- Table of Contents
-
- 10-Security Configuration Guide
- 00-Preface
- 01-AAA Configuration
- 02-802.1X Configuration
- 03-MAC Authentication Configuration
- 04-Portal Configuration
- 05-Password Control Configuration
- 06-Public Key Configuration
- 07-IPsec Configuration
- 08-SSH Configuration
- 09-Packet-Filter Firewall Configuration
- 10-ALG Configuration
- 11-Session Management Configuration
- 12-TCP and ICMP Attack Protection Configuration
- 13-IP Source Guard Configuration
- 14-ARP Attack Protection Configuration
- 15-URPF Configuration
- 16-COPS Configuration
- 17-FIPS Configuration
- 18-PKI Configuration
- Related Documents
-
| Title | Size | Download |
|---|---|---|
| 15-URPF Configuration | 108.54 KB |
Contents
|
|
NOTE: In this documentation, SPC cards refer to the interface cards prefixed with SPC, for example, SPC-GT48L. |
URPF overview
Basic concepts
Unicast Reverse Path Forwarding (URPF) protects a network against attacks based on source address spoofing.
Attackers launch attacks by creating a series of packets with forged source addresses. For applications using IP-address-based authentication, this type of attacks allows unauthorized users to access the system in the name of authorized users, or even access the system as the administrator. Even if the attackers cannot receive any response packets, the attacks are still disruptive to the attacked target.
Figure 1 Attack based on source address spoofing
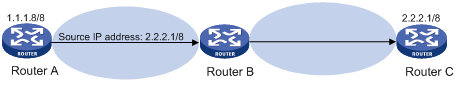
As shown in Figure 1, Router A originates a request to the server (Router B) by sending a packet with a forged source IP address 2.2.2.1/8, and Router B sends a packet to the real IP address 2.2.2.1/8 in response to the request. This type of illegal packets will attack Router B and Router C.
URPF can prevent attacks based on source address spoofing.
How URPF works
URPF provides two check modes: strict and loose. In addition, it supports default route check.
URPF works as follows:
1. First, URPF checks the source address validity, and then:
¡ Discards packets with broadcast source addresses.
¡ Discards packets with all-zero source addresses but non-broadcast destination addresses. (A packet with source address 0.0.0.0 and destination address 255.255.255.255 might be a DHCP or BOOTP packet, and thus is not discarded.)
2. If the source address of an incoming packet is found in the FIB table:
¡ In strict approach, URPF does a reverse route lookup for routes to the source address of the packet. If at least one outgoing interface of such a route matches the receiving interface, the packet passes the check. Otherwise, the packet is rejected.
¡ In loose approach, the packet passes the check.
3. If the source address is not found in the FIB table, URPF makes a decision based on the default route and the allow-default-route keyword.
¡ If no default route is available, the packet is rejected no matter which check approach is taken.
¡ If a default route is available but the allow-default-route keyword is not configured, the packet is rejected no matter which check approach is taken.
¡ If both a default route and the allow-default-route keyword are configured, URPF’s decision depends on the check approach. In strict approach, URPF lets the packet pass if the outgoing interface of the default route is the receiving interface, and otherwise rejects it. In loose approach, URPF lets the packet pass directly.
Configuring URPF
To configure URPF:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter interface view. |
interface interface-type interface-number |
N/A |
|
3. Enable URPF check. |
ip urpf { loose | strict } [ allow-default-route ] |
Disabled by default. The loose and allow-default-route keywords are supported only in SPE mode. For more information about the system working mode, see Fundamentals Configuration Guide. |
|
|
NOTE: · Strict URPF check is effective only on the VLAN interfaces of an SPC card. · URPF only checks packets received on an interface. · In SPE working mode, IPv6 URPF automatically takes effect after URPF is enabled. |
URPF configuration example
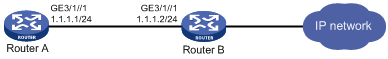
Network requirements
As shown in Figure 2, a client (Router A) directly connects to the ISP router (Router B). Enable strict URPF check on GigabitEthernet 3/1/1 of Router B. Enable strict URPF check on GigabitEthernet 3/1/1 of Router A and allow use of the default route for URPF check.
Configuration procedure
1. Configure Router B:
# Specify the IP address for GigabitEthernet 3/1/1.
<RouterB> system-view
[RouterB] interface GigabitEthernet 3/1/1
[RouterB-GigabitEthernet3/1/1] ip address 1.1.1.2 255.255.255.0
# Enable strict URPF check on GigabitEthernet 3/1/1.
[RouterB-GigabitEthernet3/1/1] ip urpf strict
2. Configure Router A:
# Specify the IP address for GigabitEthernet 3/1/1.
<RouterA> system-view
[RouterA] interface GigabitEthernet 3/1/1
[RouterA-GigabitEthernet3/1/1] ip address 1.1.1.1 255.255.255.0
# Enable strict URPF check on GigabitEthernet 3/1/1 and allow use of the default route for URPF check.
[RouterA-GigabitEthernet3/1/1] ip urpf strict allow-default-route

