本举例是在M9000-AI-E8的R9071版本上进行配置和验证的。
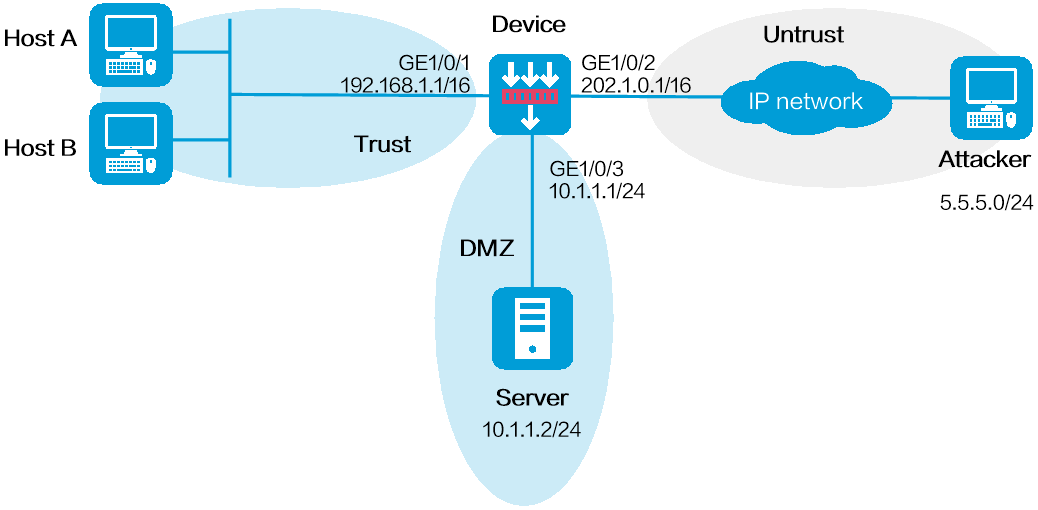
如下图所示,网络管理员通过流量分析发现外部网络中存在来自网段5.5.5.0/24的一组攻击者,需要将这组攻击者的报文在Device上永远过滤掉。
图-1 地址对象组黑名单配置组网图
配置接口IP地址
# 根据组网图中规划的信息,配置各接口的IP地址,具体配置步骤如下。
<Device> system-view
[Device] interface gigabitethernet 1/0/1
[Device-GigabitEthernet1/0/1] ip address 192.168.1.1 255.255.0.0
[Device-GigabitEthernet1/0/1] quit
请参考以上步骤配置其他接口的IP地址,具体配置步骤略。
将接口加入安全域
# 请根据组网图中规划的信息,将接口加入对应的安全域,具体配置步骤如下。
[Device] security-zone name trust
[Device-security-zone-Trust] import interface gigabitethernet 1/0/1
[Device-security-zone-Trust] quit
[Device] security-zone name untrust
[Device-security-zone-Untrust] import interface gigabitethernet 1/0/2
[Device-security-zone-Untrust] quit
[Device] security-zone name dmz
[Device-security-zone-DMZ] import interface gigabitethernet 1/0/3
[Device-security-zone-DMZ] quit
配置安全策略
# 配置名称为trust-untrust的安全策略,保证Trust安全域内的主机可以访问Internet,具体配置步骤如下。
[Device] security-policy ip
[Device-security-policy-ip] rule name trust-untrust
[Device-security-policy-ip-1-trust-untrust] source-zone trust
[Device-security-policy-ip-1-trust-untrust] destination-zone untrust
[Device-security-policy-ip-1-trust-untrust] source-ip-subnet 192.168.0.0 16
[Device-security-policy-ip-1-trust-untrust] action pass
[Device-security-policy-ip-1-trust-untrust] quit
# 配置名称为untrust-dmz的安全策略,保证Internet中的主机可以访问Server,具体配置步骤如下。
[Device-security-policy-ip] rule name untrust-dmz
[Device-security-policy-ip-2-untrust-dmz] source-zone untrust
[Device-security-policy-ip-2-untrust-dmz] destination-zone dmz
[Device-security-policy-ip-2-untrust-dmz] destination-ip-host 10.1.1.2
[Device-security-policy-ip-2-untrust-dmz] action pass
[Device-security-policy-ip-2-untrust-dmz] quit
[Device-security-policy-ip] quit
配置地址对象组黑名单功能
# 创建地址对象组obj1,并将5.5.5.0/24加入地址对象组。
[Device] object-group ip address obj1
[Device-obj-grp-ip-obj1] network subnet 5.5.5.0 24
[Device-obj-grp-ip-obj1] quit
# 通过引用地址对象组obj1配置黑名单。
[Device] blacklist object-group obj1
# 开启全局黑名单过滤功能。
[Device] blacklist global enable
完成以上配置后,Device对来自网段5.5.5.0/24的攻击者的报文一律进行丢弃处理,除非管理员认为网段5.5.5.0/24不再是攻击者,通过undo blacklist object-group将其从黑名单中删除。
#
object-group ip address obj1
0 network subnet 5.5.5.0 255.255.255.0
#
interface GigabitEthernet1/0/1
port link-mode route
ip address 192.168.1.1 255.255.0.0
#
interface GigabitEthernet1/0/2
port link-mode route
ip address 202.1.0.1 255.255.0.0
#
interface GigabitEthernet1/0/3
port link-mode route
ip address 10.1.1.1 255.255.255.0
#
security-zone name Trust
import interface GigabitEthernet1/0/1
#
security-zone name DMZ
import interface GigabitEthernet1/0/3
#
security-zone name Untrust
import interface GigabitEthernet1/0/2
#
blacklist global enable
blacklist object-group obj1
#
security-policy ip
rule 1 name trust-untrust
action pass
source-zone trust
destination-zone untrust
source-ip-subnet 192.168.0.0 255.255.0.0
rule 2 name untrust-dmz
action pass
source-zone untrust
destination-zone dmz
destination-ip-host 10.1.1.2