2.1: icmp_seq=3 ttl=255 time=1.000 ms
56 bytes from 10.1.2.1: icmp_seq=4 ttl=255 time=0.000 ms
--- Ping statistics for 10.1.2.1 ---
5 packet(s) transmitted, 5 packet(s) received, 0.0% packet loss
round-trip min/avg/max/std-dev = 0.000/0.600/1.000/0.490 ms
#
interface GigabitEthernet1/0/1
ip address 1.1.1.1 255.255.0.0
#
interface GigabitEthernet1/0/2
ip address 10.1.1.1 255.255.255.0
#
interface Tunnel1 mode ipsec
ip address 3.3.3.1 255.255.255.0
source 1.1.1.1
destination 2.2.2.2
tunnel protection ipsec profile abc
#
security-zone name Trust
import interface GigabitEthernet1/0/2
#
security-zone name Untrust
import interface GigabitEthernet1/0/1
import interface Tunnel1
#
ip route-static 2.2.0.0 16 1.1.1.2
ip route-static 10.1.2.0 24 Tunnel1
#
pki domain domain1
public-key rsa general name rsa1
undo crl check enable
#
pki entity entity1
common-name devicea
#
pki import domain domain1 der ca filename ca.cer
pki import domain domain1 p12 local filename server.pfx
#
pki certificate access-control-policy policy1
rule 1 permit group1
#
pki certificate attribute-group group1
attribute 1 subject-name dn ctn 1
#
ipsec transform-set tran1
encapsulation-mode tunnel
protocol esp
esp encryption-algorithm des-cbc
esp authentication-algorithm sha1
#
ipsec profile abc isakmp
transform-set tran1
ikev2-profile profile1
#
ikev2 profile profile1
authentication-method local rsa-signature
authentication-method remote rsa-signature
identity local dn
match remote certificate policy1
certificate domain domain1
#
security-policy ip
rule 0 name ipseclocalout
action pass
source-zone local
destination-zone untrust
source-ip-host 1.1.1.1
destination-ip-host 2.2.2.2
rule 1 name ipseclocalin
action pass
source-zone untrust
destination-zone local
source-ip-host 2.2.2.2
destination-ip-host 1.1.1.1
rule 2 name trust-untrust
action pass
source-zone trust
destination-zone untrust
source-ip-subnet 10.1.1.0 255.255.255.0
destination-ip-subnet 10.1.2.0 255.255.255.0
rule 3 name untrust-trust
action pass
source-zone untrust
destination-zone trust
source-ip-subnet 10.1.2.0 255.255.255.0
destination-ip-subnet 10.1.1.0 255.255.255.0
#
#
interface GigabitEthernet1/0/1
ip address 2.2.2.2 255.255.0.0
#
interface GigabitEthernet1/0/2
ip address 10.1.2.1 255.255.255.0
#
interface Tunnel1 mode ipsec
ip address 3.3.3.2 255.255.255.0
source 2.2.2.2
destination 1.1.1.1
tunnel protection ipsec profile abc
#
security-zone name Trust
import interface GigabitEthernet1/0/2
#
security-zone name Untrust
import interface GigabitEthernet1/0/1
import interface Tunnel1
#
ip route-static 1.1.0.0 16 2.2.2.1
ip route-static 10.1.1.0 24 Tunnel1
#
pki domain domain2
public-key rsa general name rsa1
undo crl check enable
#
pki entity entity2
common-name deviceb
#
pki import domain domain2 der ca filename ca.cer
pki import domain domain2 p12 local filename server.pfx
#
pki certificate access-control-policy policy1
rule 1 permit group1
#
pki certificate attribute-group group1
attribute 1 subject-name dn ctn 1
#
ipsec transform-set tran1
encapsulation-mode tunnel
protocol esp
esp encryption-algorithm des-cbc
esp authentication-algorithm sha1
#
ipsec profile abc isakmp
transform-set tran1
ikev2-profile profile2
#
ikev2 profile profile2
authentication-method local rsa-signature
authentication-method remote rsa-signature
identity local dn
match remote certificate policy1
certificate domain domain2
#
security-policy ip
rule 0 name ipseclocalout
action pass
source-zone local
destination-zone untrust
source-ip-host 2.2.2.2
destination-ip-host 1.1.1.1
rule 1 name ipseclocalin
action pass
source-zone untrust
destination-zone local
source-ip-host 1.1.1.1
destination-ip-host 2.2.2.2
rule 2 name trust-untrust
action pass
source-zone trust
destination-zone untrust
source-ip-subnet 10.1.2.0 255.255.255.0
destination-ip-subnet 10.1.1.0 255.255.255.0
rule 3 name untrust-trust
action pass
source-zone untrust
destination-zone trust
source-ip-subnet 10.1.1.0 255.255.255.0
destination-ip-subnet 10.1.2.0 255.255.255.0