本举例是在F1090的R8660P33版本上进行配置和验证的。
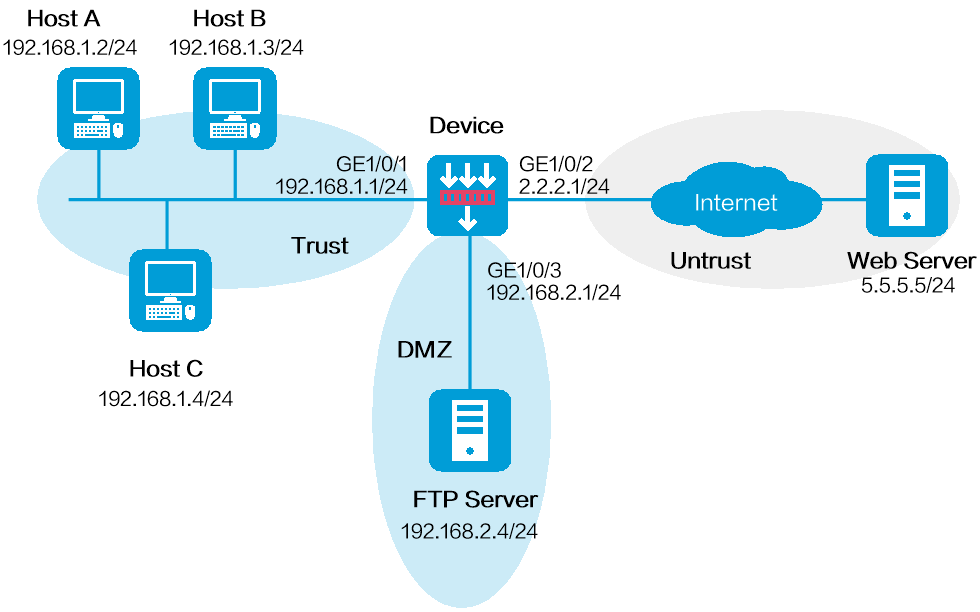
如下图所示,位于Trust安全域的局域网用户通过Device可以访问Untrust安全域的Internet资源,以及DMZ安全域的FTP服务器。FTP服务器根目录下保存了最新的IPS特征库文件ips-1.0.8-encrypt.dat,FTP服务器的登录用户名和密码分别为ips和123。现需要手动离线升级IPS特征库,加载最新的IPS特征。
图-1 手动离线升级IPS特征库配置组网图
配置接口IP地址
# 根据组网图中规划的信息,配置各接口的IP地址,具体配置步骤如下。
<Device> system-view
[Device] interface gigabitethernet 1/0/1
[Device-GigabitEthernet1/0/1] ip address 192.168.1.1 255.255.255.0
[Device-GigabitEthernet1/0/1] quit
请参考以上步骤配置其他接口的IP地址,具体配置步骤略。
配置静态路由
本举例仅以静态路由方式配置路由信息。实际组网中,请根据具体情况选择相应的路由配置方式。
# 请根据组网图中规划的信息,配置静态路由,本举例假设到达外网Web Server的下一跳IP地址为2.2.2.2,实际使用中请以具体组网情况为准,具体配置步骤如下。
[Device] ip route-static 5.5.5.0 24 2.2.2.2
配置接口加入安全域
# 请根据组网图中规划的信息,将接口加入对应的安全域,具体配置步骤如下。
[Device] security-zone name trust
[Device-security-zone-Trust] import interface gigabitethernet 1/0/1
[Device-security-zone-Trust] quit
[Device] security-zone name untrust
[Device-security-zone-Untrust] import interface gigabitethernet 1/0/2
[Device-security-zone-Untrust] quit
[Device] security-zone name dmz
[Device-security-zone-DMZ] import interface gigabitethernet 1/0/3
[Device-security-zone-DMZ] quit
配置安全策略
配置安全策略规则放行Trust到Untrust安全域的流量,使内网用户可以访问外网资源
[Device] security-policy ip
[Device-security-policy-ip] rule name trust-untrust
[Device-security-policy-ip-10-trust-untrust] source-zone trust
[Device-security-policy-ip-10-trust-untrust] source-ip-subnet 192.168.1.0 24
[Device-security-policy-ip-10-trust-untrust] destination-zone untrust
[Device-security-policy-ip-10-trust-untrust] action pass
[Device-security-policy-ip-10-trust-untrust] quit
配置安全策略规则放行Trust到DMZ安全域的流量,使内网用户可以访问DMZ安全域中的服务器
[Device] security-policy ip
[Device-security-policy-ip] rule name trust-dmz
[Device-security-policy-ip-11-trust-dmz] source-zone trust
[Device-security-policy-ip-11-trust-dmz] source-ip-subnet 192.168.1.0 24
[Device-security-policy-ip-11-trust-dmz] destination-zone dmz
[Device-security-policy-ip-11-trust-dmz] action pass
[Device-security-policy-ip-11-trust-dmz] quit
配置安全策略规则放行设备与FTP服务器之间的流量,使设备可以访问FTP服务器,获取特征库文件
[Device] security-policy ip
[Device-security-policy-ip] rule name ftplocalout
[Device-security-policy-ip-12-ftplocalout] source-zone local
[Device-security-policy-ip-12-ftplocalout] destination-zone dmz
[Device-security-policy-ip-12-ftplocalout] destination-ip-subnet 192.168.2.0 24
[Device-security-policy-ip-12-ftplocalout] application ftp
[Device-security-policy-ip-12-ftplocalout] application ftp-data
[Device-security-policy-ip-12-ftplocalout] action pass
[Device-security-policy-ip-12-ftplocalout] quit
# 激活安全策略配置。
[Device-security-policy-ip] accelerate enhanced enable
[Device-security-policy-ip] quit
手动升级IPS特征库
# 采用FTP方式手动离线升级设备上的IPS特征库,且被加载的IPS特征库文件名为ips-1.0.8-encrypt.dat。
[Device] ips signature update ftp://ips:[email protected]/ips-1.0.8-encrypt.dat
IPS特征库升级后,可以通过display ips signature library命令查看当前特征库的版本信息。
#
interface GigabitEthernet1/0/1
port link-mode route
ip address 192.168.1.1 255.255.255.0
#
interface GigabitEthernet1/0/2
port link-mode route
ip address 2.2.2.1 255.255.255.0
#
interface GigabitEthernet1/0/3
port link-mode route
ip address 192.168.2.1 255.255.255.0
#
security-zone name Trust
import interface GigabitEthernet1/0/1
#
security-zone name DMZ
import interface GigabitEthernet1/0/3
#
security-zone name Untrust
import interface GigabitEthernet1/0/2
#
ip route-static 5.5.5.0 24 2.2.2.2
#
security-policy ip
rule 10 name trust-untrust
action pass
source-zone trust
destination-zone untrust
source-ip-subnet 192.168.1.0 255.255.255.0
rule 11 name trust-dmz
action pass
source-zone trust
destination-zone dmz
source-ip-subnet 192.168.1.0 255.255.255.0
rule 12 name ftplocalout
action pass
source-zone local
destination-zone dmz
destination-ip-subnet 192.168.2.0 255.255.255.0
application ftp
application ftp-data