Create a virtual firewall
On the top navigation bar, click System, and then select Security Management > Virtual Firewalls from the navigation pane.
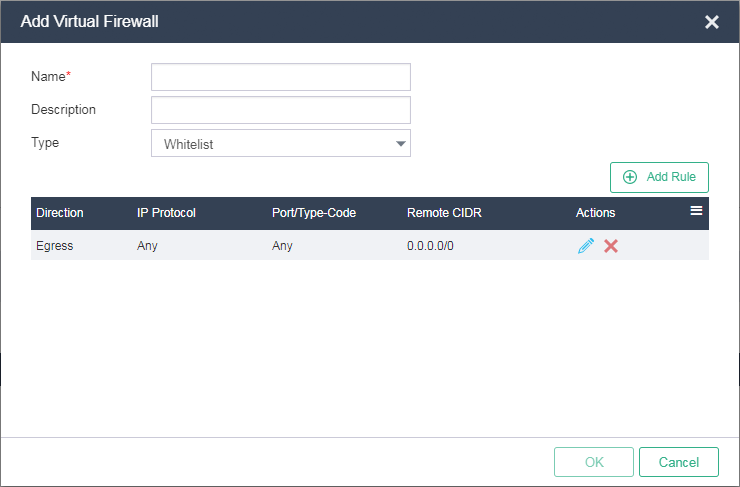
Click Add. In the dialog box that opens, enter the virtual firewall name and select a virtual firewall type.
Figure-1 Creating a virtual firewall
|
Parameter |
Description |
|
Type |
Select a virtual firewall type. Options include Whitelist and Blacklist. Packets that match the rules of a whitelist virtual firewall are permitted and other packets are dropped. Packets that match the rules of a blacklist virtual firewall are dropped and other packets are permitted.
|
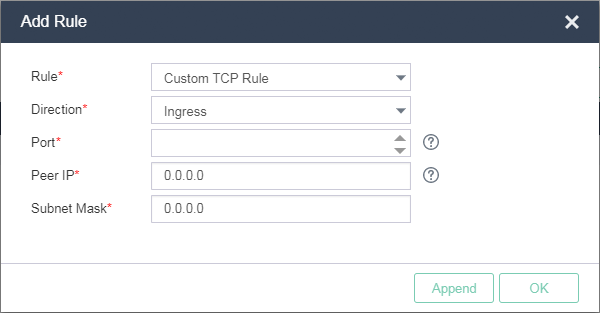
On the page for adding a firewall, click Add Rule. In the dialog box that opens, select a rule type and direction, specify a port, peer IP address and subnet mask, and then click OK.
Figure-2 Adding a rule
|
Parameter |
Description |
|
Direction |
Specify the direction of connections that the rule applies to. Ingress indicates connections initiated by a remote site. Egress indicates connections initiated by a VM. |
|
Port |
Specify a port number. If the direction is ingress, the port number is the VM port that the remote site visits. If the direction is egress, the port number is the remote site port that VMs visit. This parameter is required if Custom TCP Rule or Custom UDP Rule is selected. |
|
Type |
Select an ICMP packet type. This parameter is required if Custom ICMP Rule is selected. |
|
Code |
Select an ICMP code. This parameter is required if Custom ICMP Rule is selected. |
|
IP Protocol |
Select a protocol for which the virtual firewall implements traffic control. This parameter is required if Other Rule is selected. |
|
IP Type |
Select an IP version. This parameter is required if VM IPv6 address management is enabled. |
|
Peer IP |
Enter an IPv4 or IPv6 address of the remote site. If you do not enter an IP address, the rule matches any IP address. |
|
Subnet Mask/Network Prefix |
Enter the subnet mask for the IPv4 remote site address or network prefix for the IPv6 remote site address. For example, if the peer IP address is 172.20.190.202, and the subnet mask is 255.255.255.0, the rule matches all remote sites in the 172.20.190.0 segment. |