本举例是在F1090的R8660P33版本上进行配置和验证的。
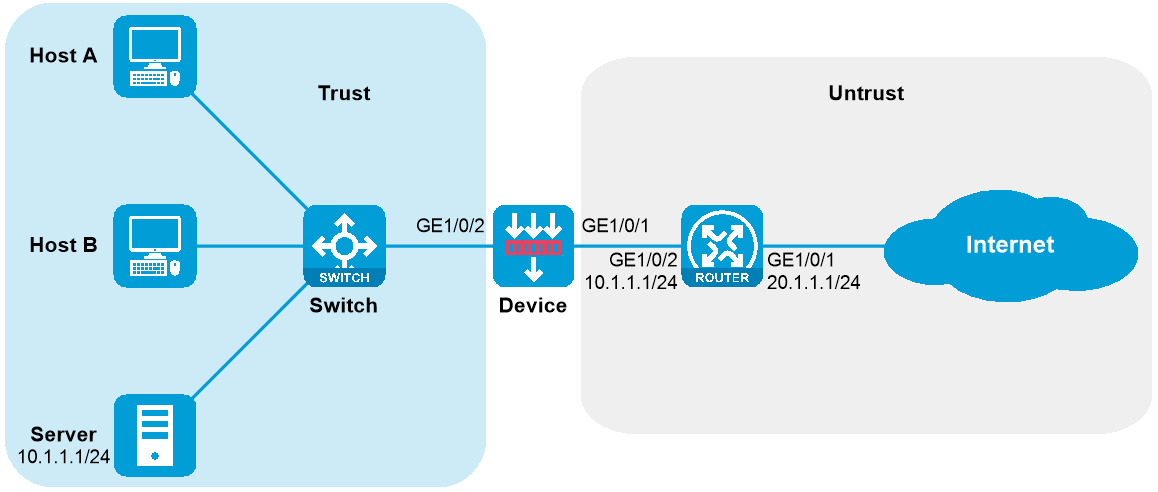
如下图所示,Host A、Host B和Server通过接入交换机Switch、Device和路由器Router与Internet通信,应用需求如下:
Switch和Device透传Host、Server与Internet之间的流量。
Router做Host A、Host B和Server的网关,查路由表转发Host、Server与Internet之间的流量。
Router作为Host的DHCP服务器,为Host动态分配网段为10.1.1.0/24的IP地址,DNS服务器地址为20.1.1.15,网关地址为10.1.1.1。
Router拥有20.1.1.1/24和20.1.1.2/24两个外网IP地址,内部网络中10.1.1.0/24网段的Host使用20.1.1.2/24地址访问Internet。
Server的内网IP地址是10.1.1.2,Server使用外网IP地址20.1.1.2的21端口对Internet提供FTP服务。
Device通过安全策略控制匹配的报文进行转发,对不匹配的报文丢弃处理。
图-1 Device透明直路部署组网图
配置接口的工作模式
# 切换GigabitEthernet1/0/1和GigabitEthernet1/0/2的工作模式为二层。
<Device> system-view
[Device] interface range gigabitethernet 1/0/1 gigabitethernet 1/0/2
[Device-if-range] port link-mode bridge
[Device-if-range] quit
配置接口加入安全域
# 将GigabitEthernet1/0/1的VLAN1加入安全域Untrust,GigabitEthernet1/0/2的VLAN1加入安全域Trust。
[Device] security-zone name untrust
[Device-security-zone-Untrust] import interface gigabitethernet 1/0/1 vlan 1
[Device-security-zone-Untrust] quit
[Device] security-zone name trust
[Device-security-zone-Trust] import interface gigabitethernet 1/0/2 vlan 1
[Device-security-zone-Trust] quit
配置安全策略
# 配置安全策略允许trust安全域访问untrust安全域。
[Device] security-policy ip
[Device-security-policy-ip] rule name trust-untrust
[Device-security-policy-ip-0-trust-untrust] action pass
[Device-security-policy-ip-0-trust-untrust] source-zone trust
[Device-security-policy-ip-0-trust-untrust] destination-zone untrust
[Device-security-policy-ip-0-trust-untrust] quit
# 配置安全策略允许untrust安全域访问trust安全域。
[Device-security-policy-ip] rule name untrust-trust
[Device-security-policy-ip-1-untrust-trust] action pass
[Device-security-policy-ip-1-untrust-trust] source-zone untrust
[Device-security-policy-ip-1-untrust-trust] destination-zone trust
[Device-security-policy-ip-1-untrust-trust] quit
[Device-security-policy-ip] quit
配置接口IP
# 配置接口GigabitEthernet1/0/1和GigabitEthernet1/0/2的IP地址。
<Router> system-view
[Router] interface gigabitethernet 1/0/1
[Router-GigabitEthernet1/0/1] ip address 20.1.1.1 24
[Router-GigabitEthernet1/0/1] quit
[Router] interface gigabitethernet 1/0/2
[Router-GigabitEthernet1/0/2] ip address 10.1.1.1 24
[Router-GigabitEthernet1/0/2] quit
配置静态路由
# 配置默认路由指导上行流量转发(此处下一跳以20.1.1.3为例,请以实际情况为准)。
[Router] ip route-static 0.0.0.0 0 20.1.1.3
配置DHCP服务
# 配置DHCP地址池1,用来为10.1.1.0/24网段内的客户端分配IP地址和网络配置参数。
[Router] dhcp server ip-pool 1
[Router-dhcp-pool-1] network 10.1.1.0 24
[Router-dhcp-pool-1] gateway-list 10.1.1.1
[Router-dhcp-pool-1] dns-list 20.1.1.15
[Router-dhcp-pool-1] forbidden-ip 10.1.1.2
[Router-dhcp-pool-1] quit
# 开启DHCP服务。
[Router] dhcp enable
配置NAT服务
# 配置地址组0,包含外网地址20.1.1.2。
[Router] nat address-group 0
[Router-address-group-0] address 20.1.1.2 20.1.1.2
[Router-address-group-0] quit
# 配置ACL 2000,仅允许对内部网络中10.1.1.0/24网段的用户报文进行地址转换。
[Router] acl basic 2000
[Router-acl-ipv4-basic-2000] rule permit source 10.1.1.0 0.0.0.255
[Router-acl-ipv4-basic-2000] quit
# 在接口GigabitEthernet1/0/1上配置出方向动态地址转换,允许使用地址组0中的地址对匹配ACL 2000的报文进行源地址转换,并在转换过程中使用端口信息。
[Router] interface gigabitethernet 1/0/1
[Router-GigabitEthernet1/0/1] nat outbound 2000 address-group 0
# 配置内部FTP服务器,允许外网主机使用地址20.1.1.2、端口号21访问内网10.1.1.2的FTP服务器。
[Router-GigabitEthernet1/0/1] nat server protocol tcp global 20.1.1.2 21 inside 10.1.1.2 ftp
[Router-GigabitEthernet1/0/1] quit
# Host A、Host B上ping测试Internet的连通性,可以ping通Internet地址20.1.1.3。
C:\>ping 20.1.1.3
Pinging 20.1.1.3 with 32 bytes of data:
Reply from 20.1.1.3: bytes=32 time=3ms TTL=254
Reply from 20.1.1.3: bytes=32 time=2ms TTL=254
Reply from 20.1.1.3: bytes=32 time=1ms TTL=254
Reply from 20.1.1.3: bytes=32 time=2ms TTL=254
Ping statistics for 20.1.1.3:
Packets: Sent = 4, Received = 4, Lost = 0 (0% loss),
Approximate round trip times in milli-seconds:
Minimum = 1ms, Maximum = 3ms, Average = 2ms
# 在Device上检查会话表,存在Host与20.1.1.3的会话表。
[Device]display session table ipv4
Slot 1:
Initiator:
Source IP/port: 10.1.1.6/240
Destination IP/port: 20.1.1.3/2048
DS-Lite tunnel peer: -
VPN instance/VLAN ID/Inline ID: -/1/-
Protocol: ICMP(1)
Inbound interface: GigabitEthernet1/0/2
Source security zone: Trust
Initiator:
Source IP/port: 10.1.1.7/237
Destination IP/port: 20.1.1.3/2048
DS-Lite tunnel peer: -
VPN instance/VLAN ID/Inline ID: -/1/-
Protocol: ICMP(1)
Inbound interface: GigabitEthernet1/0/2
Source security zone: Trust
Total sessions found: 3
# 在Router上检查NAT会话的简要信息。
[Router]display nat session brief
Slot 1:
Protocol Source IP/port Destination IP/port Global IP/port
ICMP 10.1.1.6/229 20.1.1.3/2048 20.1.1.2/0
ICMP 10.1.1.7/229 20.1.1.3/2048 20.1.1.2/0
Total sessions found: 3
#
interface GigabitEthernet1/0/1
port link-mode bridge
#
interface GigabitEthernet1/0/2
port link-mode bridge
#
security-zone name Trust
import interface GigabitEthernet1/0/2 vlan 1
#
security-zone name Untrust
import interface GigabitEthernet1/0/1 vlan 1
#
security-policy ip
rule 0 name trust-untrust
action pass
source-zone trust
destination-zone untrust
rule 1 name untrust-trust
action pass
source-zone untrust
destination-zone trust
#
#
nat address-group 0
address 20.1.1.2 20.1.1.2
#
dhcp enable
#
dhcp server ip-pool 1
gateway-list 10.1.1.1
network 10.1.1.0 mask 255.255.255.0
dns-list 20.1.1.15
forbidden-ip 10.1.1.2
#
#
interface GigabitEthernet1/0/1
ip address 20.1.1.1 255.255.255.0
nat outbound 2000 address-group 0
nat server protocol tcp global 20.1.1.2 21 inside 10.1.1.2 21
#
interface GigabitEthernet1/0/2
ip address 10.1.1.1 255.255.255.0
#
ip route-static 0.0.0.0 0 20.1.1.3
#
acl basic 2000
rule 0 permit source 10.1.1.0 0.0.0.255