本举例是在F1090的R8660P33版本上进行配置和验证的。
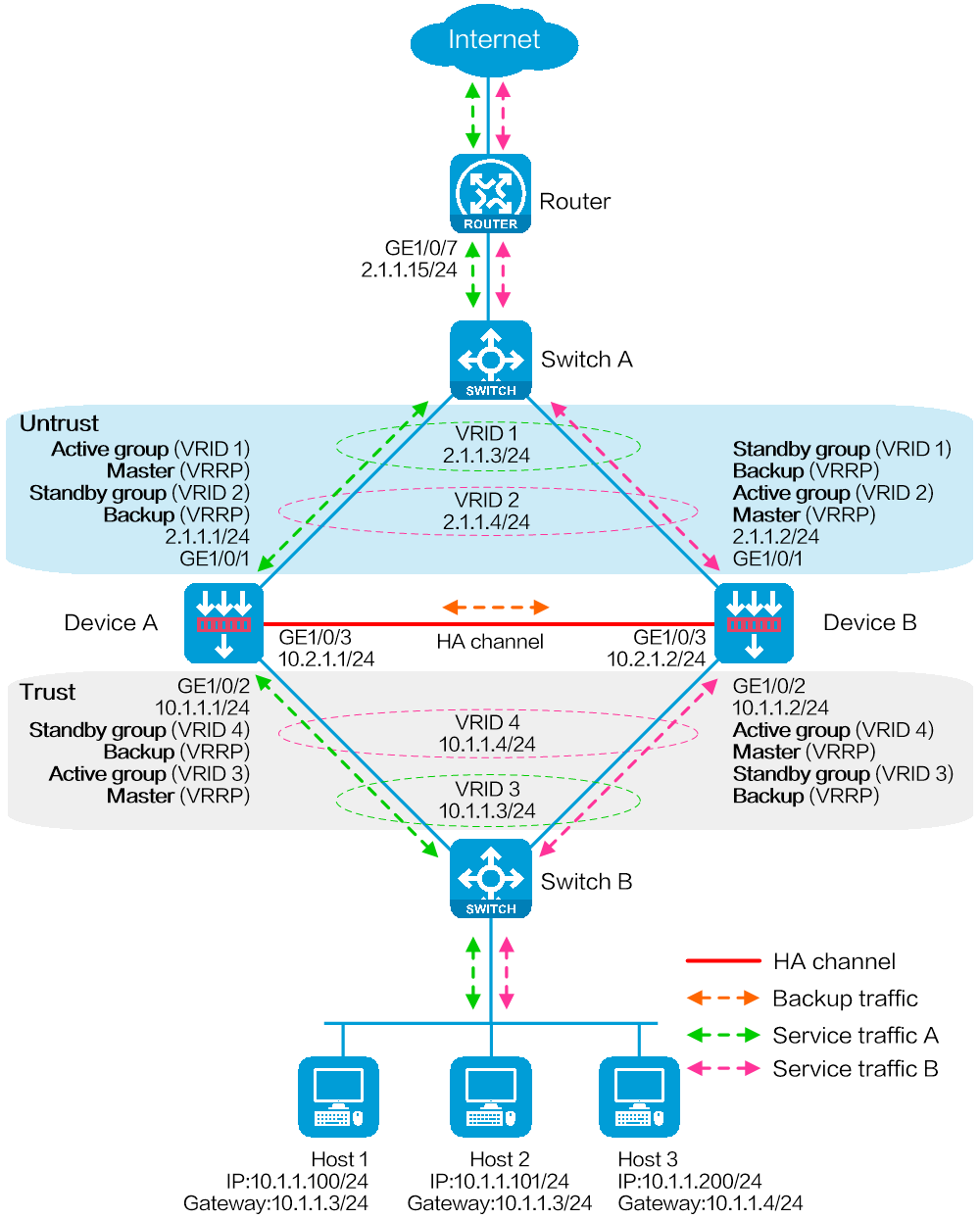
如下图所示,某公司以Device作为网络边界安全防护设备,连接公司内部网络和Internet。为提高业务稳定性,使用两台Device进行HA组网,同时需要两台Device同时处理业务,提高业务处理能力。但是当Device A或其链路发生故障时,Device B可以接替Device A继续工作,保证业务不会中断。同时需要在Device上配置动态NAT功能保证内网用户可以访问Internet,该公司拥有2.1.1.1到2.1.1.10十个外网IPv4地址。
图-1 HA联动VRRP双主模式中接口NAT功能组网图
部署HA前,请先保证主/备设备硬件环境的一致性,具体要求如下:
主/备设备的型号必须一致。
主/备设备上管理接口、业务接口、HA通道接口需要分别使用相互独立的接口,且所使用的接口编号和类型必须一致。
主/备设备上硬盘的位置、数量和类型建议一致。未安装硬盘的设备日志存储量将远低于安装了硬盘的设备,而且部分日志和报表功能不可用。
部署HA前,请先保证主/备设备软件环境的一致性,具体要求如下:
主/备设备的系统软件环境及其版本必须一致,如:Boot包、System包、Feature包和补丁包等等。
主/备设备上被授权的特征库和特性环境必须一致,如:特征库的种类,每类特征库的版本、授权时间范围、授权的资源数等等。
主/备设备的接口编号必须一致。
主/备设备之间建立HA通道的接口类型、速率和编号等信息必须一致,推荐使用聚合接口。
主/备设备上聚合接口的编号、成员接口编号必须一致。
主/备设备相同位置的接口必须加入到相同的安全域。
主/备设备的HASH选择CPU模式以及HASH因子都必须相同(即forwarding policy命令)。
配置接口IPv4地址
# 根据组网图中规划的信息,配置各接口的IPv4地址,具体配置步骤如下。
<Router> system-view
[Router] interface gigabitethernet 1/0/7
[Router-GigabitEthernet1/0/7] ip address 2.1.1.15 255.255.255.0
[Router-GigabitEthernet1/0/7] quit
请参考以上步骤配置其他接口的IP地址,具体配置步骤略。
配置静态路由,保证网络路由可达
本举例仅以静态路由方式配置路由信息。实际组网中,请根据具体情况选择相应的路由配置方式。
# 请根据组网图中规划的信息,配置静态路由。本举例假设去往一部分内网流量(如Host 1)的下一跳IPv4地址为VRRP备份组1的虚拟IPv4地址2.1.1.3,去往另一部分内网流量(如Host 3)的下一跳IPv4地址为VRRP备份组2的虚拟IPv4地址2.1.1.4,去往Internet流量的下一跳IPv4地址为3.1.1.15,实际环境中请以具体组网情况为准,具体配置步骤如下。
[Router] ip route-static 10.1.1.0 255.255.255.128 2.1.1.3
[Router] ip route-static 10.1.1.128 255.255.255.128 2.1.1.4
[Router] ip route-static 0.0.0.0 0.0.0.0 3.1.1.15
在Switch A上创建VLAN 10,并将连接Device A、Device B和Router的接口链路类型设置为Access,并将接口加入VLAN 10。
# 根据组网图中规划的信息,配置各接口加入VLAN,并设置链路类型,具体配置步骤如下。
<SwitchA> system-view
[SwitchA] vlan 10
[SwitchA-vlan10] quit
[SwitchA] interface gigabitethernet 1/0/1
[SwitchA-GigabitEthernet1/0/1] port access vlan 10
[SwitchA-GigabitEthernet1/0/1] quit
[SwitchA] interface gigabitethernet 1/0/2
[SwitchA-GigabitEthernet1/0/2] port access vlan 10
[SwitchA-GigabitEthernet1/0/2] quit
[SwitchA] interface gigabitethernet 1/0/3
[SwitchA-GigabitEthernet1/0/3] port access vlan 10
[SwitchA-GigabitEthernet1/0/3] quit
# 在Switch B上创建VLAN 10,并将连接Device A、Device B和Host的接口设置成工作在二层模式,接口链路类型为Access,并将此接口加入VLAN 10。
# 根据组网图中规划的信息,配置各接口加入VLAN,并设置链路类型,具体配置步骤如下。
<SwitchB> system-view
[SwitchB] vlan 10
[SwitchB-vlan10] quit
[SwitchB] interface gigabitethernet 1/0/1
[SwitchB-GigabitEthernet1/0/1] port access vlan 10
[SwitchB-GigabitEthernet1/0/1] quit
[SwitchB] interface gigabitethernet 1/0/2
[SwitchB-GigabitEthernet1/0/2] port access vlan 10
[SwitchB-GigabitEthernet1/0/2] quit
[SwitchB] interface gigabitethernet 1/0/3
[SwitchB-GigabitEthernet1/0/3] port access vlan 10
[SwitchB-GigabitEthernet1/0/3] quit
配置接口IPv4地址
# 根据组网图中规划的信息,配置各接口的IPv4地址,具体配置步骤如下。
<DeviceA> system-view
[DeviceA] interface gigabitethernet 1/0/1
[DeviceA-GigabitEthernet1/0/1] ip address 2.1.1.1 255.255.255.0
[DeviceA-GigabitEthernet1/0/1] quit
请参考以上步骤配置其他接口的IP地址,具体配置步骤略。
配置接口加入安全域。
# 请根据组网图中规划的信息,将接口加入对应的安全域,具体配置步骤如下。
[DeviceA] security-zone name untrust
[DeviceA-security-zone-Untrust] import interface gigabitethernet 1/0/1
[DeviceA-security-zone-Untrust] quit
[DeviceA] security-zone name trust
[DeviceA-security-zone-Trust] import interface gigabitethernet 1/0/2
[DeviceA-security-zone-Trust] quit
配置静态路由,保证路由可达
本举例仅以静态路由方式配置路由信息。实际组网中,请根据具体情况选择相应的路由配置方式。
# 请根据组网图中规划的信息,配置静态路由使设备与内外网之间路由可达。本举例假设到达外网的下一跳IPv4地址为2.1.1.15,实际环境中请以具体组网情况为准,具体配置步骤如下。
[DeviceA] ip route-static 0.0.0.0 0.0.0.0 2.1.1.15
配置安全策略,允许所需的业务报文通过
此部分安全策略只需在主管理设备配置,HA组网完成后,从管理设备会自动同步这些安全策略配置信息。
# 配置名称为trust-untrust的安全策略规则,使10.1.1.0/24网段的内网用户可以主动访问Internet,但是Internet上的用户不能访问内网,具体配置步骤如下。
[DeviceA] security-policy ip
[DeviceA-security-policy-ip] rule name trust-untrust
[DeviceA-security-policy-ip-0-trust-untrust] source-zone trust
[DeviceA-security-policy-ip-0-trust-untrust] destination-zone untrust
[DeviceA-security-policy-ip-0-trust-untrust] source-ip-subnet 10.1.1.0 24
[DeviceA-security-policy-ip-0-trust-untrust] action pass
[DeviceA-security-policy-ip-0-trust-untrust] quit
# 配置名称为vrrp的安全策略规则,允许VRRP协议报文通过。当HA通道断开时,使Device A与Device B之间可以交换VRRP报文,进行VRRP角色竞选,保证网络互通。
[DeviceA-security-policy-ip] rule name vrrp1
[DeviceA-security-policy-ip-1-vrrp1] source-zone trust
[DeviceA-security-policy-ip-1-vrrp1] destination-zone local
[DeviceA-security-policy-ip-1-vrrp1] service vrrp
[DeviceA-security-policy-ip-1-vrrp1] action pass
[DeviceA-security-policy-ip-1-vrrp1] quit
[DeviceA-security-policy-ip] rule name vrrp2
[DeviceA-security-policy-ip-2-vrrp2] source-zone local
[DeviceA-security-policy-ip-2-vrrp2] destination-zone trust
[DeviceA-security-policy-ip-2-vrrp2] service vrrp
[DeviceA-security-policy-ip-2-vrrp2] action pass
[DeviceA-security-policy-ip-2-vrrp2] quit
[DeviceA-security-policy-ip] rule name vrrp3
[DeviceA-security-policy-ip-3-vrrp3] source-zone untrust
[DeviceA-security-policy-ip-3-vrrp3] destination-zone local
[DeviceA-security-policy-ip-3-vrrp3] service vrrp
[DeviceA-security-policy-ip-3-vrrp3] action pass
[DeviceA-security-policy-ip-3-vrrp3] quit
[DeviceA-security-policy-ip] rule name vrrp4
[DeviceA-security-policy-ip-4-vrrp4] source-zone local
[DeviceA-security-policy-ip-4-vrrp4] destination-zone untrust
[DeviceA-security-policy-ip-4-vrrp4] service vrrp
[DeviceA-security-policy-ip-4-vrrp4] action pass
[DeviceA-security-policy-ip-4-vrrp4] quit
[DeviceA-security-policy-ip] quit
配置高可靠性
本举例仅用以太网接口作为控制通道和数据通道接口使用。对于设备同时拥有HA接口和以太网接口的情况,建议使用HA接口作为控制通道和数据通道接口使用,这样能够更好地保护设备的安全性和稳定性。HA接口不能作为业务接口使用。
# 使用两台Device进行HA组网,需要两台Device同时处理业务,提高业务处理能力。但是当Device A或其链路发生故障时,Device B可以接替Device A继续工作,保证业务不会中断。
[DeviceA] remote-backup group
[DeviceA-remote-backup-group] remote-ip 10.2.1.2
[DeviceA-remote-backup-group] local-ip 10.2.1.1
[DeviceB-remote-backup-group] data-channel interface gigabitethernet 1/0/3
[DeviceA-remote-backup-group] device-role primary
RBM_P[DeviceA-remote-backup-group] backup-mode dual-active
RBM_P[DeviceA-remote-backup-group] hot-backup enable
RBM_P[DeviceA-remote-backup-group] configuration auto-sync enable
RBM_P[DeviceA-remote-backup-group] configuration sync-check interval 12
RBM_P[DeviceA-remote-backup-group] delay-time 1
RBM_P[DeviceA-remote-backup-group] quit
# 配置VRRP备份组,并与HA关联。实现HA对VRRP备份组的统一管理和流量引导。
RBM_P[DeviceA] interface gigabitethernet 1/0/1
RBM_P[DeviceA-GigabitEthernet1/0/1] vrrp vrid 1 virtual-ip 2.1.1.3 active
RBM_P[DeviceA-GigabitEthernet1/0/1] vrrp vrid 2 virtual-ip 2.1.1.4 standby
RBM_P[DeviceA-GigabitEthernet1/0/1] quit
RBM_P[DeviceA] interface gigabitethernet 1/0/2
RBM_P[DeviceA-GigabitEthernet1/0/2] vrrp vrid 3 virtual-ip 10.1.1.3 active
RBM_P[DeviceA-GigabitEthernet1/0/2] vrrp vrid 4 virtual-ip 10.1.1.4 standby
RBM_P[DeviceA-GigabitEthernet1/0/2] quit
配置动态NAT
在此配置举例中,仅需要在主管理设备Device A上配置NAT的相关配置,Device A上的NAT配置会自动同步到从管理设备Device B。
# 配置NAT地址组1,其地址成员范围为2.1.1.5到2.1.1.7,并与VRRP备份组1绑定。
RBM_P<DeviceA> system-view
RBM_P[DeviceA] nat address-group 1
RBM_P[DeviceA-address-group-1] address 2.1.1.5 2.1.1.7
RBM_P[DeviceA-address-group-1] vrrp vrid 1
RBM_P[DeviceA-address-group-1] quit
# 配置NAT地址组2,其地址成员范围为2.1.1.8到2.1.1.10,并与VRRP备份组2绑定。
RBM_P[DeviceA] nat address-group 2
RBM_P[DeviceA-address-group-2] address 2.1.1.8 2.1.1.10
RBM_P[DeviceA-address-group-2] vrrp vrid 2
RBM_P[DeviceA-address-group-2] quit
# 配置ACL 3000,仅允许10.1.1.1/25网段的报文通过;配置ACL 3001,仅允许10.1.1.129/25网段的报文通过。
RBM_P[DeviceA] acl advanced 3000
RBM_P[DeviceA-ipv4-adv-3000] rule permit ip source 10.1.1.1 0.0.0.127
RBM_P[DeviceA-ipv4-adv-3000] quit
RBM_P[DeviceA] acl advanced 3001
RBM_P[DeviceA-ipv4-adv-3001] rule permit ip source 10.1.1.129 0.0.0.127
RBM_P[DeviceA-ipv4-adv-3001] quit
# 在接口上配置出方向动态地址转换,允许使用地址组1中的IPv4地址对匹配ACL 3000的报文进行源地址转换,并在转换过程中使用端口信息;允许使用地址组2中的IPv4地址对匹配ACL 3001的报文进行源地址转换,并在转换过程中使用端口信息。
RBM_P[DeviceA] interface gigabitethernet 1/0/1
RBM_P[DeviceA-GigabitEthernet1/0/1] nat outbound 3000 address-group 1
RBM_P[DeviceA-GigabitEthernet1/0/1] nat outbound 3001 address-group 2
RBM_P[DeviceA-GigabitEthernet1/0/1] quit
配置安全业务
# 以上有关HA的配置部署完成后,可以配置各种安全业务。对于HA支持配置信息备份的功能模块仅需要在此主管理设备上(Device A)进行配置即可。
配置接口IPv4地址
# 根据组网图中规划的信息,配置各接口的IPv4地址,具体配置步骤如下。
<DeviceB> system-view
[DeviceB] interface gigabitethernet 1/0/1
[DeviceB-GigabitEthernet1/0/1] ip address 2.1.1.2 255.255.255.0
[DeviceB-GigabitEthernet1/0/1] quit
请参考以上步骤配置其他接口的IP地址,具体配置步骤略。
配置接口加入安全域。
# 请根据组网图中规划的信息,将接口加入对应的安全域,具体配置步骤如下。
[DeviceB] security-zone name untrust
[DeviceB-security-zone-Untrust] import interface gigabitethernet 1/0/1
[DeviceB-security-zone-Untrust] quit
[DeviceB] security-zone name trust
[DeviceB-security-zone-Trust] import interface gigabitethernet 1/0/2
[DeviceB-security-zone-Trust] quit
配置静态路由,保证路由可达
本举例仅以静态路由方式配置路由信息。实际组网中,请根据具体情况选择相应的路由配置方式。
# 请根据组网图中规划的信息,配置静态路由使设备与内外网之间路由可达。本举例假设到达外网的下一跳IPv4地址为2.1.1.15,实际环境中请以具体组网情况为准,具体配置步骤如下。
[DeviceB] ip route-static 0.0.0.0 0.0.0.0 2.1.1.15
配置高可靠性
本举例仅用以太网接口作为控制通道和数据通道接口使用。对于设备同时拥有HA接口和以太网接口的情况,建议使用HA接口作为控制通道和数据通道接口使用,这样能够更好地保护设备的安全性和稳定性。HA接口不能作为业务接口使用。
# 使用两台Device进行HA组网,需要两台Device同时处理业务,提高业务处理能力。但是当Device A或其链路发生故障时,Device B可以接替Device A继续工作,保证业务不会中断。
[DeviceB] remote-backup group
[DeviceB-remote-backup-group] remote-ip 10.2.1.1
[DeviceB-remote-backup-group] local-ip 10.2.1.2
[DeviceB-remote-backup-group] data-channel interface gigabitethernet 1/0/3
[DeviceB-remote-backup-group] device-role secondary
RBM_S[DeviceB-remote-backup-group] backup-mode dual-active
RBM_S[DeviceB-remote-backup-group] hot-backup enable
RBM_S[DeviceB-remote-backup-group] configuration auto-sync enable
RBM_S[DeviceB-remote-backup-group] configuration sync-check interval 12
RBM_S[DeviceB-remote-backup-group] delay-time 1
RBM_S[DeviceB-remote-backup-group] quit
# 配置VRRP备份组,并与HA关联。实现HA对VRRP备份组的统一管理和流量引导。
RBM_S[DeviceB] interface gigabitethernet 1/0/1
RBM_S[DeviceB-GigabitEthernet1/0/1] vrrp vrid 1 virtual-ip 2.1.1.3 standby
RBM_S[DeviceB-GigabitEthernet1/0/1] vrrp vrid 2 virtual-ip 2.1.1.4 active
RBM_S[DeviceB-GigabitEthernet1/0/1] quit
RBM_S[DeviceB] interface gigabitethernet 1/0/2
RBM_S[DeviceB-GigabitEthernet1/0/2] vrrp vrid 3 virtual-ip 10.1.1.3 standby
RBM_S[DeviceB-GigabitEthernet1/0/2] vrrp vrid 4 virtual-ip 10.1.1.4 active
RBM_S[DeviceB-GigabitEthernet1/0/2] quit
# 配置一部分Host(如Host 1)的默认网关为VRRP备份组3的虚拟IPv4地址10.1.1.3,配置另一部分Host(如Host 3)的默认网关为VRRP备份组4的虚拟IPv4地址10.1.1.4。
# 以上配置完成后,内网主机Host 1能够通过Device A访问Internet。在Device A设备上查看如下显示信息,可以看到内网主机访问外网时生成的NAT会话信息。
RBM_P[DeviceA] display nat session verbose
Slot 1:
Initiator:
Source IP/port: 10.1.1.100/52082
Destination IP/port: 202.38.1.10/80
DS-Lite tunnel peer: -
VPN instance/VLAN ID/Inline ID: -/-/-
Protocol: TCP(6)
Inbound interface: GigabitEthernet1/0/2
Source security zone: Trust
Responder:
Source IP/port: 202.38.1.10/80
Destination IP/port: 2.1.1.5/1036
DS-Lite tunnel peer: -
VPN instance/VLAN ID/Inline ID: -/-/-
Protocol: TCP(6)
Inbound interface: GigabitEthernet1/0/1
Source security zone: Untrust
State: TCP_ESTABLISHED
Application: HTTP
Rule ID: 2
Rule name: 3
Start time: 2019-1-29 16:16:59 TTL: 9995s
Initiator->Responder: 551 packets 32547 bytes
Responder->Initiator: 956 packets 1385514 bytes
Total sessions found: 1
# 以上配置完成后,内网主机Host 3能够通过Device B访问Internet。在Device B设备上查看如下显示信息,可以看到内网主机访问外网时生成的NAT会话信息。
RBM_S[DeviceB] display nat session verbose
Slot 1:
Initiator:
Source IP/port: 10.1.1.200/52082
Destination IP/port: 202.38.1.10/80
DS-Lite tunnel peer: -
VPN instance/VLAN ID/Inline ID: -/-/-
Protocol: TCP(6)
Inbound interface:
Source security zone: Trust
Responder:
Source IP/port: 202.38.1.10/80
Destination IP/port: 2.1.1.8/1036
DS-Lite tunnel peer: -
VPN instance/VLAN ID/Inline ID: -/-/-
Protocol: TCP(6)
Inbound interface:
Source security zone: Untrust
State: TCP_ESTABLISHED
Application: HTTP
Rule ID: 2
Rule name: 3
Start time: 2019-1-29 16:17:59 TTL: 9995s
Initiator->Responder: 551 packets 32547 bytes
Responder->Initiator: 956 packets 1385514 bytes
Total sessions found: 1
Router
#
interface GigabitEthernet1/0/7
port link-mode route
ip address 2.1.1.15 255.255.255.0
#
interface GigabitEthernet1/0/8
port link-mode route
ip address 3.1.1.14 255.255.255.0
#
ip route-static 0.0.0.0 0 3.1.1.15
ip route-static 10.1.1.0 25 2.1.1.3
ip route-static 10.1.1.128 25 2.1.1.4
SwitchA
#
vlan 10
#
interface GigabitEthernet1/0/1
port access vlan 10
#
interface GigabitEthernet1/0/2
port access vlan 10
#
interface GigabitEthernet1/0/3
port access vlan 10
SwitchB
#
vlan 10
#
interface GigabitEthernet1/0/1
port access vlan 10
#
interface GigabitEthernet1/0/2
port access vlan 10
#
interface GigabitEthernet1/0/3
port access vlan 10
DeviceA
#
nat address-group 1
address 2.1.1.5 2.1.1.7
vrrp vrid 1
#
nat address-group 2
address 2.1.1.8 2.1.1.10
vrrp vrid 2
#
interface GigabitEthernet1/0/1
port link-mode route
ip address 2.1.1.1 255.255.255.0
vrrp vrid 1 virtual-ip 2.1.1.3 active
vrrp vrid 2 virtual-ip 2.1.1.4 standby
nat outbound 3001 address-group 2
nat outbound 3000 address-group 1
#
interface GigabitEthernet1/0/2
port link-mode route
ip address 10.1.1.1 255.255.255.0
vrrp vrid 3 virtual-ip 10.1.1.3 active
vrrp vrid 4 virtual-ip 10.1.1.4 standby
#
interface GigabitEthernet1/0/3
port link-mode route
ip address 10.2.1.1 255.255.255.0
#
security-zone name Trust
import interface GigabitEthernet1/0/2
#
security-zone name Untrust
import interface GigabitEthernet1/0/1
#
ip route-static 0.0.0.0 0 2.1.1.15
#
acl advanced 3000
rule 0 permit ip source 10.1.1.0 0.0.0.127
#
acl advanced 3001
rule 0 permit ip source 10.1.1.128 0.0.0.127
#
security-policy ip
rule 0 name trust-untrust
action pass
source-zone trust
destination-zone untrust
source-ip-subnet 10.1.1.0 255.255.255.0
rule 1 name vrrp1
action pass
source-zone trust
destination-zone local
service vrrp
rule 2 name vrrp2
action pass
source-zone local
destination-zone trust
service vrrp
rule 3 name vrrp3
action pass
source-zone untrust
destination-zone local
service vrrp
rule 4 name vrrp4
action pass
source-zone local
destination-zone untrust
service vrrp
#
remote-backup group
backup-mode dual-active
data-channel interface GigabitEthernet1/0/3
configuration sync-check interval 12
delay-time 1
local-ip 10.2.1.1
remote-ip 10.2.1.2
device-role primary
#
DeviceB
#
interface GigabitEthernet1/0/1
port link-mode route
ip address 2.1.1.2 255.255.255.0
vrrp vrid 1 virtual-ip 2.1.1.3 standby
vrrp vrid 2 virtual-ip 2.1.1.4 active
#
interface GigabitEthernet1/0/2
port link-mode route
ip address 10.1.1.2 255.255.255.0
vrrp vrid 3 virtual-ip 10.1.1.3 standby
vrrp vrid 4 virtual-ip 10.1.1.4 active
#
interface GigabitEthernet1/0/3
port link-mode route
ip address 10.2.1.2 255.255.255.0
#
security-zone name Trust
import interface GigabitEthernet1/0/2
#
security-zone name Untrust
import interface GigabitEthernet1/0/1
#
ip route-static 0.0.0.0 0 2.1.1.15
#
remote-backup group
data-channel interface GigabitEthernet1/0/3
configuration sync-check interval 12
local-ip 10.2.1.2
remote-ip 10.2.1.1