本举例是在M9000-AI-E8的R9071版本上进行配置和验证的。
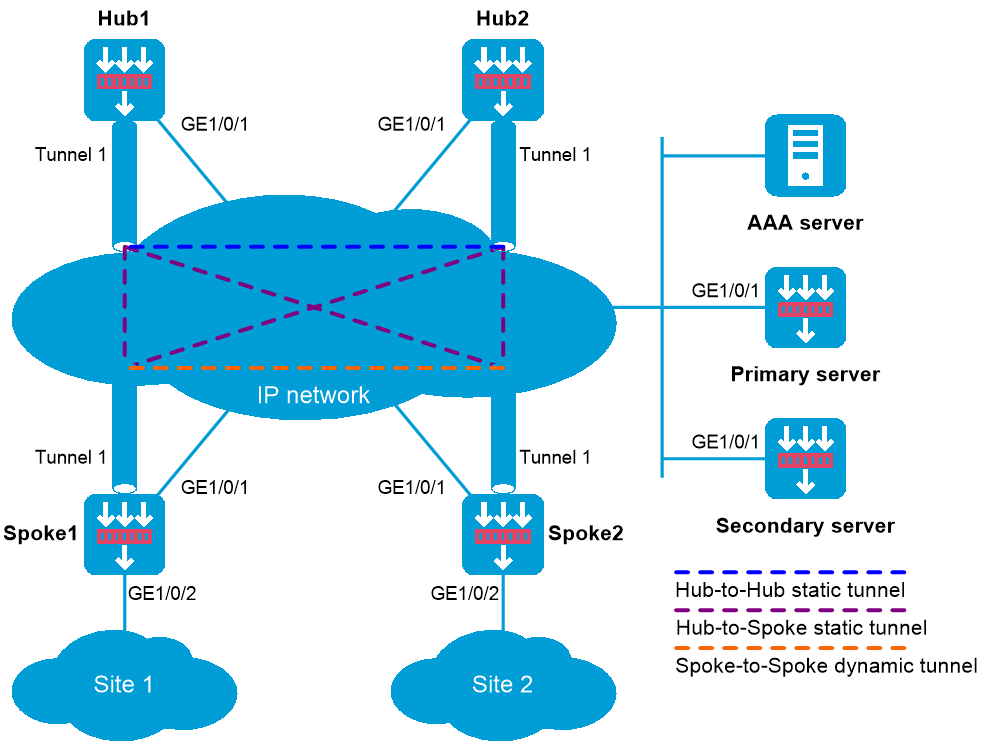
如下图所示:
在IPv6 Hub-Spoke的组网方式下,数据通过Hub-Spoke隧道进行转发。主、备VAM Server负责管理、维护各个节点的信息;AAA服务器负责对VAM Client进行认证和计费管理;两个Hub互为备份,负责数据的转发和路由信息的交换。
Spoke与Hub之间建立永久的ADVPN隧道。
图-1 IPv6 Hub-Spoke类型ADVPN组网图
|
设备 |
接口 |
IP地址 |
设备 |
接口 |
IP地址 |
|
Hub 1 |
GE1/0/1 |
1::1/64 |
Spoke 1 |
GE1/0/1 |
1::3/64 |
|
|
Tunnel1 |
192:168::1/64 |
|
GE1/0/2 |
192:168:1::1/64 |
|
Hub 2 |
GE1/0/1 |
1::2/64 |
|
Tunnel1 |
192:168::3/64 |
|
|
Tunnel1 |
192:168::2/64 |
Spoke 2 |
GE1/0/1 |
1::4/64 |
|
AAA server |
|
1::10/64 |
|
GE1/0/2 |
192:168:2::1/64 |
|
Primary server |
GE1/0/1 |
1::11/64 |
|
Tunnel1 |
192:168::4/64 |
|
Secondary server |
GE1/0/1 |
1::12/64 |
|
|
|
配置接口IP地址
# 根据组网图中规划的信息,配置各接口的IP地址,具体配置步骤如下。
<PrimaryServer> system-view
[PrimaryServer] interface gigabitethernet 1/0/1
[PrimaryServer-GigabitEthernet1/0/1] ipv6 address 1::11/64
[PrimaryServer-GigabitEthernet1/0/1] quit
配置接口加入安全域。
# 请根据组网图中规划的信息,将接口加入对应的安全域,具体配置步骤如下。
[PrimaryServer] security-zone name untrust
[PrimaryServer-security-zone-Untrust] import interface gigabitethernet 1/0/1
[PrimaryServer-security-zone-Untrust] quit
配置安全策略
# 配置名称为advpnlocalout的安全策规则,使VAM Server可以向VAM Clinet发送VAM协议报文,具体配置步骤如下。
[PrimaryServer] security-policy ipv6
[PrimaryServer-security-policy-ipv6] rule name advpnlocalout
[PrimaryServer-security-policy-ipv6-1-advpnlocalout] source-zone local
[PrimaryServer-security-policy-ipv6-1-advpnlocalout] destination-zone untrust
[PrimaryServer-security-policy-ipv6-1-advpnlocalout] source-ip-host 1::11
[PrimaryServer-security-policy-ipv6-1-advpnlocalout] destination-ip-range 1::1 1::12
[PrimaryServer-security-policy-ipv6-1-advpnlocalout] action pass
[PrimaryServer-security-policy-ipv6-1-advpnlocalout] quit
# 配置名称为advpnlocalin的安全策略规则,使VAM Server可以接收和处理来自VAM Clinet的VAM协议报文,具体配置步骤如下。
[PrimaryServer-security-policy-ipv6] rule name advpnlocalin
[PrimaryServer-security-policy-ipv6-2-advpnlocalin] source-zone untrust
[PrimaryServer-security-policy-ipv6-2-advpnlocalin] destination-zone local
[PrimaryServer-security-policy-ipv6-2-advpnlocalin] source-ip-range 1::1 1::12
[PrimaryServer-security-policy-ipv6-2-advpnlocalin] destination-ip-host 1::11
[PrimaryServer-security-policy-ipv6-2-advpnlocalin] action pass
[PrimaryServer-security-policy-ipv6-2-advpnlocalin] quit
[PrimaryServer-security-policy-ipv6] quit
配置AAA认证
# 配置RADIUS方案。
<PrimaryServer> system-view
[PrimaryServer] radius scheme abc
[PrimaryServer-radius-abc] primary authentication ipv6 1::10 1812
[PrimaryServer-radius-abc] primary accounting ipv6 1::10 1813
[PrimaryServer-radius-abc] key authentication simple 123
[PrimaryServer-radius-abc] key accounting simple 123
[PrimaryServer-radius-abc] user-name-format without-domain
[PrimaryServer-radius-abc] quit
[PrimaryServer] radius session-control enable
# 配置ISP域的AAA方案。
[PrimaryServer] domain abc
[PrimaryServer-isp-abc] authentication advpn radius-scheme abc
[PrimaryServer-isp-abc] accounting advpn radius-scheme abc
[PrimaryServer-isp-abc] quit
[PrimaryServer] domain default enable abc
配置VAM Server,用于管理和维护VAM Client地址信息
[PrimaryServer] vam server advpn-domain abc id 1
[PrimaryServer-vam-server-domain-abc] hub-group 0
[PrimaryServer-vam-server-domain-abc-hub-group-0] hub ipv6 private-address 192:168::1
[PrimaryServer-vam-server-domain-abc-hub-group-0] hub ipv6 private-address 192:168::2
[PrimaryServer-vam-server-domain-abc-hub-group-0] spoke ipv6 private-address network 192:168::0 64
[PrimaryServer-vam-server-domain-abc-hub-group-0] quit
[PrimaryServer-vam-server-domain-abc] pre-shared-key simple 123456
[PrimaryServer-vam-server-domain-abc] authentication-method chap
[PrimaryServer-vam-server-domain-abc] server enable
[PrimaryServer-vam-server-domain-abc] quit
除IP地址外,备VAM Server的ADVPN配置与主VAM Server相同,不再赘述。
配置接口IP地址
# 根据组网图中规划的信息,配置各接口的IP地址,具体配置步骤如下。
<Hub1> system-view
[Hub1] interface gigabitethernet 1/0/1
[Hub1-GigabitEthernet1/0/1] ipv6 address 1::1 64
[Hub1-GigabitEthernet1/0/1] quit
[Hub1] interface tunnel 1 mode advpn gre ipv6
[Hub1-Tunnel1] ipv6 address 192:168::1 64
[Hub1-Tunnel1] ipv6 address fe80::1 link-local
配置接口加入安全域。
# 请根据组网图中规划的信息,将接口加入对应的安全域,具体配置步骤如下。
[Hub1] security-zone name untrust
[Hub1-security-zone-Untrust] import interface gigabitethernet 1/0/1
[Hub1-security-zone-Untrust] import interface tunnel 1
[Hub1-security-zone-Untrust] quit
配置安全策略
# 配置名称为advpnlocalout的安全策规则,使Hub1可以向VAM Server发送VAM协议报文,具体配置步骤如下。
[Hub1] security-policy ipv6
[Hub1-security-policy-ipv6] rule name advpnlocalout
[Hub1-security-policy-ipv6-1-advpnlocalout] source-zone local
[Hub1-security-policy-ipv6-1-advpnlocalout] destination-zone untrust
[Hub1-security-policy-ipv6-1-advpnlocalout] source-ip-host 1::1
[Hub1-security-policy-ipv6-1-advpnlocalout] destination-ip-range 1::10 1::12
[Hub1-security-policy-ipv6-1-ipseclocalout] action pass
[Hub1-security-policy-ipv6-1-ipseclocalout] quit
# 配置名称为advpnlocalin的安全策略规则,使Hub1可以接收和处理来自VAM Server的VAM协议报文,具体配置步骤如下。
[Hub1-security-policy-ipv6] rule name advpnlocalin
[Hub1-security-policy-ipv6-2-advpnlocalin] source-zone untrust
[Hub1-security-policy-ipv6-2-advpnlocalin] destination-zone local
[Hub1-security-policy-ipv6-2-advpnlocalin] source-ip-range 1::10 1::12
[Hub1-security-policy-ipv6-2-advpnlocalin] destination-ip-host 1::1
[Hub1-security-policy-ipv6-2-advpnlocalin] action pass
[Hub1-security-policy-ipv6-2-advpnlocalin] quit
# 配置名称为ipseclocalout的安全策规则,使Hub1可以向其他VAM Client发送IPsec协商报文,具体配置步骤如下。
[Hub1-security-policy-ipv6] rule name ipseclocalout
[Hub1-security-policy-ipv6-3-ipseclocalout] source-zone local
[Hub1-security-policy-ipv6-3-ipseclocalout] destination-zone untrust
[Hub1-security-policy-ipv6-3-ipseclocalout] source-ip-host 1::1
[Hub1-security-policy-ipv6-3-ipseclocalout] destination-ip-range 1::2 1::4
[Hub1-security-policy-ipv6-3-ipseclocalout] action pass
[Hub1-security-policy-ipv6-3-ipseclocalout] quit
# 配置名称为ipseclocalin的安全策略规则,使Hub1可以接收和处理来自其他VAM Clinet的IPsec协商报文,具体配置步骤如下。
[Hub1-security-policy-ipv6] rule name ipseclocalin
[Hub1-security-policy-ipv6-4-ipseclocalin] source-zone untrust
[Hub1-security-policy-ipv6-4-ipseclocalin] destination-zone local
[Hub1-security-policy-ipv6-4-ipseclocalin] source-ip-range 1::2 1::4
[Hub1-security-policy-ipv6-4-ipseclocalin] destination-ip-host 1::1
[Hub1-security-policy-ipv6-4-ipseclocalin] action pass
[Hub1-security-policy-ipv6-4-ipseclocalin] quit
# 配置名称为ospflocalout的安全策规则,使Hub1可以向其他VAM Client发送OSPF报文,具体配置步骤如下。
[Hub1-security-policy-ipv6] rule name ospflocalout
[Hub1-security-policy-ipv6-5-ospflocalout] source-zone local
[Hub1-security-policy-ipv6-5-ospflocalout] destination-zone untrust
[Hub1-security-policy-ipv6-5-ospflocalout] service ospf
[Hub1-security-policy-ipv6-5-ospflocalout] action pass
[Hub1-security-policy-ipv6-5-ospflocalout] quit
# 配置名称为ospflocalin的安全策略规则,使Hub1可以接收和处理来自其他VAM Clinet的OSPF报文,具体配置步骤如下。
[Hub1-security-policy-ipv6] rule name ospflocalin
[Hub1-security-policy-ipv6-6-ospflocalin] source-zone untrust
[Hub1-security-policy-ipv6-6-ospflocalin] destination-zone local
[Hub1-security-policy-ipv6-6-ospflocalin] service ospf
[Hub1-security-policy-ipv6-6-ospflocalin] action pass
[Hub1-security-policy-ipv6-6-ospflocalin] quit
配置VAM Client,用于建立ADVPN网络
[Hub1] vam client name Hub1
[Hub1-vam-client-Hub1] advpn-domain abc
[Hub1-vam-client-Hub1] pre-shared-key simple 123456
[Hub1-vam-client-Hub1] user hub1 password simple hub1
[Hub1-vam-client-Hub1] server primary ipv6-address 1::11
[Hub1-vam-client-Hub1] server secondary ipv6-address 1::12
[Hub1-vam-client-Hub1] client enable
[Hub1-vam-client-Hub1] quit
配置IPsec安全框架
# 配置IKE框架。
[Hub1] ike keychain abc
[Hub1-ike-keychain-abc] pre-shared-key address ipv6 :: 0 key simple 123456
[Hub1-ike-keychain-abc] quit
[Hub1] ike profile abc
[Hub1-ike-profile-abc] keychain abc
[Hub1-ike-profile-abc] quit
# 配置IPsec安全框架。
[Hub1] ipsec transform-set abc
[Hub1-ipsec-transform-set-abc] encapsulation-mode transport
[Hub1-ipsec-transform-set-abc] esp encryption-algorithm des-cbc
[Hub1-ipsec-transform-set-abc] esp authentication-algorithm sha1
[Hub1-ipsec-transform-set-abc] quit
[Hub1] ipsec profile abc isakmp
[Hub1-ipsec-profile-isakmp-abc] transform-set abc
[Hub1-ipsec-profile-isakmp-abc] ike-profile abc
[Hub1-ipsec-profile-isakmp-abc] quit
配置OSPFv3路由
# 启动OSPFv3,以发布私网的路由信息。
[Hub1] ospfv3 1
[Hub1-ospfv3-1] router-id 0.0.0.1
[Hub1-ospfv3-1] area 0
[Hub1-ospfv3-1-area-0.0.0.0] quit
[Hub1-ospfv3-1] quit
配置ADVPN隧道
# 配置GRE封装的IPv6 ADVPN隧道接口Tunnel1。
[Hub1] interface tunnel 1
[Hub1-Tunnel1] vam ipv6 client Hub1
[Hub1-Tunnel1] ospfv3 1 area 0
[Hub1-Tunnel1] ospfv3 network-type p2mp
[Hub1-Tunnel1] source gigabitethernet 1/0/1
[Hub1-Tunnel1] tunnel protection ipsec profile abc
[Hub1-Tunnel1] quit
配置接口IP地址
# 根据组网图中规划的信息,配置各接口的IP地址,具体配置步骤如下。
<Hub2> system-view
[Hub2] interface gigabitethernet 1/0/1
[Hub2-GigabitEthernet1/0/1] ipv6 address 1::2 64
[Hub2-GigabitEthernet1/0/1] quit
[Hub2] interface tunnel 1 mode advpn gre ipv6
[Hub2-Tunnel1] ipv6 address 192:168::2 64
[Hub2-Tunnel1] ipv6 address fe80::2 link-local
配置接口加入安全域。
# 请根据组网图中规划的信息,将接口加入对应的安全域,具体配置步骤如下。
[Hub2] security-zone name untrust
[Hub2-security-zone-Untrust] import interface gigabitethernet 1/0/1
[Hub2-security-zone-Untrust] import interface tunnel 1
[Hub2-security-zone-Untrust] quit
配置安全策略
# 配置名称为advpnlocalout的安全策规则,使Hub2可以向VAM Server发送VAM协议报文,具体配置步骤如下。
[Hub2] security-policy ipv6
[Hub2-security-policy-ipv6] rule name advpnlocalout
[Hub2-security-policy-ipv6-1-advpnlocalout] source-zone local
[Hub2-security-policy-ipv6-1-advpnlocalout] destination-zone untrust
[Hub2-security-policy-ipv6-1-advpnlocalout] source-ip-host 1::2
[Hub2-security-policy-ipv6-1-advpnlocalout] destination-ip-range 1::10 1::12
[Hub2-security-policy-ipv6-1-ipseclocalout] action pass
[Hub2-security-policy-ipv6-1-ipseclocalout] quit
# 配置名称为advpnlocalin的安全策略规则,使Hub2可以接收和处理来自VAM Server的VAM协议报文,具体配置步骤如下。
[Hub2-security-policy-ipv6] rule name advpnlocalin
[Hub2-security-policy-ipv6-2-advpnlocalin] source-zone untrust
[Hub2-security-policy-ipv6-2-advpnlocalin] destination-zone local
[Hub2-security-policy-ipv6-2-advpnlocalin] source-ip-range 1::10 1::12
[Hub2-security-policy-ipv6-2-advpnlocalin] destination-ip-host 1::2
[Hub2-security-policy-ipv6-2-advpnlocalin] action pass
[Hub2-security-policy-ipv6-2-advpnlocalin] quit
# 配置名称为ipseclocalout的安全策规则,使Hub2可以向其他VAM Client发送IPsec协商报文,具体配置步骤如下。
[Hub2-security-policy-ipv6] rule name ipseclocalout
[Hub2-security-policy-ipv6-3-ipseclocalout] source-zone local
[Hub2-security-policy-ipv6-3-ipseclocalout] destination-zone untrust
[Hub2-security-policy-ipv6-3-ipseclocalout] source-ip-host 1::2
[Hub2-security-policy-ipv6-3-ipseclocalout] destination-ip-range 1::1 1::4
[Hub2-security-policy-ipv6-3-ipseclocalout] action pass
[Hub2-security-policy-ipv6-3-ipseclocalout] quit
# 配置名称为ipseclocalin的安全策略规则,使Hub2可以接收和处理来自其他VAM Clinet的IPsec协商报文,具体配置步骤如下。
[Hub2-security-policy-ipv6] rule name ipseclocalin
[Hub2-security-policy-ipv6-4-ipseclocalin] source-zone untrust
[Hub2-security-policy-ipv6-4-ipseclocalin] destination-zone local
[Hub2-security-policy-ipv6-4-ipseclocalin] source-ip-range 1::1 1::4
[Hub2-security-policy-ipv6-4-ipseclocalin] destination-ip-host 1::2
[Hub2-security-policy-ipv6-4-ipseclocalin] action pass
[Hub2-security-policy-ipv6-4-ipseclocalin] quit
# 配置名称为ospflocalout的安全策规则,使Hub2可以向其他VAM Client发送OSPF报文,具体配置步骤如下。
[Hub2-security-policy-ipv6] rule name ospflocalout
[Hub2-security-policy-ipv6-5-ospflocalout] source-zone local
[Hub2-security-policy-ipv6-5-ospflocalout] destination-zone untrust
[Hub2-security-policy-ipv6-5-ospflocalout] service ospf
[Hub2-security-policy-ipv6-5-ospflocalout] action pass
[Hub2-security-policy-ipv6-5-ospflocalout] quit
# 配置名称为ospflocalin的安全策略规则,使Hub2可以接收和处理来自其他VAM Clinet的OSPF报文,具体配置步骤如下。
[Hub2-security-policy-ipv6] rule name ospflocalin
[Hub2-security-policy-ipv6-6-ospflocalin] source-zone untrust
[Hub2-security-policy-ipv6-6-ospflocalin] destination-zone local
[Hub2-security-policy-ipv6-6-ospflocalin] service ospf
[Hub2-security-policy-ipv6-6-ospflocalin] action pass
[Hub2-security-policy-ipv6-6-ospflocalin] quit
[Hub2-security-policy-ipv6] quit
配置VAM Client,用于建立ADVPN网络
[Hub2] vam client name Hub2
[Hub2-vam-client-Hub2] advpn-domain abc
[Hub2-vam-client-Hub2] pre-shared-key simple 123456
[Hub2-vam-client-Hub2] user hub2 password simple hub2
[Hub2-vam-client-Hub2] server primary ipv6-address 1::11
[Hub2-vam-client-Hub2] server secondary ipv6-address 1::12
[Hub2-vam-client-Hub2] client enable
[Hub2-vam-client-Hub2] quit
配置IPsec安全框架
# 配置IKE框架。
[Hub2] ike keychain abc
[Hub2-ike-keychain-abc] pre-shared-key address ipv6 :: 0 key simple 123456
[Hub2-ike-keychain-abc] quit
[Hub2] ike profile abc
[Hub2-ike-profile-abc] keychain abc
[Hub2-ike-profile-abc] quit
# 配置IPsec安全框架。
[Hub2] ipsec transform-set abc
[Hub2-ipsec-transform-set-abc] encapsulation-mode transport
[Hub2-ipsec-transform-set-abc] esp encryption-algorithm des-cbc
[Hub2-ipsec-transform-set-abc] esp authentication-algorithm sha1
[Hub2-ipsec-transform-set-abc] quit
[Hub2] ipsec profile abc isakmp
[Hub2-ipsec-profile-isakmp-abc] transform-set abc
[Hub2-ipsec-profile-isakmp-abc] ike-profile abc
[Hub2-ipsec-profile-isakmp-abc] quit
配置OSPFv3路由
# 启动OSPFv3,以发布私网的路由信息。
[Hub2] ospfv3 1
[Hub2-ospfv3-1] router-id 0.0.0.2
[Hub2-ospfv3-1] area 0
[Hub2-ospfv3-1-area-0.0.0.0] quit
[Hub2-ospfv3-1] quit
配置ADVPN隧道
# 配置GRE封装的IPv6 ADVPN隧道接口Tunnel1。
[Hub2] interface tunnel 1
[Hub2-Tunnel1] vam ipv6 client Hub2
[Hub2-Tunnel1] ospfv3 1 area 0
[Hub2-Tunnel1] ospfv3 network-type p2mp
[Hub2-Tunnel1] source gigabitethernet 1/0/1
[Hub2-Tunnel1] tunnel protection ipsec profile abc
[Hub2-Tunnel1] quit
配置接口IP地址
# 根据组网图中规划的信息,配置各接口的IP地址,具体配置步骤如下。
<Spoke1> system-view
[Spoke1] interface gigabitethernet 1/0/1
[Spoke1-GigabitEthernet1/0/1] ipv6 address 1::3 64
[Spoke1-GigabitEthernet1/0/1] quit
[Spoke1] interface tunnel 1 mode advpn gre ipv6
[Spoke1-Tunnel1] ipv6 address 192:168::3 64
[Spoke1-Tunnel1] ipv6 address fe80::3 link-local
请参考以上步骤配置其他接口的IP地址,具体配置步骤略。
配置接口加入安全域。
# 请根据组网图中规划的信息,将接口加入对应的安全域,具体配置步骤如下。
[Spoke1] security-zone name untrust
[Spoke1-security-zone-Untrust] import interface gigabitethernet 1/0/1
[Spoke1-security-zone-Untrust] import interface tunnel 1
[Spoke1-security-zone-Untrust] quit
[Spoke1] security-zone name trust
[Spoke1-security-zone-Trust] import interface gigabitethernet 1/0/2
[Spoke1-security-zone-Trust] quit
配置安全策略
# 配置名称为advpnlocalout的安全策规则,使Spoke1可以向VAM Server发送VAM协议报文,具体配置步骤如下。
[Spoke1] security-policy ipv6
[Spoke1-security-policy-ipv6] rule name advpnlocalout
[Spoke1-security-policy-ipv6-1-advpnlocalout] source-zone local
[Spoke1-security-policy-ipv6-1-advpnlocalout] destination-zone untrust
[Spoke1-security-policy-ipv6-1-advpnlocalout] source-ip-host 1::3
[Spoke1-security-policy-ipv6-1-advpnlocalout] destination-ip-range 1::10 1::12
[Spoke1-security-policy-ipv6-1-ipseclocalout] action pass
[Spoke1-security-policy-ipv6-1-ipseclocalout] quit
# 配置名称为advpnlocalin的安全策略规则,使Spoke1可以接收和处理来自VAM Server的VAM协议报文,具体配置步骤如下。
[Spoke1-security-policy-ipv6] rule name advpnlocalin
[Spoke1-security-policy-ipv6-2-advpnlocalin] source-zone untrust
[Spoke1-security-policy-ipv6-2-advpnlocalin] destination-zone local
[Spoke1-security-policy-ipv6-2-advpnlocalin] source-ip-range 1::10 1::12
[Spoke1-security-policy-ipv6-2-advpnlocalin] destination-ip-host 1::3
[Spoke1-security-policy-ipv6-2-advpnlocalin] action pass
[Spoke1-security-policy-ipv6-2-advpnlocalin] quit
# 配置名称为ipseclocalout的安全策规则,使Spoke1可以向其他VAM Client发送IPsec协商报文,具体配置步骤如下。
[Spoke1-security-policy-ipv6] rule name ipseclocalout
[Spoke1-security-policy-ipv6-3-ipseclocalout] source-zone local
[Spoke1-security-policy-ipv6-3-ipseclocalout] destination-zone untrust
[Spoke1-security-policy-ipv6-3-ipseclocalout] source-ip-host 1::3
[Spoke1-security-policy-ipv6-3-ipseclocalout] destination-ip-range 1::1 1::4
[Spoke1-security-policy-ipv6-3-ipseclocalout] action pass
[Spoke1-security-policy-ipv6-3-ipseclocalout] quit
# 配置名称为ipseclocalin的安全策略规则,使Spoke1可以接收和处理来自其他VAM Clinet的IPsec协商报文,具体配置步骤如下。
[Spoke1-security-policy-ipv6] rule name ipseclocalin
[Spoke1-security-policy-ipv6-4-ipseclocalin] source-zone untrust
[Spoke1-security-policy-ipv6-4-ipseclocalin] destination-zone local
[Spoke1-security-policy-ipv6-4-ipseclocalin] source-ip-range 1::1 1::4
[Spoke1-security-policy-ipv6-4-ipseclocalin] destination-ip-host 1::3
[Spoke1-security-policy-ipv6-4-ipseclocalin] action pass
[Spoke1-security-policy-ipv6-4-ipseclocalin] quit
# 配置名称为ospflocalout的安全策规则,使Spoke1可以向其他VAM Client发送OSPF报文,具体配置步骤如下。
[Spoke1-security-policy-ipv6] rule name ospflocalout
[Spoke1-security-policy-ipv6-5-ospflocalout] source-zone local
[Spoke1-security-policy-ipv6-5-ospflocalout] destination-zone untrust
[Spoke1-security-policy-ipv6-5-ospflocalout] service ospf
[Spoke1-security-policy-ipv6-5-ospflocalout] action pass
[Spoke1-security-policy-ipv6-5-ospflocalout] quit
# 配置名称为ospflocalin的安全策略规则,使Spoke1可以接收和处理来自其他VAM Clinet的OSPF报文,具体配置步骤如下。
[Spoke1-security-policy-ipv6] rule name ospflocalin
[Spoke1-security-policy-ipv6-6-ospflocalin] source-zone untrust
[Spoke1-security-policy-ipv6-6-ospflocalin] destination-zone local
[Spoke1-security-policy-ipv6-6-ospflocalin] service ospf
[Spoke1-security-policy-ipv6-6-ospflocalin] action pass
[Spoke1-security-policy-ipv6-6-ospflocalin] quit
[Spoke1-security-policy-ipv6] quit
配置VAM Client,用于建立ADVPN网络
[Spoke1] vam client name Spoke1
[Spoke1-vam-client-Spoke1] advpn-domain abc
[Spoke1-vam-client-Spoke1] pre-shared-key simple 123456
[Spoke1-vam-client-Spoke1] user spoke1 password simple spoke1
[Spoke1-vam-client-Spoke1] server primary ipv6-address 1::11
[Spoke1-vam-client-Spoke1] server secondary ipv6-address 1::12
[Spoke1-vam-client-Spoke1] client enable
[Spoke1-vam-client-Spoke1] quit
配置IPsec安全框架
# 配置IKE框架。
[Spoke1] ike keychain abc
[Spoke1-ike-keychain-abc] pre-shared-key address ipv6 :: 0 key simple 123456
[Spoke1-ike-keychain-abc] quit
[Spoke1] ike profile abc
[Spoke1-ike-profile-abc] keychain abc
[Spoke1-ike-profile-abc] quit
# 配置IPsec安全框架。
[Spoke1] ipsec transform-set abc
[Spoke1-ipsec-transform-set-abc] encapsulation-mode transport
[Spoke1-ipsec-transform-set-abc] esp encryption-algorithm des-cbc
[Spoke1-ipsec-transform-set-abc] esp authentication-algorithm sha1
[Spoke1-ipsec-transform-set-abc] quit
[Spoke1] ipsec profile abc isakmp
[Spoke1-ipsec-profile-isakmp-abc] transform-set abc
[Spoke1-ipsec-profile-isakmp-abc] ike-profile abc
[Spoke1-ipsec-profile-isakmp-abc] quit
配置OSPFv3路由
# 启动OSPFv3,以发布私网的路由信息。
[Spoke1] ospfv3 1
[Spoke1-ospfv3-1] router-id 0.0.0.3
[Spoke1-ospfv3-1] area 0
[Spoke1-ospfv3-1-area-0.0.0.0] quit
[Spoke1-ospfv3-1] quit
配置ADVPN隧道
# 配置GRE封装的IPv6 ADVPN隧道接口Tunnel1。
[Spoke1] interface tunnel 1
[Spoke1-Tunnel1] vam ipv6 client Spoke1
[Spoke1-Tunnel1] ospfv3 1 area 0
[Spoke1-Tunnel1] ospfv3 network-type p2mp
[Spoke1-Tunnel1] source gigabitethernet 1/0/1
[Spoke1-Tunnel1] tunnel protection ipsec profile abc
[Spoke1-Tunnel1] quit
配置接口IP地址
# 根据组网图中规划的信息,配置各接口的IP地址,具体配置步骤如下。
<Spoke2> system-view
[Spoke2] interface gigabitethernet 1/0/1
[Spoke2-GigabitEthernet1/0/1] ipv6 address 1::4 64
[Spoke2-GigabitEthernet1/0/1] quit
[Spoke2] interface tunnel 1 mode advpn gre ipv6
[Spoke2-Tunnel1] ipv6 address 192:168::4 64
[Spoke2-Tunnel1] ipv6 address fe80::4 link-local
请参考以上步骤配置其他接口的IP地址,具体配置步骤略。
配置接口加入安全域。
# 请根据组网图中规划的信息,将接口加入对应的安全域,具体配置步骤如下。
[Spoke2] security-zone name untrust
[Spoke2-security-zone-Untrust] import interface gigabitethernet 1/0/1
[Spoke2-security-zone-Untrust] import interface tunnel 1
[Spoke2-security-zone-Untrust] quit
[Spoke2] security-zone name trust
[Spoke2-security-zone-Trust] import interface gigabitethernet 1/0/2
[Spoke2-security-zone-Trust] quit
配置安全策略
# 配置名称为advpnlocalout的安全策规则,使Spoke2可以向VAM Server发送VAM协议报文,具体配置步骤如下。
[Spoke2] security-policy ipv6
[Spoke2-security-policy-ipv6] rule name advpnlocalout
[Spoke2-security-policy-ipv6-1-advpnlocalout] source-zone local
[Spoke2-security-policy-ipv6-1-advpnlocalout] destination-zone untrust
[Spoke2-security-policy-ipv6-1-advpnlocalout] source-ip-host 1::4
[Spoke2-security-policy-ipv6-1-advpnlocalout] destination-ip-range 1::10 1::12
[Spoke2-security-policy-ipv6-1-ipseclocalout] action pass
[Spoke2-security-policy-ipv6-1-ipseclocalout] quit
# 配置名称为advpnlocalin的安全策略规则,使Spoke2可以接收和处理来自VAM Server的VAM协议报文,具体配置步骤如下。
[Spoke2-security-policy-ipv6] rule name advpnlocalin
[Spoke2-security-policy-ipv6-2-advpnlocalin] source-zone untrust
[Spoke2-security-policy-ipv6-2-advpnlocalin] destination-zone local
[Spoke2-security-policy-ipv6-2-advpnlocalin] source-ip-range 1::10 1::12
[Spoke2-security-policy-ipv6-2-advpnlocalin] destination-ip-host 1::4
[Spoke2-security-policy-ipv6-2-advpnlocalin] action pass
[Spoke2-security-policy-ipv6-2-advpnlocalin] quit
# 配置名称为ipseclocalout的安全策规则,使Spoke2可以向其他VAM Client发送IPsec协商报文,具体配置步骤如下。
[Spoke2-security-policy-ipv6] rule name ipseclocalout
[Spoke2-security-policy-ipv6-3-ipseclocalout] source-zone local
[Spoke2-security-policy-ipv6-3-ipseclocalout] destination-zone untrust
[Spoke2-security-policy-ipv6-3-ipseclocalout] source-ip-host 1::4
[Spoke2-security-policy-ipv6-3-ipseclocalout] destination-ip-range 1::1 1::3
[Spoke2-security-policy-ipv6-3-ipseclocalout] action pass
[Spoke2-security-policy-ipv6-3-ipseclocalout] quit
# 配置名称为ipseclocalin的安全策略规则,使Spoke2可以接收和处理来自其他VAM Clinet的IPsec协商报文,具体配置步骤如下。
[Spoke2-security-policy-ipv6] rule name ipseclocalin
[Spoke2-security-policy-ipv6-4-ipseclocalin] source-zone untrust
[Spoke2-security-policy-ipv6-4-ipseclocalin] destination-zone local
[Spoke2-security-policy-ipv6-4-ipseclocalin] source-ip-range 1::1 1::3
[Spoke2-security-policy-ipv6-4-ipseclocalin] destination-ip-host 1::4
[Spoke2-security-policy-ipv6-4-ipseclocalin] action pass
[Spoke2-security-policy-ipv6-4-ipseclocalin] quit
# 配置名称为ospflocalout的安全策规则,使Spoke2可以向其他VAM Client发送OSPF报文,具体配置步骤如下。
[Spoke2-security-policy-ipv6] rule name ospflocalout
[Spoke2-security-policy-ipv6-5-ospflocalout] source-zone local
[Spoke2-security-policy-ipv6-5-ospflocalout] destination-zone untrust
[Spoke2-security-policy-ipv6-5-ospflocalout] service ospf
[Spoke2-security-policy-ipv6-5-ospflocalout] action pass
[Spoke2-security-policy-ipv6-5-ospflocalout] quit
# 配置名称为ospflocalin的安全策略规则,使Spoke2可以接收和处理来自其他VAM Clinet的OSPF报文,具体配置步骤如下。
[Spoke2-security-policy-ipv6] rule name ospflocalin
[Spoke2-security-policy-ipv6-6-ospflocalin] source-zone untrust
[Spoke2-security-policy-ipv6-6-ospflocalin] destination-zone local
[Spoke2-security-policy-ipv6-6-ospflocalin] service ospf
[Spoke2-security-policy-ipv6-6-ospflocalin] action pass
[Spoke2-security-policy-ipv6-6-ospflocalin] quit
[Spoke2-security-policy-ipv6] quit
配置VAM Client,用于建立ADVPN网络
[Spoke2] vam client name Spoke2
[Spoke2-vam-client-Spoke2] advpn-domain abc
[Spoke2-vam-client-Spoke2] pre-shared-key simple 123456
[Spoke2-vam-client-Spoke2] user spoke2 password simple spoke2
[Spoke2-vam-client-Spoke2] server primary ipv6-address 1::11
[Spoke2-vam-client-Spoke2] server secondary ipv6-address 1::12
[Spoke2-vam-client-Spoke2] client enable
[Spoke2-vam-client-Spoke2] quit
配置IPsec安全框架
# 配置IKE框架。
[Spoke2] ike keychain abc
[Spoke2-ike-keychain-abc] pre-shared-key address ipv6 :: 0 key simple 123456
[Spoke2-ike-keychain-abc] quit
[Spoke2] ike profile abc
[Spoke2-ike-profile-abc] keychain abc
[Spoke2-ike-profile-abc] quit
# 配置IPsec安全框架。
[Spoke2] ipsec transform-set abc
[Spoke2-ipsec-transform-set-abc] encapsulation-mode transport
[Spoke2-ipsec-transform-set-abc] esp encryption-algorithm des-cbc
[Spoke2-ipsec-transform-set-abc] esp authentication-algorithm sha1
[Spoke2-ipsec-transform-set-abc] quit
[Spoke2] ipsec profile abc isakmp
[Spoke2-ipsec-profile-isakmp-abc] transform-set abc
[Spoke2-ipsec-profile-isakmp-abc] ike-profile abc
[Spoke2-ipsec-profile-isakmp-abc] quit
配置OSPFv3路由
# 启动OSPFv3,以发布私网的路由信息。
[Spoke2] ospfv3 1
[Spoke2-ospfv3-1] router-id 0.0.0.4
[Spoke2-ospfv3-1] area 0
[Spoke2-ospfv3-1-area-0.0.0.0] quit
[Spoke2-ospfv3-1] quit
配置ADVPN隧道
# 配置GRE封装的IPv6 ADVPN隧道接口Tunnel1。
[Spoke2] interface tunnel 1
[Spoke2-Tunnel1] vam ipv6 client Spoke2
[Spoke2-Tunnel1] ospfv3 1 area 0
[Spoke2-Tunnel1] ospfv3 network-type p2mp
[Spoke2-Tunnel1] source gigabitethernet 1/0/1
[Spoke2-Tunnel1] tunnel protection ipsec profile abc
[Spoke2-Tunnel1] quit
# 显示注册到主VAM Server的所有VAM Client的IPv6私网地址映射信息。
[PrimaryServer] display vam server ipv6 address-map
ADVPN domain name: abc
Total private address mappings: 4
Group Private address Public address Type NAT Holding time
0 192:168::1 1::1 Hub No 0H 52M 7S
0 192:168::2 1::2 Hub No 0H 47M 31S
0 192:168::3 1::3 Spoke No 0H 28M 25S
0 192:168::4 1::4 Spoke No 0H 19M 15S
# 显示注册到备VAM Server的所有VAM Client的IPv6私网地址映射信息。
[SecondaryServer] display vam server ipv6 address-map
ADVPN domain name: abc
Total private address mappings: 4
Group Private address Public address Type NAT Holding time
0 192:168::1 1::1 Hub No 0H 52M 7S
0 192:168::2 1::2 Hub No 0H 47M 31S
0 192:168::3 1::3 Spoke No 0H 28M 25S
0 192:168::4 1::4 Spoke No 0H 19M 15S
以上显示信息表示Hub1、Hub2、Spoke1和Spoke2均已将地址映射信息注册到VAM Server。
# 显示Hub1上的IPv6 ADVPN隧道信息。
[Hub1] display advpn ipv6 session
Interface : Tunnel1
Number of sessions: 3
Private address Public address Port Type State Holding time
192:168::2 1::2 -- H-H Success 0H 46M 8S
192:168::3 1::3 -- H-S Success 0H 27M 27S
192:168::4 1::4 -- H-S Success 0H 18M 18S
以上显示信息表示Hub1与Hub2、Spoke1、Spoke2建立了永久隧道。Hub2上的显示信息与Hub1类似。
# 显示Spoke1上的IPv6 ADVPN隧道信息。
[Spoke1] display advpn ipv6 session
Interface : Tunnel1
Number of sessions: 2
Private address Public address Port Type State Holding time
192:168::1 1::1 -- S-H Success 0H 46M 8S
192:168::2 1::2 -- S-H Success 0H 46M 8S
以上显示信息表示Spoke1与Hub1、Hub2建立了Hub-Spoke永久隧道。Spoke2上的显示信息与Spoke1类似。
# 在Spoke1上ping Spoke2的私网地址192:168::4。
[Spoke1] ping ipv6 192:168::4
Ping6(56 data bytes) 192:168::4 --> 192:168::4, press CTRL_C to break
56 bytes from 192:168::4, icmp_seq=0 hlim=64 time=3.000 ms
56 bytes from 192:168::4, icmp_seq=1 hlim=64 time=0.000 ms
56 bytes from 192:168::4, icmp_seq=2 hlim=64 time=1.000 ms
56 bytes from 192:168::4, icmp_seq=3 hlim=64 time=1.000 ms
56 bytes from 192:168::4, icmp_seq=4 hlim=64 time=1.000 ms
--- Ping6 statistics for 192:168::4 ---
5 packets transmitted, 5 packets received, 0.0% packet loss
round-trip min/avg/max/std-dev = 0.000/1.200/3.000/0.980 ms
#
interface GigabitEthernet1/0/1
ipv6 address 1::11/64
#
security-zone name Untrust
import interface GigabitEthernet1/0/1
#
radius session-control enable
#
radius scheme abc
primary authentication ipv6 1::10
primary accounting ipv6 1::10
key authentication simple 123
key accounting simple 123
user-name-format without-domain
#
domain abc
authentication advpn radius-scheme abc
accounting advpn radius-scheme abc
#
domain default enable abc
#
vam server advpn-domain abc id 1
pre-shared-key simple 123456
authentication-method chap
server enable
hub-group 0
hub ipv6 private-address 192:168::1
hub ipv6 private-address 192:168::2
spoke ipv6 private-address range 192:168:: 192:168::FFFF:FFFF:FFFF:FFFF
#
security-policy ipv6
rule 0 name advpnlocalout
action pass
source-zone local
destination-zone untrust
source-ip-host 1::11
destination-ip-range 1::1 1::12
rule 1 name advpnlocalin
action pass
source-zone untrust
destination-zone local
source-ip-range 1::1 1::12
destination-ip-host 1::11
#
#
interface GigabitEthernet1/0/1
ipv6 address 1::12/64
#
security-zone name Untrust
import interface GigabitEthernet1/0/1
#
radius session-control enable
#
radius scheme abc
primary authentication ipv6 1::10
primary accounting ipv6 1::10
key authentication simple 123
key accounting simple 123
user-name-format without-domain
#
domain abc
authentication advpn radius-scheme abc
accounting advpn radius-scheme abc
#
domain default enable abc
#
vam server advpn-domain abc id 1
pre-shared-key simple 123456
authentication-method chap
server enable
hub-group 0
hub ipv6 private-address 192:168::1
hub ipv6 private-address 192:168::2
spoke ipv6 private-address range 192:168:: 192:168::FFFF:FFFF:FFFF:FFFF
#
security-policy ipv6
rule 0 name advpnlocalout
action pass
source-zone local
destination-zone untrust
source-ip-host 1::11
destination-ip-range 1::1 1::12
rule 1 name advpnlocalin
action pass
source-zone untrust
destination-zone local
source-ip-range 1::1 1::12
destination-ip-host 1::11
#
#
ospfv3 1
router-id 0.0.0.1
area 0.0.0.0
#
interface GigabitEthernet1/0/1
ipv6 address 1::1/64
#
interface tunnel 1 mode advpn gre ipv6
ospfv3 1 area 0.0.0.0
ospfv3 network-type p2mp
source GigabitEthernet1/0/1
ipv6 address FE80::1 link-local
ipv6 address 192:168::1/64
tunnel protection ipsec profile abc
vam ipv6 client Hub1
#
security-zone name Untrust
import interface GigabitEthernet1/0/1
import interface tunnel 1
#
ipsec transform-set abc
encapsulation-mode transport
esp encryption-algorithm des-cbc
esp authentication-algorithm sha1
#
ipsec profile abc isakmp
transform-set abc
ike-profile abc
#
ike profile abc
keychain abc
#
ike keychain abc
pre-shared-key address ipv6 :: 0 key simple 123456
#
vam client name Hub1
advpn-domain abc
server primary ipv6-address 1::11
server secondary ipv6-address 1::12
pre-shared-key simple 123456
user hub1 password simple hub1
client enable
#
security-policy ip
#
security-policy ipv6
rule 0 name advpnlocalout
action pass
source-zone local
destination-zone untrust
source-ip-host 1::1
destination-ip-range 1::10 1::12
rule 1 name advpnlocalin
action pass
source-zone untrust
destination-zone local
source-ip-range 1::10 1::12
destination-ip-host 1::1
rule 2 name ipseclocalout
action pass
source-zone local
destination-zone untrust
source-ip-host 1::1
destination-ip-range 1::2 1::4
rule 3 name ipseclocalin
action pass
source-zone untrust
destination-zone local
source-ip-range 1::2 1::4
destination-ip-host 1::1
rule 4 name ospflocalout
action pass
source-zone local
destination-zone untrust
service ospf
rule 5 name ospflocalin
action pass
source-zone untrust
destination-zone local
service ospf
#
#
ospfv3 1
router-id 0.0.0.2
area 0.0.0.0
#
interface GigabitEthernet1/0/1
ipv6 address 1::2/64
#
interface tunnel 1 mode advpn gre ipv6
ospfv3 1 area 0.0.0.0
ospfv3 network-type p2mp
source GigabitEthernet1/0/1
ipv6 address FE80::2 link-local
ipv6 address 192:168::2/64
tunnel protection ipsec profile abc
vam ipv6 client Hub2
#
security-zone name Untrust
import interface GigabitEthernet1/0/1
import interface tunnel 1
#
ipsec transform-set abc
encapsulation-mode transport
esp encryption-algorithm des-cbc
esp authentication-algorithm sha1
#
ipsec profile abc isakmp
transform-set abc
ike-profile abc
#
ike profile abc
keychain abc
#
ike keychain abc
pre-shared-key address ipv6 :: 0 key simple 123456
#
vam client name Hub2
advpn-domain abc
server primary ipv6-address 1::11
server secondary ipv6-address 1::12
pre-shared-key simple 123456
user hub2 password simple hub2
client enable
#
security-policy ip
#
security-policy ipv6
rule 0 name advpnlocalout
action pass
source-zone local
destination-zone untrust
source-ip-host 1::2
destination-ip-range 1::10 1::12
rule 1 name advpnlocalin
action pass
source-zone untrust
destination-zone local
source-ip-range 1::10 1::12
destination-ip-host 1::2
rule 2 name ipseclocalout
action pass
source-zone local
destination-zone untrust
source-ip-host 1::2
destination-ip-range 1::1 1::4
rule 3 name ipseclocalin
action pass
source-zone untrust
destination-zone local
source-ip-range 1::1 1::4
destination-ip-host 1::2
rule 4 name ospflocalout
action pass
source-zone local
destination-zone untrust
service ospf
rule 5 name ospflocalin
action pass
source-zone untrust
destination-zone local
service ospf
#
#
ospfv3 1
router-id 0.0.0.3
area 0.0.0.0
#
interface GigabitEthernet1/0/1
ipv6 address 1::3/64
#
interface GigabitEthernet1/0/2
ipv6 address 192:168:1::1/64
#
interface tunnel 1 mode advpn gre ipv6
ospfv3 1 area 0.0.0.0
ospfv3 network-type p2mp
source GigabitEthernet1/0/1
ipv6 address FE80::3 link-local
ipv6 address 192:168::3/64
tunnel protection ipsec profile abc
vam ipv6 client Spoke1
#
security-zone name Trust
import interface GigabitEthernet1/0/2
#
security-zone name Untrust
import interface GigabitEthernet1/0/1
import interface tunnel 1
#
ipsec transform-set abc
encapsulation-mode transport
esp encryption-algorithm des-cbc
esp authentication-algorithm sha1
#
ipsec profile abc isakmp
transform-set abc
ike-profile abc
#
ike profile abc
keychain abc
#
ike keychain abc
pre-shared-key address 0.0.0.0 0.0.0.0 key simple 123456
#
vam client name Spoke1
advpn-domain abc
server primary ipv6-address 1::11
server secondary ipv6-address 1::12
pre-shared-key simple 123456
user spoke1 password simple spoke1
client enable
#
security-policy ip
#
security-policy ipv6
rule 0 name advpnlocalout
action pass
source-zone local
destination-zone untrust
source-ip-host 1::3
destination-ip-range 1::10 1::12
rule 1 name advpnlocalin
action pass
source-zone untrust
destination-zone local
source-ip-range 1::10 1::12
destination-ip-host 1::3
rule 2 name ipseclocalout
action pass
source-zone local
destination-zone untrust
source-ip-host 1::3
destination-ip-range 1::1 1::4
rule 3 name ipseclocalin
action pass
source-zone untrust
destination-zone local
source-ip-range 1::1 1::4
destination-ip-host 1::3
rule 4 name ospflocalout
action pass
source-zone local
destination-zone untrust
service ospf
rule 5 name ospflocalin
action pass
source-zone untrust
destination-zone local
service ospf
#
#
ospfv3 1
router-id 0.0.0.4
area 0.0.0.0
#
interface GigabitEthernet1/0/1
ipv6 address 1::4/64
#
interface GigabitEthernet1/0/2
ipv6 address 192:168:2::1/64
#
interface tunnel 1 mode advpn gre ipv6
ospfv3 1 area 0.0.0.0
ospfv3 network-type p2mp
source GigabitEthernet1/0/1
ipv6 address FE80::4 link-local
ipv6 address 192:168::4/64
tunnel protection ipsec profile abc
vam ipv6 client Spoke2
#
security-zone name Trust
import interface GigabitEthernet1/0/2
#
security-zone name Untrust
import interface GigabitEthernet1/0/1
import interface tunnel 1
#
ipsec transform-set abc
encapsulation-mode transport
esp encryption-algorithm des-cbc
esp authentication-algorithm sha1
#
ipsec profile abc isakmp
transform-set abc
ike-profile abc
#
ike profile abc
keychain abc
#
ike keychain abc
pre-shared-key address 0.0.0.0 0.0.0.0 key simple 123456
#
vam client name Spoke2
advpn-domain abc
server primary ipv6-address 1::11
server secondary ipv6-address 1::12
pre-shared-key simple 123456
user spoke2 password simple spoke2
client enable
#
security-policy ip
#
security-policy ipv6
rule 0 name advpnlocalout
action pass
source-zone local
destination-zone untrust
source-ip-host 1::4
destination-ip-range 1::10 1::12
rule 1 name advpnlocalin
action pass
source-zone untrust
destination-zone local
source-ip-range 1::10 1::12
destination-ip-host 1::4
rule 2 name ipseclocalout
action pass
source-zone local
destination-zone untrust
source-ip-host 1::4
destination-ip-range 1::1 1::3
rule 3 name ipseclocalin
action pass
source-zone untrust
destination-zone local
source-ip-range 1::1 1::3
destination-ip-host 1::4
rule 4 name ospflocalout
action pass
source-zone local
destination-zone untrust
service ospf
rule 5 name ospflocalin
action pass
source-zone untrust
destination-zone local
service ospf